- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Site to Site VPN with Full Internet tunnel one Site has a static I
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 02:18 AM - edited 01-23-2024 04:49 AM
Dear All Members,
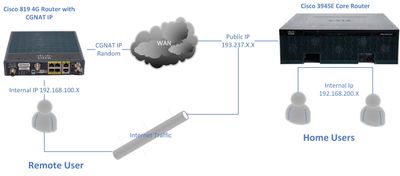
I am trying to set up the 819 4G Router as a VPN Client (Router) with the purpose of full internet tunnelling.
The goal here is the Remote users behind the 4G Router when he travels overseas and connect to any 4g network and when he does whats my IP? He gets the static IP of the Home Network 193.237.X.X----.->
Basically, I am trying to set up a network similar to EXPRESS VPN or BearVPN
I have one static IP at home, but the remote router may sometimes have a CGNAT IP or a Dynamic IP address?
I have googled and searched this forum to see whats the best configuration method for it. Please help me with the Home Router and Remote router configuration that makes it work.
Currently I have the 3945E Home router has Anyconnect with full tunnel that works with anyconnect endpoints (e.g. iPhone , Android , Windows PC) but not a router
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2024 04:58 AM
I was able to make it work after the help of @ccieexpert and @MHM Cisco World Thank you so much for all your help. The only problem that was found. My ACL in the HUB had ip permit any any that made all the problems :'(
Now everything works perfectly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2024 09:23 AM
Yes indeed the permit ip any any in the NAT acl was natting the inbound traffic and causing issues. This is a common problem seen. Glad i was able to help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 04:55 AM
@heshamcentrino1 you can use either DMVPN or FlexVPN, I recommend using FlexVPN which supports Site-to-Site VPN to routers and AnyConnect Remote Access VPN.
As long as the hub at your home has the static IP address, it is fine the remote peer has a dynamic IP address - the remote router can peer with the static IP address and establish a tunnel.
Examples:
https://www.cisco.com/c/en/us/support/security/flexvpn/products-configuration-examples-list.html
https://integratingit.wordpress.com/2016/07/10/configuring-cisco-flexvpn-hub-and-spoke/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 04:58 AM
I believe this is best solved with DMVPN. This is a guide for IOS-XE, but should be the same on your ISR 819: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_dmvpn/configuration/xe-16/sec-conn-dmvpn-xe-16-book.html
Let me know if you need any further assistance in configuring this.
Get in touch: https://torbjorn.dev
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 05:53 AM
Hi Torbjorn,
Thank you very much for reaching out to help. I went through some of the configs but I am still confused on how to substitute for
match identity remote fqdn domain example.com
identity local fqdn hub.example.com
I wonder if I need to setup Dynamic DNS and substuite it for it
I am sorry , I am not a technical R/S guy. I am more of a Collaboration and Wireless rather than Routing/SP and Security. I would appreciate if you could give me my Hub router config and Spoke for it
I already attached everything with addresses. I would appreciate if you could send me the hub and spoke config for my setup.
I appreciate all your great effots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 06:01 AM - edited 01-23-2024 06:10 AM
@heshamcentrino1 you do not need Dynamic DNS to resolve those FQDN names, those are statically assigned identities that are sent during the establishment of the VPN to uniquely identify the connecting router. The spoke router just needs to know the public IP address of the hub, then sends it's identity.
Hub IKEV2 profile
match identity remote fqdn domain example.com
identity local fqdn hub.example.com
Spke IKEV2 profile
match identity remote fqdn domain example.com
identity local fqdn spoke1.example.com
As the remote identity of both domain name ends with example.com, they will match.
The links in the first reply provides information on configuration of a hub and a spoke router using the FQDN as the identity.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 07:56 AM
Hi Rob,
Thank you very much for helping me out. Yes it did work out and the tunnel is up and running also both routers could ping each other however the Internet is not tunnelled at all. When I connected a computer to my remote router. I got my normal WAN IP.
I want the internet tunnelled back to the HUB like a full tunnel VPN
What to add to my configs?
Here you are both of my Hub and Remote router configs
3945E Router config
interface loopback 1
ip address 172.16.0.1 255.255.255.255
no shut
interface virtual-template 2 type tunnel
tunnel source dialer1
ip unnumbered loopback 1
crypto ikev2 keyring KEYRING
peer ANY-PEER
address 0.0.0.0
pre-shared-key local cisco1234
pre-shared-key remote cisco1234
exit
crypto ikev2 profile IKEV2_PROFILE
match identity remote fqdn domain lab.net
identity local fqdn R1.lab.net
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
no virtual-template 1
virtual-template 2
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEV2_PROFILE
interface virtual-template 2 type tunnel
tunnel protection ipsec profile IPSEC_PROFILE
interface loopback3
ip address 10.1.0.1 255.255.255.0
no shut
interface loopback4
ip address 10.1.1.1 255.255.255.0
no shut
router eigrp 1
no auto-summary
network 172.16.0.1
network 10.1.0.0 0.0.255.255
network MY HUB INTERNAL
network MY HUB SPOKE INTERNAL NETWORK
--------------------------------------
819 REMOTE ROUTER
interface loopback1
ip address 172.16.0.2 255.255.255.0
no shut
interface loopback2
ip address 10.3.0.1 255.255.255.0
no shut
interface loopback3
ip address 10.3.1.1 255.255.255.0
no shut
router eigrp 1
no auto-summary
network 172.16.0.2
network 10.3.0.0 0.0.255.255
network MY HUB INTERNAL
network MY HUB SPOKE INTERNAL NETWORK
crypto ikev2 keyring KEYRING
peer ANY-PEER
address 0.0.0.0
pre-shared-key local cisco1234
pre-shared-key remote cisco1234
exit
crypto ikev2 profile IKEV2_PROFILE
match identity remote fqdn domain lab.net
identity local fqdn R2.lab.net
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEV2_PROFILE
interface tunnel1
ip unnumbered loopback 1
tunnel source cellular 0
tunnel destination MY STATIC IP
tunnel protection ipsec profile IPSEC_PROFILE
no shut
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 08:06 AM
@heshamcentrino1 you need a Frontdoor VRF (fVRF) on the spoke, then advertise the default route from the hub to the spoke.
See the fVRF section in this link.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 08:23 AM
Hi Rob,
Thank you so much again for your help so please tell me what should I substitute for these addresses 1.1.1.1 and 1.1.1.2
Is it the WAN IP address or the loopback previously configured or which one sorry to ask again I said I am no where expert in VPN , Tunnels and routing
WAN Interface
interface GigabitEthernet0/0
description ---| WAN Interface |---
vrf forwarding WAN
ip address 1.1.1.1 255.255.255.0
The default route must be configured in the VRF
ip route vrf WAN 0.0.0.0 0.0.0.0 1.1.1.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 11:28 AM
Hi @heshamcentrino1,
You should configure the "vrf forwarding WAN" command on your cellular 0 interface here instead of Gi0/0, as this is the interface where your tunnel is sourced. The static default route is only necessary if you aren't receiving a default gateway from your LTE/4G provider - which is unlikely in this situation and can be left out.
Get in touch: https://torbjorn.dev
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 04:58 PM
Hi @Torbjørn and @Rob Ingram
I found a problem now. I use a Cellular interface with IP address negotiated
when I configure vrf forwarding WAN under the interface, then I am no longer able to get an IP from the carrier as it uses CGNAT IP and then the WAN is down also
when I configured this
crypto ikev2 policy IKEV2_POLICY
! Policy Incomplete(MUST have atleast one complete proposal attached)
match fvrf WAN
!I don't know what to put in the PROPOSAL statement?
Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2024 12:43 AM
@heshamcentrino1 as already mentioned you just need to reference an IKEv2 proposal under the IKEV2 policy, make sure you still match the VRF name under the policy, as below:
crypto ikev2 proposal IKEv2_PROPOSAL
encryption aes-gcm-256
prf sha512
group 20
!
crypto ikev2 policy IKEv2_POLICY
match fvrf WAN
proposal IKEv2_PROPOSAL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2024 03:51 AM
@Rob Ingram and @Torbjørn Thank you all for helping me out. I have tried the solutions but for some reason, the VRF is not allowing my Cellular interface to negotiate with the carrier. Once I configure it it does remove the negotiated IP address and never negotiate another one again. Here you are my config please let me know what I am missing.
Building configuration...
Current configuration : 4397 bytes
!
! Last configuration change at 13:29:23 GMT Wed Jan 24 2024 by heshamcentrino
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname R2_Router
!
boot-start-marker
boot-end-marker
!
!
vrf definition WAN
address-family ipv4
exit-address-family
!
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
!
!
!
aaa session-id common
ethernet lmi ce
clock timezone GMT 0 0
clock summer-time GMT recurring
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
ip dhcp excluded-address 192.168.100.1 192.168.100.50
!
ip dhcp pool Data
import all
network 192.168.100.0 255.255.255.0
dns-server 8.8.8.8 8.8.4.4
default-router 192.168.100.253
!
!
!
ip multicast-routing
ip cef
no ipv6 cef
!
!
!
!
!
multilink bundle-name authenticated
!
!
chat-script lte "" "AT!CALL" TIMEOUT 20 "OK"
!
!
!
!
!
license udi pid C819G-4G-GA-K9 sn FCZ2219104N
!
!
!
crypto ikev2 proposal IKEv2_PROPOSAL
encryption aes-gcm-256
prf sha512
group 20
!
crypto ikev2 policy IKEv2_POLICY
match fvrf WAN
proposal IKEv2_PROPOSAL
!
crypto ikev2 keyring KEYRING
peer ANY-PEER
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco1234
pre-shared-key remote cisco1234
!
!
!
crypto ikev2 profile IKEV2_PROFILE
match fvrf WAN
match identity remote fqdn domain lab.net
identity local fqdn R2.lab.net
authentication local pre-share
authentication remote pre-share
keyring local KEYRING
!
!
!
controller Cellular 0
lte sim data-profile 1 attach-profile 1 slot 0
no lte gps enable
lte modem link-recovery rssi onset-threshold -110
lte modem link-recovery monitor-timer 20
lte modem link-recovery wait-timer 10
lte modem link-recovery debounce-count 6
description T-mobile
!
track 234 ip sla 1 reachability
!
!
!
!
!
crypto ipsec profile IPSEC_PROFILE
set ikev2-profile IKEV2_PROFILE
!
!
!
!
!
!
!
!
interface Loopback0
no ip address
!
interface Loopback1
ip address 172.16.0.2 255.255.255.0
!
interface Loopback2
ip address 10.3.0.1 255.255.255.0
!
interface Loopback3
ip address 10.3.1.1 255.255.255.0
!
interface Tunnel1
ip unnumbered Loopback1
tunnel source Cellular0
tunnel destination 193.237.XXX.XXX
tunnel vrf WAN
tunnel protection ipsec profile IPSEC_PROFILE
!
interface Cellular0
vrf forwarding WAN
ip address negotiated
ip nat outside
ip virtual-reassembly in
encapsulation slip
dialer in-band
dialer string lte
dialer-group 1
async mode interactive
routing dynamic
!
interface Cellular1
ip address negotiated
encapsulation slip
dialer in-band
dialer string lte
dialer-group 1
async mode interactive
routing dynamic
!
interface FastEthernet0
no ip address
!
interface FastEthernet1
no ip address
!
interface FastEthernet2
no ip address
!
interface FastEthernet3
no ip address
!
interface GigabitEthernet0
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0
no ip address
shutdown
clock rate 2000000
!
interface Virtual-Template1 type tunnel
no ip address
tunnel vrf WAN
!
interface Vlan1
ip address 192.168.100.253 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
!
router eigrp 1
network 10.3.0.0 0.0.255.255
network YYY.YYY.0.0
network 172.16.0.0
network 192.168.100.0
!
ip forward-protocol nd
ip http server
ip http access-class 23
ip http authentication aaa
no ip http secure-server
!
!
ip nat inside source list DSL_ACCESSLIST interface Cellular0 overload
ip route 0.0.0.0 0.0.0.0 Cellular0
!
ip access-list extended DSL_ACCESSLIST
permit ip 192.168.100.0 0.0.0.255 any
permit ip any any
!
ip sla 1
icmp-echo 10.1.1.1 source-interface Cellular0
frequency 5
ip sla schedule 1 life forever start-time now
dialer-list 1 protocol ip permit
!
!
!
!
!
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2024 02:40 PM
@Rob Ingram AND @Torbjørn any update on my config please??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2024 08:22 AM
First I will divide issue to two parts
1- you use default route to make spoke reach hub interface (tunnel destination)
Here eigrp push defualt and you use default route this need split using frontVRF ( I mention that in below comment)
If you use static route in spoke (not defualt) to reach hub then no need frontVRF
2- ypu need to config NAT in hub
Tunnel must config as ip nat inside
And ypu need to config dynamic NAT
Ip nat inside source list <any prefix behind spoke> interface < hub interface > overload
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2024 06:53 AM
@MHM Cisco World Thanks a lot for your help and you mentioned.
If you use static route in spoke (not defualt) to reach hub then no need frontVRF
From what I know static route is usually to route a specific address through a specific hop so in my case how can i specify the internet traffic as static route to the tunnel. Can you give me example of that static route?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide