- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Ask the Expert: Wireless LAN Security
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2016 08:12 AM - edited 07-05-2021 05:15 AM

Welcome to this Cisco Support Community Ask the Expert conversation. This is an opportunity to learn and any ask questions about how to secure a wireless network with Cisco expert Roman Manchur
Wireless networks have became pervasive in today's world. Cisco offers very strong wireless porfolio that helps business to connect to the Internet anywhere anytime. Network managers need reassurance that solutions are available to protect their WLANs from these vulnerabilities and that WLANs can provide the same level of security, manageability, and scalability offered by wired LANs.
This session will focus on answering question regarding how to deploy, configure and troubleshot security in a wireless network and also the common pitfalls and issues that might happen in an installed secured wireless network.
To participate in this event, please use the ![]() button to ask your question.
button to ask your question.
Ask questions from Monday June 20 to Friday July 1st , 2016
 Roman Manchur is a Customer Support engineer in the Cisco Technical Assistance Center in Cisco Brussels. He is expert on any wireless products, including Wireless LAN controllers and Access Points, as well as in many security products and technologies, including IBNS, ISE, ACS4.x/ACS5.x, AAA Security, RADIUS, and TACACS. Roman has over 8 years of experience in IT. He joined Cisco in 2011. Prior to Cisco he worked at Priocom, Pysus, Aricent and Telread. Roman holds a CCIE in Wireless (#47699) and a Master in Sciences in Telecommunications and IT from the National University Lviv Polytechnic.
Roman Manchur is a Customer Support engineer in the Cisco Technical Assistance Center in Cisco Brussels. He is expert on any wireless products, including Wireless LAN controllers and Access Points, as well as in many security products and technologies, including IBNS, ISE, ACS4.x/ACS5.x, AAA Security, RADIUS, and TACACS. Roman has over 8 years of experience in IT. He joined Cisco in 2011. Prior to Cisco he worked at Priocom, Pysus, Aricent and Telread. Roman holds a CCIE in Wireless (#47699) and a Master in Sciences in Telecommunications and IT from the National University Lviv Polytechnic.
Roman might not be able to answer each question due to the volume expected during this event. Remember that you can continue the conversation on the Security and Network Management Community
Find other https://supportforums.cisco.com/expert-corner/events.
**Ratings Encourage Participation! **
Please be sure to rate the Answers to Questions
Monica Lluis
Community Manager Lead
Solved! Go to Solution.
- Labels:
-
Wireless Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2016 10:19 AM
Now it works perfectly! Thanks Roman!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2016 12:15 AM
Hi Jblack,
Thanks for getting back and glad to hear it helped :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2016 05:14 PM
Hi Roman,
One of our customers has Cisco WLC, MS NPS RADIUS server, and some clients doing WPA2-Enterprise authentication.
For some reason, all the endpoints work, except Win7 clients.
With either self, or public signed certs, Win7 would prompt for username/password, but after clicking OK, authentication would fail.
Win7 does NOT prompt for user to accept cert, while NPS has a log saying cert is not trusted.
Why would Win7 not prompt for user to accept cert, and how do we enable that prompt?
As a temporary workaround for testing purpose, we unchecked the option to validate server cert.
I don't remember having to do this extra step in any of my previous WPA2-Enterprise deployments...did Win7 clients change this behavior somehow in the past year or two?
Have you seen this same issue before?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2016 09:31 AM
Hi,
Thanks for your question.
From what you are saying your customer is using EAP-PEAP authentication in the network. In generic case it does require server certificate to be trusted by client, only after certificate validation is successful client will be prompted for username and password.
In native supplicant configuration settings on Windows you have following options:
- Validate server certificate (enabled by default). Can be disabled as workaround in cases client has no trust for server certificate, like in your case.
- Do not prompt user to authorize new servers or trusted root certification authorities (disabled by default). That option enable / disable pop up for client to trust server certificate during authentication. That option is probably enabled on your Windows 7 client(s). If not, but no pop up is still happening, that's something you will need to check with Microsoft support team.
Reference screenshot:
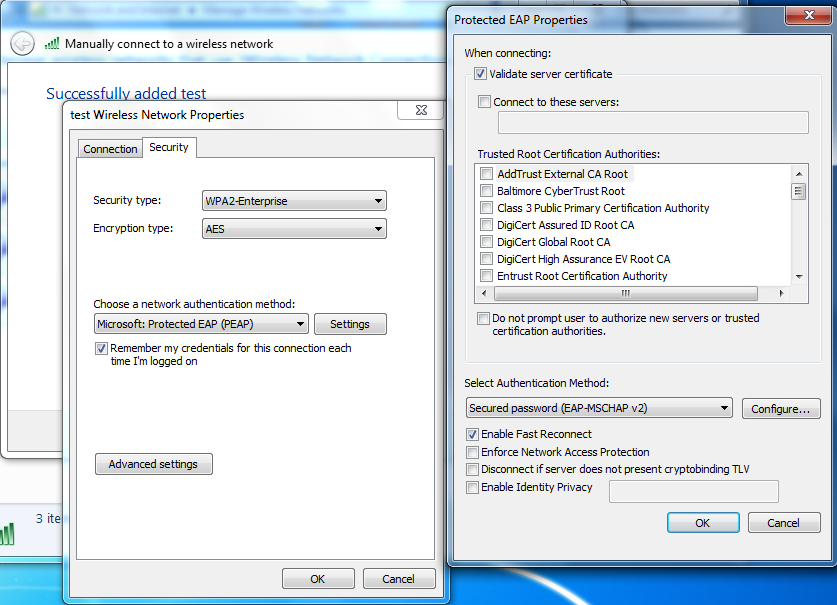
As final solution I would recommend to import your NPS server certificate under trusted CA list on all clients in your network (can be pushed with GPO policies), so all clients have trust for the server certificate and therefor workaround with disabling server certificate validation is no longer needed.
It has to be installed under following location "Console Root\Certificates(Local Computer)\Trusted Root Certification Authorities\Certificates".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2016 12:19 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2016 01:00 PM
It could be that option "Do not prompt user to authorize new servers or trusted root certification authorities" is enabled on those device, something I would check first - cause that's the only setting in native supplicant that enforce user interaction on accepting/declining server certificate.
But since you have no control on client device, neither you want to configure those client - another option will be generate CSR (certificate signing request) on your NPS server and sign it with some well known CA. After that install signed certificate on NPS server and use it as server certificate for EAP authentication. Clients will have trust for that certificate as they have corresponding signing CA certificate under default trusted CA list.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 05:09 AM
Hi
First i apologies to posting my question here because i do not know whether i am reaching to right group or not .
Please help me if it is right place.
- AP 1552E with regulatory domain C (China, in 5Ghz band, it has 5 channels: 149, 153, 157, 161, 165)
- AP 1572E with regulatory domain F (Indonesia, in 5Ghz, it has 4 channels: 149, 153, 157, 161)
WLC SW version 8.1
Questions:
1. Can We combine those two AP in single MESH bridge group?
2. Is there any potential problem if we put AP 1572 domain F as RAP and AP 1552 domain C as MAP? The logic is channel will be driven by RAP, so it will avoid to use channel 165 as backbone MESH, is it correct logic?
3. Is there any potential problem to combine AP 1552 and AP 1572 model in single MESH network since they have different capability?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 06:14 AM
Hi Prakash,
You are in the right section :)
Answering your questions:
- Yes, you can combine APs from different RF domain and different AP models in same BGN (bridge group name)
- Normally, in the mesh world, channels are selected by the user for RAPs, and MAPs auto tune to RAP channels. In your question you are following this logic and if you configure 1572 domain -F as RAP with fixed channel, 1552 domain -C MAP will connect to it since it does scan on channels that RAP operates on.
- Yes, in case you have 1552 domain -C being parent or RAP and operating on channel 165, then 1572 domain -F MAP won't be able to connect to given parent or RAP. So careful planning is needed.
You can use 'Backhaul channel deselect' feature to minimize administrative overhead when configuring MESH deployment to ensure you RAP/MAP never select certain channel (in your case channel 165): Backhaul channel deselect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 06:27 AM
Thank you so much for your fast reply Roman.
I appreciate you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2016 02:26 AM
Hi Prakash,
Thanks for your feedback, glad to hear you found this information useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 06:56 AM
Hi Roman
We have a rule in each policy set in our ISE 2.1 deployment that deals with staff attempting to connect their personal devices to our wireless network.
Currenty it just responds with AccessReject but I was wondering if in addition to this I could also statically add the endpoint into a group as part of the authorization result?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 07:26 AM
Hi Martin,
Thanks for your question.
From what I know it's not possible to assign endpoint to certain group as part of authorization policy result. Authorization policies are a component of the Cisco ISE network authorization service. This service allows you to define authorization policies and configure authorization profiles for specific users and groups that access your network resources. They define permission on accessing certain network resources or do certain administrative actions.
If you need map client devices to certain device groups on ISE dynamically you should use profiling service. Based on your explanation you are interested to put personal devices in certain group, so probably best option would be to use AD probe and check condition 'AD-Host-Exists', then assign device to corresponding group if not found in AD.
Please refer to ISE profiling documentation for more details: Cisco ISE Endpoint Profiling Policies
I hope this information will be useful for you.
P.S: This section is related to Wireless LAN security, for your question more relevant topic will be in Security/AAA section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 07:31 AM
Is there any way to pull up or scroll through the speed dial list on the screen of the 9971?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 11:43 AM
Hi Kristina,
Unfortunately, I won't be able to answer your question since it's related to IP telephony and not to wireless technology.
I would recommend you to reach CUCM team regarding questions related to IP Phones functionality.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2016 08:25 AM
Hi,
On a 5508 WLC how can SSH Server CBC mode ciphers encryption be disabled and enable CTR or GCM cipher mode encryption?
Thank you.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

