- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: 9800-CL WLC Repeated Client Exclusion for Wrong PSK
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
9800-CL WLC Repeated Client Exclusion for Wrong PSK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 08:58 AM
I've recently inherited a 9800-CL WLC with a somewhat questionable configuration. It seems to be working as expected, however reviewing the Syslog shows regular repeated errors. The error in question is:
%CLIENT_EXCLUSION_SERVER-5-ADD_TO_EXCLUSIONLIST_REASON_DYNAMIC: Chassis 1 R0/0: wncmgrd: Client MAC: dcb5.XX was added to exclusion list associated with AP Name:AP013, BSSID:MAC: 84f1.XX, reason:Wrong PSK
I'm seeing these appear about once per minute or more. The error is thrown repeatedly for the same device every few minutes it appears with a decent number of devices causing the error while on-site. Oddly enough there haven't been any reported issues with disconnects or failure to connect. From what I've found, based on the MAC address every device being reported is an Apple device, almost certainly to be an iPhone that is issued to users. Is there any specific configuration that may have been misconfigured that might cause this issue? Any ideas would be greatly appreciated.
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 09:24 AM
>... with a somewhat questionable configuration.
- In that context , review the 9800-CL WLC configuration with the CLI command show tech wireless and feed the output into
Wireless Config Analyzer
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 09:29 AM
Currently reviewing that report now actually. Nothing too major, and nothing that really explains the current log... might be an Apple specific config issue that's not reported as an error/warning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 09:52 AM
- Ok, I also noted : https://community.cisco.com/t5/wireless/c9800-exclusion-due-to-wrong-psk-macos-clients-only/m-p/4820972#M254968
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 01:08 PM
I had saw this article, but it was specific to Mac OS not iOS like I'm experiencing so I had ruled it out. Also after comparing RA Trace to his, his clients got past layer 2 authentication suggesting it's a different issue. Although looking through the RA trace maybe I need to understand this more. It appears this is the hangup point:
| 2024/02/05 15:42:05.864 | client-keymgmt | Sent M1 for EAPOL 4-Way Handshake |
| 2024/02/05 15:42:05.869 | client-keymgmt | Could not validate MIC received in M2 message |
| 2024/02/05 15:42:05.869 | client-keymgmt | Fast roam key validation failure on M2 |
| 2024/02/05 15:42:06.865 | client-keymgmt | Controller did not receive response for M1, sending retransmission |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 06:54 AM - edited 02-12-2024 06:56 AM
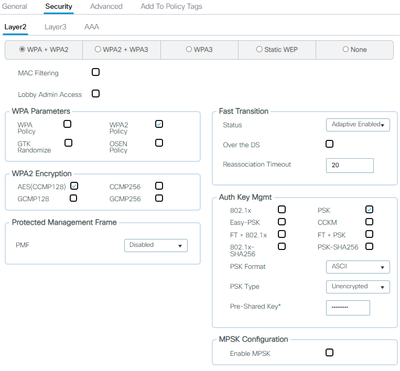
Can i see l2 secuirty of wlan
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 07:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 07:03 AM
Disbale adptive FT since you use PSK without FT.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 07:10 AM
Disabled. Still seeing errors reported though...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 07:13 AM
Wait' until the wifi client re-asso or manually disconnected one wifi client (you see it mac in log server) and reconnect again and check log server.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 10:43 AM
Can you get Radioactive Trace for one of the clients and run it through Cisco Wireless Debug Analyzer and see if it points to any errors
https://cway.cisco.com/wireless-debug-analyzer/
Make sure to capture the radio active trace for complete session.
Jagan Chowdam
/**Please rate helpful responses**/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 12:57 PM - edited 02-05-2024 12:59 PM
Parsed RA Trace for a single client provided repeating entries of the following:
Time Task Translated
2024/02/05 14:56:21.040 client-orch-sm Client made a new Association to an AP/BSSID: BSSID 84f1.XX, WLAN GUEST, Slot 1 AP 84f1.XX, AP012
2024/02/05 14:56:21.041 dot11 Association success for client, assigned AID is: 10. Client performed fast roam.
2024/02/05 14:56:21.055 client-keymgmt Could not validate MIC received in M2 message
2024/02/05 14:56:21.055 client-keymgmt Fast roam key validation failure on M2
2024/02/05 14:56:22.057 client-keymgmt Could not validate MIC received in M2 message
2024/02/05 14:56:22.057 client-keymgmt Fast roam key validation failure on M2
2024/02/05 14:56:23.055 client-keymgmt Could not validate MIC received in M2 message
2024/02/05 14:56:23.055 client-keymgmt Fast roam key validation failure on M2
2024/02/05 14:56:24.050 client-keymgmt Reached maximum retries for M1
2024/02/05 14:56:24.052 client-orch-sm Controller initiated client deletion with code: CO_CLIENT_DELETE_REASON_NOOP. Explanation: Default code when no other reason is known, it should have been replaced with corresponding delete trigger, internal error. Client will recover after a new session. Actions: Collect RA trace for the client
The advanced debug insights are suggesting that following the client "L2 Authentication Request" there's no logged interactions between the device and the AP/WLC. No authentication failure response, nothing. Which explains the disconnect reason being "NOOP" which apparently is the error for an unreported/unexplained error... Just repeated entries of this association attempt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 02:02 PM
Is Cisco Centralized Key Management (CCKM) feature enabled on the SSID? If it is, can you disable it and check.
I've seen connectivity issues with new WiFi 6E apple devices when CCKM enabled on SSID level.
Jagan Chowdam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2024 07:38 AM
Checked, but no dice. CCKM isn't enabled on any of our SSIDs...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2024 09:12 AM
What version of software are you using?
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide