- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: 9800 Guest Anchor Design
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 10:47 AM
I am trying to understand Guest Anchoring with the 9800 Controllers.
In the 5500 series WLCs you had to access the WMI from the inside network through the firewall to the Anchor Controller Mgmt Vlan on a DMZ. Then create another sub-interface on the Firewall for the guest traffic to go out to the Internet once de-encapsulated. You could not have the AC connect to the inside network as you had to have an SVI on the Mgmt and Guest vlan possibly creating a backdoor if the Mgmt interface was on the inside network.
Since the 9800's don't need an SVI for the guest traffic has Cisco changed it's best practices to allow the AC WMI to connect directly to the inside network and then we don't have to create another sub-interface on the firewall for management and create all the rules needed AC management and tunneling?
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2024 12:10 AM - edited 04-18-2024 12:11 AM
@nir wittenberg Hi, I was informed by Cisco some time ago that they see there WLCs as a secure boundary device and that traffic should not be able to pass between management and guest functions. However, accepting this and putting it in to practice in my eyes was always a leap of faith too far
Based on what you are intimating I would suggest either;
Put the WMI in a dmz on it's own, and then drop the L2 guest traffic into another DMZ to keep traffic separate. This could be done with a trunk port from the WLC. It will mean passing the WMI tunnel traffic through from an inside network to the WMI DMZ.
The other option is to be brave, put the WMI on a separate physical interface on the WLC and connect to an inside network, and then put the guest L2 VLANs into a different interface on the WLC and pass to a DMZ/FW for access control. You could put some form of interface ACL onto the WMI L3 interface to restrict to traffic to/from the export WLCs you connect to.
Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 10:14 PM
- More of a generic reply ; have a look at https://www.cisco.com/c/en/us/support/docs/wireless/catalyst-9800-series-wireless-controllers/213912-configure-mobility-anchor-on-catalyst-98.html
Note that it is always advisable to have a checkup of the involved 9800 WLC's configuration with the CLI command show tech wireless and feed the output to : Wireless Config Analyzer
Meaning that in your case it will also point to errors related to anchoring setups (e.g.)
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2024 09:55 AM
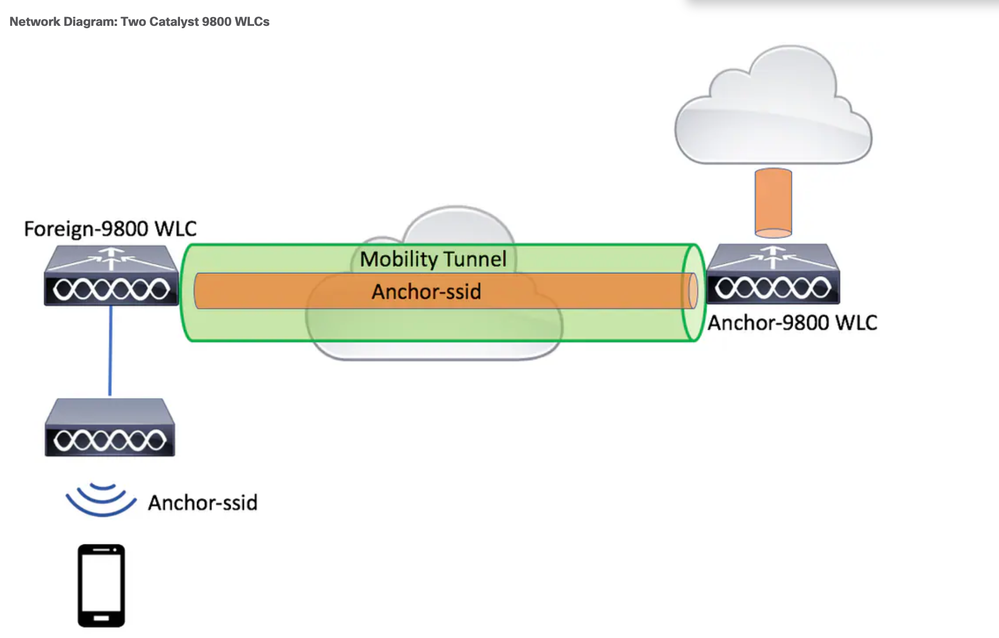
There is not one mention of a firewall/DMZ in that support doc. It does show a diagram of the Forgein and Anchor connecting via the internal network and then a link to the Internet from the Anchor. That document lacks so much detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 11:58 PM
SVI's do exist on C9800 but they are not needed, but one use case is to configure VRFs to isolate Guest traffic on a different VLAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2024 12:10 AM - edited 04-18-2024 12:11 AM
@nir wittenberg Hi, I was informed by Cisco some time ago that they see there WLCs as a secure boundary device and that traffic should not be able to pass between management and guest functions. However, accepting this and putting it in to practice in my eyes was always a leap of faith too far
Based on what you are intimating I would suggest either;
Put the WMI in a dmz on it's own, and then drop the L2 guest traffic into another DMZ to keep traffic separate. This could be done with a trunk port from the WLC. It will mean passing the WMI tunnel traffic through from an inside network to the WMI DMZ.
The other option is to be brave, put the WMI on a separate physical interface on the WLC and connect to an inside network, and then put the guest L2 VLANs into a different interface on the WLC and pass to a DMZ/FW for access control. You could put some form of interface ACL onto the WMI L3 interface to restrict to traffic to/from the export WLCs you connect to.
Hope that helps.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide