- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- 9800 WLC CLI PIV Works but Web GUI Doesn't
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
9800 WLC CLI PIV Works but Web GUI Doesn't
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 09:45 AM
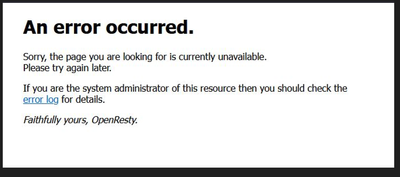
I have successfully enabled PIV authentication for CLI via ISE. However, web does not work, gives me openresty error after entering my PIN. Background - I am with DOI and obtained a certificate for the WLC from the DOI CA. Our PIV cards are provided by ENTRUST. I use the Entrust trust point for CLI.
This allows me to use CLI PIV -
crypto pki trustpoint ENTRUST_MG_SVC_SSP_CA
enrollment terminal
authorization username alt-subjectname userprinciplename
revocation-check none
cyrpto pki authenticate ENTRUST_MG_SVC_SSP_CA
Insert Certificate HERE
ip ssh server certificate profile
user
trustpoint verify ENTRUST_MG_SVC_SSP_CA
Ip http secure-trustpoint (WLC trustpoint)
Ip http secure-client-auth
ip http secure-peer-verify-trustpoint (WLC Trustpoint) - I've tried using ENTRUST_MG_SVC_SSP_CA as well.
ip http secure-piv-based-auth secure-piv-based-author-only
TAC has been working on this for a few months with no resolution yet. Any suggestions? I've tried 17.3, 17.4, 17.12.1, 17.12.2 with no changes.
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 10:35 PM
>...web does not work, gives me openresty error after entering my PIN. Background
- What is the error ? Can you provide a screenshot (e.g.)
- Post output of : show ip http server status | inc PIV
- Have a checkup of the 9800 WLC configuration with the CLI command show tech wireless and feed the output into :
Wireless Config Analyzer
- Have a try with 17.9.4a
M.
-- Let everything happen to you
Beauty and terror
Just keep going
No feeling is final
Reiner Maria Rilke (1899)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2024 07:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2024 09:33 AM
>....Wireless Config Analyzer isn't working for me. I can upload and run it but there is no output.
- Note that Wireless Config Analyzer needs the output of show tech wireless ; not show tech or show tech-support
Strongly advising to go ahead with it : This is so good
M.
-- Let everything happen to you
Beauty and terror
Just keep going
No feeling is final
Reiner Maria Rilke (1899)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2024 09:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 12:23 AM
>....gives me openresty error after entering my PIN.
- What is the error ?
M.
-- Let everything happen to you
Beauty and terror
Just keep going
No feeling is final
Reiner Maria Rilke (1899)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 05:42 AM
i provided a screen shot above
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 05:57 AM
- Sorry , I don't have it currently (screenshot) , you may want to try again,
M.
-- Let everything happen to you
Beauty and terror
Just keep going
No feeling is final
Reiner Maria Rilke (1899)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 06:19 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 06:50 AM
- Check 9800 controller logs when that message appears ,
M.
-- Let everything happen to you
Beauty and terror
Just keep going
No feeling is final
Reiner Maria Rilke (1899)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 07:30 AM
sho debug
General OS:
AAA Authentication debugging is on
IOSXE Conditional Debug Configs:
Conditional Debug Global State: Stop
IOSXE Packet Tracing Configs:
license policy manager client:
platform software policy_manager_error debugging is on
Packet Infra debugs:
Ip Address Port
------------------------------------------------------|----------
HTTP Server:
HTTP Server transaction debugging is on
HTTP Server tokens debugging is on
HTTP Server EZSetup debugging is on
HTTP Server URL debugging is on
HTTP Server Authentication debugging is on
HTTP Server Side Includes debugging is on
HTTP Application Inout debugging is on
HTTP Application Detail debugging is on
HTTP Server Error debugging is on
HTTP SSL Error debugging is on
HTTP CTC trace debug debugging is on
HTTP CTC error debug debugging is on
HTTP SESSION debugging is on
HTTP TPS Trace debugging is on
HTTP TPS Error debugging is on
HTTP WSMAN debugging is on
PKI:
Crypto PKI Msg debugging is on
Crypto PKI Trans debugging is on
Crypto PKI Validation Path debugging is on
ibrcgbwlc002#sho log
Syslog logging: enabled (0 messages dropped, 3 messages rate-limited, 0 flushes, 0 overruns, xml disabled, filtering disabled)
No Active Message Discriminator.
No Inactive Message Discriminator.
Console logging: level critical, 2 messages logged, xml disabled,
filtering disabled
Monitor logging: level debugging, 0 messages logged, xml disabled,
filtering disabled
Buffer logging: level debugging, 294 messages logged, xml disabled,
filtering disabled
Exception Logging: size (4096 bytes)
Count and timestamp logging messages: enabled
Persistent logging: disabled
No active filter modules.
Wed, 17 Jan 2024 15:28:42 GMT 192.168.1.5 /openresty_pki/local-certificate/ibrcgbwlc002.pfx ok
Protocol = HTTP/1.1 Method = GET
AAA/BIND(00000FD3): Bind i/f
CRYPTO_PKI: (A0067) Session started - identity selected (ibrcgbwlc002.pfx)ibrcgbwlc002.pfx:refcount after increment = 1
CRYPTO_PKI: Begin local cert chain retrieval.
CRYPTO_PKI: Done with local cert chain fetch 0.
CRYPTO_PKI: Rcvd request to end PKI session A0067.
CRYPTO_PKI: PKI session A0067 has ended. Freeing all resources.ibrcgbwlc002.pfx:unlocked trustpoint ibrcgbwlc002.pfx, refcount is 0
CRYPTO_PKI: PKI session A0000 has ended. Freeing all resources completed
CRYPTO_PKI: (A0068) Session started - identity selected (ibrcgbwlc002.pfx)ibrcgbwlc002.pfx:refcount after increment = 1
CRYPTO_PKI: Rcvd request to end PKI session A0068.
CRYPTO_PKI: PKI session A0068 has ended. Freeing all resources.ibrcgbwlc002.pfx:unlocked trustpoint ibrcgbwlc002.pfx, refcount is 0
CRYPTO_PKI: PKI session A0000 has ended. Freeing all resources completed
CRYPTO_PKI: Begin trustpoint info get.
CRYPTO_PKI: Successfully got trustpoint info.
CRYPTO_PKI: Freeing trustpoint info.
CRYPTO_PKI: Successfully freed trustpoint info.
CRYPTO_PKI: (A0069) Session started - identity selected (ibrcgbwlc002.pfx)ibrcgbwlc002.pfx:refcount after increment = 1
CRYPTO_PKI: Begin local cert chain retrieval.
CRYPTO_PKI: Done with local cert chain fetch 0.
CRYPTO_PKI: Rcvd request to end PKI session A0069.
CRYPTO_PKI: PKI session A0069 has ended. Freeing all resources.ibrcgbwlc002.pfx:unlocked trustpoint ibrcgbwlc002.pfx, refcount is 0
CRYPTO_PKI: PKI session A0000 has ended. Freeing all resources completed
http_ifs_server_urlhook: file not found size ret=-1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2024 10:10 AM
FYI this is currently being tested on a 9800-L. I originally started on a 9800-40 which had the original problem but as that is production I had to switch gears to a test 9800-L. So it's the same on multiple platforms.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 09:24 AM
Were you able to resolve this. I am having the exact same issue. Cisco TAC has not provided one single solution or troubleshooting step
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 09:46 AM
Nope. I've got HTTS support as well and with their lab they get it to work with a soft certificate and their CA. Using DOI provided web cert, along with hard token PIV fails. They say it may be because the PIV Entrust CA has additional junk in their certificate it can handle. Having weekly meetings about it. Here is my current config:
crypto pki trustpoint ibrcgbwlc002
enrollment terminal pem
subject-name C=US, ST=CA, L=Sacramento, O=BOR, OU=CGB, CN=ibrcgbwlc002.bor.doi.net
subject-alt-name ibrcgbwlc002.bor.doi.net
chain-validation continue DOIRootCA2 ---see below 4b
revocation-check crl
rsakeypair WEBGUI2048
authorization username alt-subjectname userprinciplename
hash sha256
!
ip http server
ip http authentication aaa login-authentication AMLT_HWISE
ip http authentication aaa exec-authorization AMLT_HWISE
ip http secure-server
ip http secure-client-auth
ip http secure-trustpoint ibrcgbwlc002
ip http secure-peer-verify-trustpoint ibrcgbwlc002
ip http secure-piv-based-auth secure-piv-based-author-only
ip http client source-interface Vlan900
With this, I don't get prompted for any cred, just fails. If i remove ip http secure-peer-verify-trustpoint ibrcgbwlc002 I get prompted for PIV and PIN. Still fails. Are you in the government?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 10:20 AM
Thank you for sharing this. I have the exact same configuration except for the chain validation and revocation check. I have set both none. Sometimes I get a page saying you have been logged out, click here to log back in and it goes back to the error page. Other times it goes directly to the error page. No logs in radius server so it's not even making it there. At this point I don't know what debugs I can enable that can give me an idea on what's happening. I can log in to the CLI using the PIV card
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide