- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Split Tunnel WebEx/Outlook365/Zoom/Skype
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Split Tunnel WebEx/Outlook365/Zoom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2020 02:23 PM - edited 04-15-2020 09:30 PM
Posting to help customers with ASA who need to split tunnel Outlook 365, WebEx, and Zoom.
1. How to optimize Anyconnect for Webex Meetings
2. How to optimize Anyconnect for Office365 connections
3. How to optimize Anyconnect for Zoom Documentation for Split Tunnel
4. Provide Stealth Watch Visibility for Split Tunnel
1. WebEx Split Tunnel Configuration:
##### Step 1: Create an access-list to include the split-exclude networks
access-list ExcludeWebEx extended permit ip 64.68.96.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 66.114.160.0 255.255.240.0 any4
access-list ExcludeWebEx extended permit ip 66.163.32.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 170.133.128.0 255.255.192.0 any4
access-list ExcludeWebEx extended permit ip 173.39.224.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 173.243.0.0 255.255.240.0 any4
access-list ExcludeWebEx extended permit ip 207.182.160.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 209.197.192.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 216.151.128.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 114.29.192.0 255.255.224.0 any4
access-list ExcludeWebEx extended permit ip 210.4.192.0 255.255.240.0 any4
access-list ExcludeWebEx extended permit ip 69.26.176.0 255.255.240.0 any4
access-list ExcludeWebEx extended permit ip 62.109.192.0 255.255.192.0 any4
access-list ExcludeWebEx extended permit ip 69.26.160.0 255.255.240.0 any4
##### Step 2: Create an Anyconnect custom attribute for dynamic split excludes
webvpn
anyconnect-custom-attr dynamic-split-exclude-domains description dynamic-split-exclude-domains
anyconnect-custom-data dynamic-split-exclude-domains webEx webex.com,accompany.com,quovadisglobal.com
##### Step 3: Configure the split exclude in the group-policy
group-policy GP1 attributes
split-tunnel-policy excludespecified
ipv6-split-tunnel-policy excludespecified
split-tunnel-network-list value ExcludeWebEx
anyconnect-custom dynamic-split-exclude-domains value webEx
2. Outlook 365 Split Tunnel Configuration:
##### Step 1: Create an access-list to include the split-exclude networks
access-list ExcludeO365 extended permit ip 104.146.128.0 255.255.128.0 any4
access-list ExcludeO365 extended permit ip 13.107.128.0 255.255.252.0 any4
access-list ExcludeO365 extended permit ip 13.107.136.0 255.255.252.0 any4
access-list ExcludeO365 extended permit ip 13.107.18.10 255.255.255.254 any4
access-list ExcludeO365 extended permit ip 13.107.6.152 255.255.255.254 any4
access-list ExcludeO365 extended permit ip 13.107.64.0 255.255.192.0 any4
access-list ExcludeO365 extended permit ip 131.253.33.215 255.255.255.255 any4
access-list ExcludeO365 extended permit ip 132.245.0.0 255.255.0.0 any4
access-list ExcludeO365 extended permit ip 150.171.32.0 255.255.252.0 any4
access-list ExcludeO365 extended permit ip 150.171.40.0 255.255.252.0 any4
access-list ExcludeO365 extended permit ip 191.234.140.0 255.255.252.0 any4
access-list ExcludeO365 extended permit ip 204.79.197.215 255.255.255.255 any4
access-list ExcludeO365 extended permit ip 23.103.160.0 255.255.240.0 any4
access-list ExcludeO365 extended permit ip 2603:1006::/40 any6
access-list ExcludeO365 extended permit ip 2603:1016::/36 any6
access-list ExcludeO365 extended permit ip 2603:1026::/36 any6
access-list ExcludeO365 extended permit ip 2603:1036::/36 any6
access-list ExcludeO365 extended permit ip 2603:1046::/36 any6
access-list ExcludeO365 extended permit ip 2603:1056::/36 any6
access-list ExcludeO365 extended permit ip 2603:1096:400::/40 any6
access-list ExcludeO365 extended permit ip 2603:1096:600::/40 any6
access-list ExcludeO365 extended permit ip 2603:1096::/38 any6
access-list ExcludeO365 extended permit ip 2603:1096:a00::/39 any6
access-list ExcludeO365 extended permit ip 2603:1096:c00::/40 any6
access-list ExcludeO365 extended permit ip 2603:10a6:200::/40 any6
access-list ExcludeO365 extended permit ip 2603:10a6:400::/40 any6
access-list ExcludeO365 extended permit ip 2603:10a6:600::/40 any6
access-list ExcludeO365 extended permit ip 2603:10a6:800::/40 any6
access-list ExcludeO365 extended permit ip 2603:10d6:200::/40 any6
access-list ExcludeO365 extended permit ip 2620:1ec:4::152/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:4::153/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:8f0::/46 any6
access-list ExcludeO365 extended permit ip 2620:1ec:8f8::/46 any6
access-list ExcludeO365 extended permit ip 2620:1ec:900::/46 any6
access-list ExcludeO365 extended permit ip 2620:1ec:908::/46 any6
access-list ExcludeO365 extended permit ip 2620:1ec:a92::152/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:a92::153/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:c::10/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:c::11/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:d::10/128 any6
access-list ExcludeO365 extended permit ip 2620:1ec:d::11/128 any6
access-list ExcludeO365 extended permit ip 2a01:111:f400::/48 any6
access-list ExcludeO365 extended permit ip 2a01:111:f402::/48 any6
access-list ExcludeO365 extended permit ip 40.104.0.0 255.254.0.0 any4
access-list ExcludeO365 extended permit ip 40.108.128.0 255.255.128.0 any4
access-list ExcludeO365 extended permit ip 40.96.0.0 255.248.0.0 any4
access-list ExcludeO365 extended permit ip 52.104.0.0 255.252.0.0 any4
access-list ExcludeO365 extended permit ip 52.112.0.0 255.252.0.0 any4
access-list ExcludeO365 extended permit ip 52.96.0.0 255.252.0.0 any4
##### Step 2: Create an Anyconnect custom attribute for dynamic split excludes
webvpn
anyconnect-custom-attr dynamic-split-exclude-domains description dynamic-split-exclude-domains
anyconnect-custom-data dynamic-split-exclude-domains o365 sharepoint.com,outlook.office365.com,outlook.office.com
##### Step 3: Configure the split exclude in the group-policy
group-policy GP1 attributes
split-tunnel-policy excludespecified
ipv6-split-tunnel-policy excludespecified
split-tunnel-network-list value ExcludeO365
anyconnect-custom dynamic-split-exclude-domains value o365
3. Zoom Split Tunnel Configuration:
##### Step 1: Create an access-list to include the split-exclude networks
access-list zoom extended permit ip 3.7.35.0 255.255.255.128 any4
access-list zoom extended permit ip 3.21.137.128 255.255.255.128 any4
access-list zoom extended permit ip 3.22.11.0 255.255.255.0 any4
access-list zoom extended permit ip 3.25.41.128 255.255.255.128 any4
access-list zoom extended permit ip 3.25.42.0 255.255.255.128 any4
access-list zoom extended permit ip 3.80.20.128 255.255.255.128 any4
access-list zoom extended permit ip 3.101.32.128 255.255.255.128 any4
access-list zoom extended permit ip 3.101.52.0 255.255.255.128 any4
access-list zoom extended permit ip 3.104.34.128 255.255.255.128 any4
access-list zoom extended permit ip 3.120.121.0 255.255.255.128 any4
access-list zoom extended permit ip 3.127.194.128 255.255.255.128 any4
access-list zoom extended permit ip 3.208.72.0 255.255.255.128 any4
access-list zoom extended permit ip 3.211.241.0 255.255.255.128 any4
access-list zoom extended permit ip 3.235.69.0 255.255.255.128 any4
access-list zoom extended permit ip 3.235.82.0 255.255.254.0 any4
access-list zoom extended permit ip 3.235.71.128 255.255.255.128 any4
access-list zoom extended permit ip 3.235.72.128 255.255.255.128 any4
access-list zoom extended permit ip 3.235.73.0 255.255.255.128 any4
access-list zoom extended permit ip 3.235.96.0 255.255.254.0 any4
access-list zoom extended permit ip 4.34.125.128 255.255.255.128 any4
access-list zoom extended permit ip 4.35.64.128 255.255.255.128 any4
access-list zoom extended permit ip 8.5.128.0 255.255.254.0 any4
access-list zoom extended permit ip 13.52.6.128 255.255.255.128 any4
access-list zoom extended permit ip 13.52.146.0 255.255.255.128 any4
access-list zoom extended permit ip 13.114.106.166 255.255.255.255 any4
access-list zoom extended permit ip 18.205.93.128 255.255.255.128 any4
access-list zoom extended permit ip 50.239.202.0 255.255.254.0 any4
access-list zoom extended permit ip 50.239.204.0 255.255.255.0 any4
access-list zoom extended permit ip 52.61.100.128 255.255.255.128 any4
access-list zoom extended permit ip 52.81.151.128 255.255.255.128 any4
access-list zoom extended permit ip 52.197.97.21 255.255.255.255 any4
access-list zoom extended permit ip 52.202.62.192 255.255.255.192 any4
access-list zoom extended permit ip 52.215.168.0 255.255.255.128 any4
access-list zoom extended permit ip 64.69.74.0 255.255.255.0 any4
access-list zoom extended permit ip 64.125.62.0 255.255.255.0 any4
access-list zoom extended permit ip 64.211.144.0 255.255.255.0 any4
access-list zoom extended permit ip 65.39.152.0 255.255.255.0 any4
access-list zoom extended permit ip 69.174.57.0 255.255.255.0 any4
access-list zoom extended permit ip 69.174.108.0 255.255.252.0 any4
access-list zoom extended permit ip 99.79.20.0 255.255.255.128 any4
access-list zoom extended permit ip 103.122.166.0 255.255.254.0 any4
access-list zoom extended permit ip 109.94.160.0 255.255.252.0 any4
access-list zoom extended permit ip 109.244.18.0 255.255.255.128 any4
access-list zoom extended permit ip 109.244.19.0 255.255.255.0 any4
access-list zoom extended permit ip 115.110.154.192 255.255.255.192 any4
access-list zoom extended permit ip 115.114.56.192 255.255.255.192 any4
access-list zoom extended permit ip 115.114.115.0 255.255.255.192 any4
access-list zoom extended permit ip 115.114.131.0 255.255.255.192 any4
access-list zoom extended permit ip 120.29.148.0 255.255.255.0 any4
access-list zoom extended permit ip 147.124.96.0255.255.224.0 any4
access-list zoom extended permit ip 160.1.56.128 255.255.255.128 any4
access-list zoom extended permit ip 161.199.136.0 255.255.252.0 any4
access-list zoom extended permit ip 162.12.232.0 255.255.252.0 any4
access-list zoom extended permit ip 162.255.36.0 255.255.252.0 any4
access-list zoom extended permit ip 165.254.88.0 255.255.254.0 any4
access-list zoom extended permit ip 173.231.80.0 255.255.240.0 any4
access-list zoom extended permit ip 192.204.12.0 255.255.252.0 any4
access-list zoom extended permit ip 202.177.207.128 255.255.255.224 any4
access-list zoom extended permit ip 202.177.213.96 255.255.255.224 any4
access-list zoom extended permit ip 204.80.104.0255.255.248.0 any4
access-list zoom extended permit ip 204.141.28.0 255.255.252.0 any4
access-list zoom extended permit ip 207.226.132.0 255.255.255.0 any4
access-list zoom extended permit ip 209.9.211.0 255.255.255.0 any4
access-list zoom extended permit ip 209.9.215.0 255.255.255.0 any4
access-list zoom extended permit ip 210.57.55.0 255.255.255.0 any4
access-list zoom extended permit ip 213.19.144.0 255.255.255.0 any4
access-list zoom extended permit ip 213.19.153.0 255.255.255.0 any4
access-list zoom extended permit ip 213.244.140.0 255.255.255.0 any4
access-list zoom extended permit ip 221.122.88.64 255.255.255.224 any4
access-list zoom extended permit ip 221.122.88.128 255.255.255.128 any4
access-list zoom extended permit ip 221.122.89.128 255.255.255.128 any4
access-list zoom extended permit ip 221.123.139.192 255.255.255.224 any4
access-list zoom extended permit ip 2620:123:2000::/40 any6
##### Step 2: Create an Anyconnect custom attribute for dynamic split excludes
webvpn
anyconnect-custom-attr dynamic-split-exclude-domains description dynamic-split-exclude-domains
anyconnect-custom-data dynamic-split-exclude-domains zoom zoom.us,cloudfront.net,MeetingConnector.IP,MeetingConnector.IP2,MeetingConnector2.IP,MeetingConnector2.IP2
##### Step 3: Configure the split exclude in the group-policy
group-policy GP1 attributes
split-tunnel-policy excludespecified
ipv6-split-tunnel-policy excludespecified
split-tunnel-network-list value zoom
anyconnect-custom dynamic-split-exclude-domains value zoom
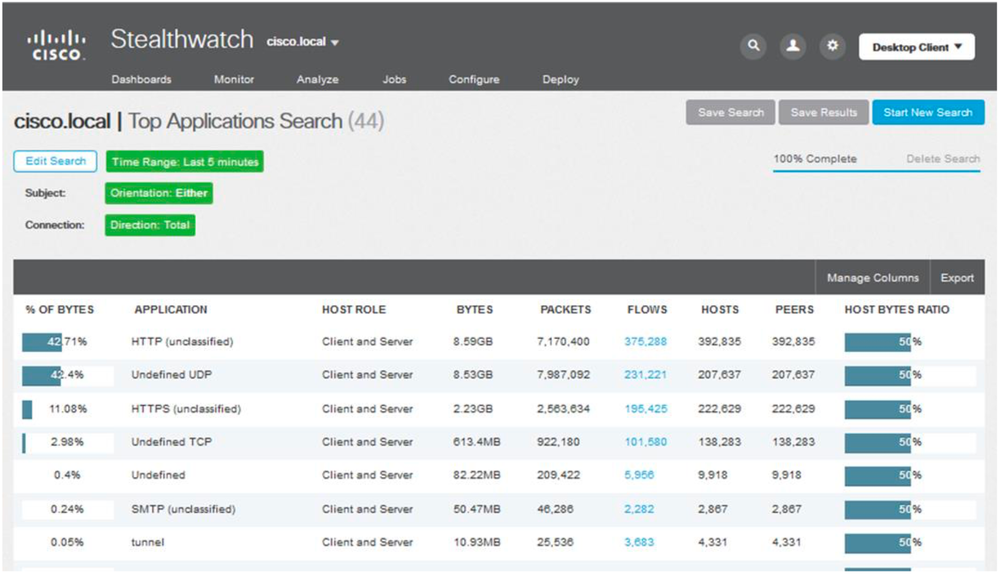
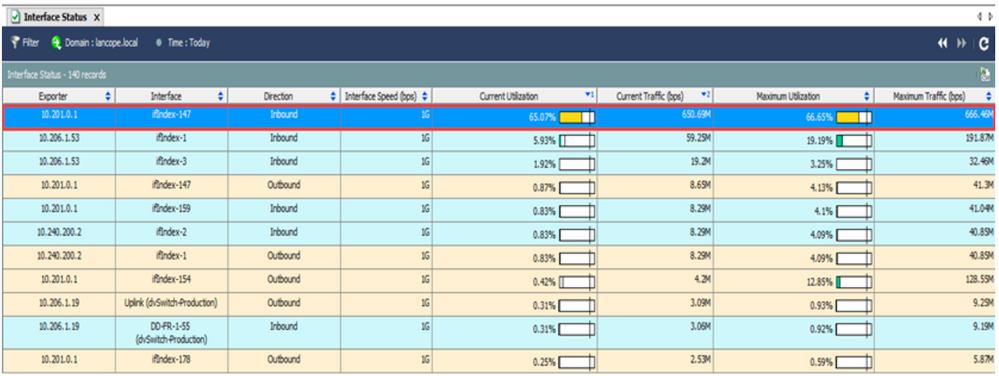
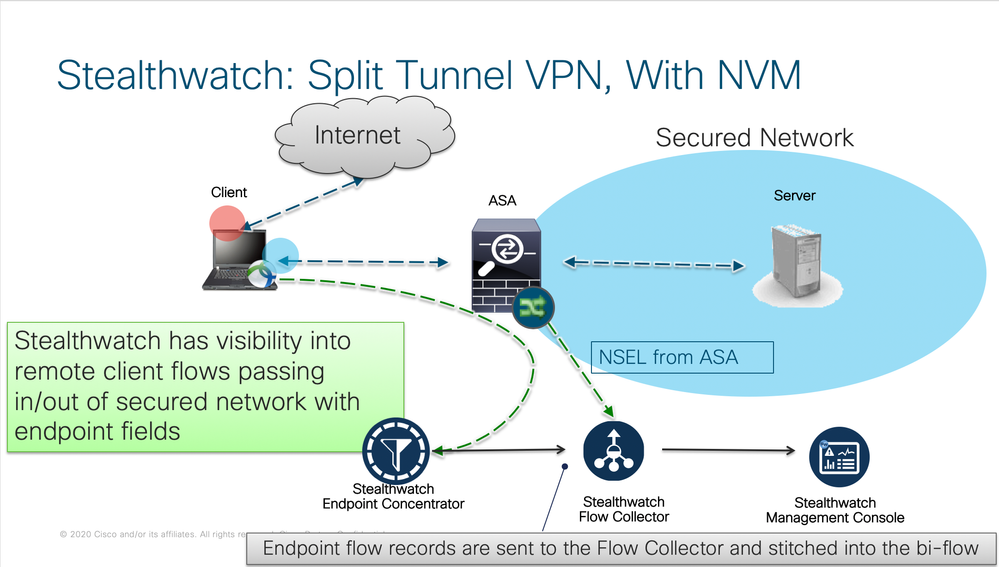
4. Provide Stealth Watch Visibility for Split Tunnel:
Solution 3: Identify the specific interface that is either overloaded or close to capacity, and identify the applications, users, or hosts that are taxing the network.

- Labels:
-
AnyConnect
-
Clientless SSL
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2020 02:23 AM
In anyconnect 4.6 you should be able to du excludes from the full tunnel on URL in-areas of ip. That would be easier and more dynamic. Has any one tested it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2020 10:46 AM - edited 03-26-2020 10:57 AM
The SAAS providers like O365 public ip address can change which is why you need AC Dynamic Split Tunnel in AC 4.6 or higher or direct IP for the split tunnel to work. We have provide a way to do both for O365/WebEx and Zoom in case you don't have AC 4.6 or higher and need a way via to direct IP to accomplish the same goal. We have also uploaded the Dynamic Split tunnel pdf to this Community page to ensure what ever option you choose that you will be successful in your operation as we support everyone during the COVID-19 challenges.
please notice the sub-domain you want to bypass must be listed. We do not support wild card bypass in the ASA/FTD.
We are still working to determine the configuration for Skype but believe by next week we will have the information updated.
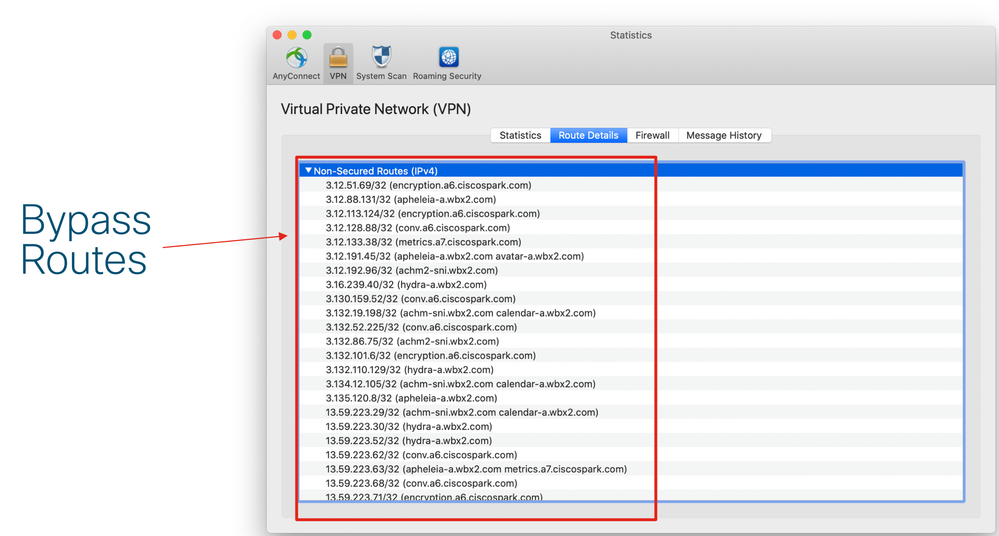
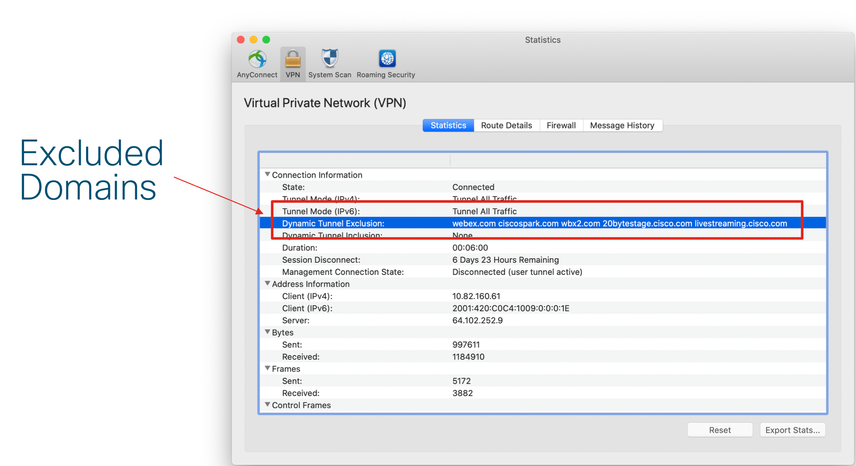
This would be your end results for success:
Here we see the Direct IP bypass rules:
Here we see the Dynamic Split Tunnel based on Domain:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 01:14 AM
Hi Nidamen,
thank you for sharing this!
Much appreciate :)!
However...are you 100% sure about "no wildcard"?
In our Tests we can see that "webex.com" is enough to split e.g "subdomains.webex.com"
Another Question...could you also please Update this Thread to support MS Teams?
Would be awesome!
https://repl.it/@ministryofjay/AnyConnectO365DynamicExclude
This isn't including the necessary Teams URLs/IPs as per Official Whitelist Document:
https://docs.microsoft.com/de-de/office365/enterprise/urls-and-ip-address-ranges
Thank you in advance.
PS: Ice on the Cake...would be nice if the ASA would have a native Function to Download and Parse JSON/XML Files for ACLs/Split Tunneling...or even better, Layer 7 Detection in Anyconnect based on "Apps" instead of Domains/IPs ;)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 07:49 AM - edited 03-26-2020 11:05 AM
Link to Url Filtering:
Info where we state no wild cards supported:
Configuring URL Conditions/Step 5/You can enter a URL or IP address. This field does not support wild cards.
Regarding matching list entries, note the following:
• The system matches sub-level domains if a higher-level domain exists in a URL or DNS list. For example, if you add example.com to a DNS list, the system matches both www.example.com and test.example.com.
• The system does not perform DNS lookups (forward or reverse) on DNS or URL list entries. For example, if you add http://192.168.0.2 to a URL list, and it resolves to http://www.example.com, the system only matches http://192.168.0.2, not http://www.example.com.
• If you add a URL ending in a forward slash (/) character to a URL list, only exact URLs match that entry.
• If you add a URL that does not end in a forward slash to a URL or DNS list, any URL that shares the same common prefix matches that entry. For example, if you add www.example.com to a URL list, the system matches both www.example.com and www.example.com/example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 10:49 PM
• The system matches sub-level domains if a higher-level domain exists in a URL or DNS list. For example, if you add example.com to a DNS list, the system matches both www.example.com and test.example.com.
Hi Nidamen.
The high-level domain thing was my unterstanding in terms of Wildcards in this Case.
Sorry for misconfusion.
You just confirmed our tests.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 10:50 AM
Hi Nidamen,
Thanks for sharing AC Dynamic Split Tunneling v2 doc, I can confirm we are running AC 4.6 to 4.9, ASA version 9.6 and ASDM 7.7 Our ASA is running in multi-context mode.
I can see anyconnect-custom-attr command under webvpn commands (attached - webvpn) however I am not seeing anyconnect-custom-data command under global config mode (please see attached - global config mode). Also there is no anyconnect-custom command available under group policy commands (attached - group policy commands)
I am not sure if we are seeing the difference because our firewall is operating in multicontext mode or I have to configure anyconnect-custom-attr first before the absent commands will become available?
I have also tried via ASDM, I can see the options under Remote Access VPN > Network (Client) Access > Advanced to configure AnyConnect Customer Atrributes and AnyConnect Custom Attribute Names (attached - ASDM AnyConnect custom) however I am not seeing Custom Attributes option under AnyConnect Client for Group Policy configuration (attached - ASDM gp edit).
Can you please advise? Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 09:22 AM
Hello nidamen,
First off thank you very much for putting this documentation together. It has been very helpful!
We've implemented this solution and it was working great for Dynamic Split Tunneling via domain names. However when attempting to add extended ACL's the traffic for specific Subnet's I specified which d0not associate to a Domain would not be split. Upon opening a TAC case I was told that Extended ACL's were not Cisco best practice/supported with Dynamic Split Tunneling and that using a Standard ACL would resolve the issue. This did in fact resolve the issue, but I found it curious that clearly you and I'm assuming others are using Extended ACL's and this is working.
Is it possible this might be a feature in a newer ASA Code? We're currently running ASA Version: 9.6(4)10 and AnyConnect Version: 4.8.03036
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 04:08 PM - edited 04-15-2020 09:26 PM
We have verified with the ASA TME the following:
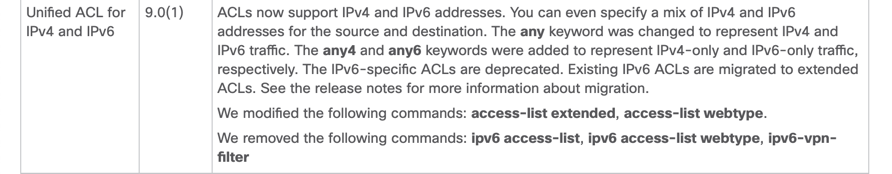
1. In ASA 9.0 they introduced Unified (IPv4 + IPv6)
2. If its IPv4 and IPv6 then you have to use and Extended ACL. See Video (MP4) attached (ExtendedACL4_6.mp4).
Thank You to ASA TME team for their support (Paul and Divya)
Please see Video for details. I believe Tac may have informed you on code for ASA below 9.0?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 09:44 AM
Hello Nidamen,
We have configured split tunnel on ASA 9.2 (2)9 and this we can see some traffic is choosing the local gateway. However in one to one call scenario team traffic is still choosing the VPN gateway. When split VPN is on it requires two tries to make a call and sometime we need to send message twice. First time it failed and in second attempt it sent but there are some lagging all time. It needs more time to send message while split tunnel on.
Any idea to solve the problem?
Thanks,
Mohammad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 10:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2020 12:30 PM
Did you ever solve this problem? We are having this issue as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2020 01:10 PM
Unfortunately we did not. We implemented Full Split Tunneling and now only tunneling traffic destined back to the Data Center through the VPN tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2020 10:02 AM
Thanks for this information I see now and understand.
One further question. I see you have these split up into three separate Extended ACL's. Is there a way to apply all these of these to one Group-Policy being applied to an AnyConnect Connection Profile? Or would I have to consolidate to one Extended ACL?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide