- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Is your AP autonomous or
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
capture traffic radius and acct ... I need your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2016 04:28 AM - edited 07-05-2021 04:31 AM
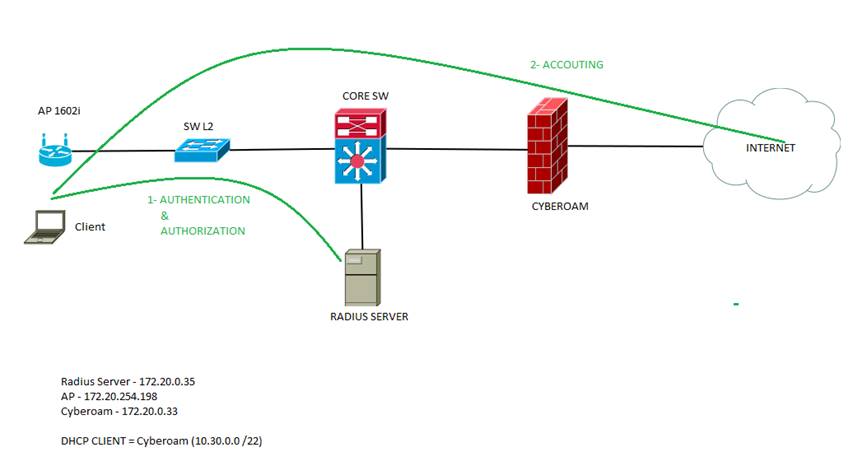
I need your help ... I need capture all the traffic that goes from a wireless client 802.1x to AP and the AP to RADIUS and Customer .
I connected a computer to a switch port where the AP is connected and configured as follows:
monitor session 1 source int f0 / 1
monitor session 1 des int f0 / 12
but only see Radius packets between the AP and the server ... I could not see accounting communications or DHCP REQ by the customer .
- Labels:
-
Other Wireless Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2016 12:27 PM
Is your AP autonomous or controller based?
___________________________________________________________
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2016 02:10 PM
is AP autonomous, cisco 1602i.
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2016 02:17 PM
If you are indeed sniffing the port the AP is connected to you should see all of this traffic. DHCP, Radius, etc. Do you have filters on your analyzer that may be preventing you from seeing this traffic?
___________________________________________________________
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2016 04:02 AM
I don't use any Filters ...the RADIUS server is a NPS of microsoft .
on the radius i have configured the accouting for Cyberoam ... but when I'm capturing the traffic , I don't see AP communication with Cyberoam ... but they have open communications ( active routes...for exemple ping OK)
i need configure a specify attribute on NPS for radius send USER-NAME in accounting packet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2016 08:49 AM
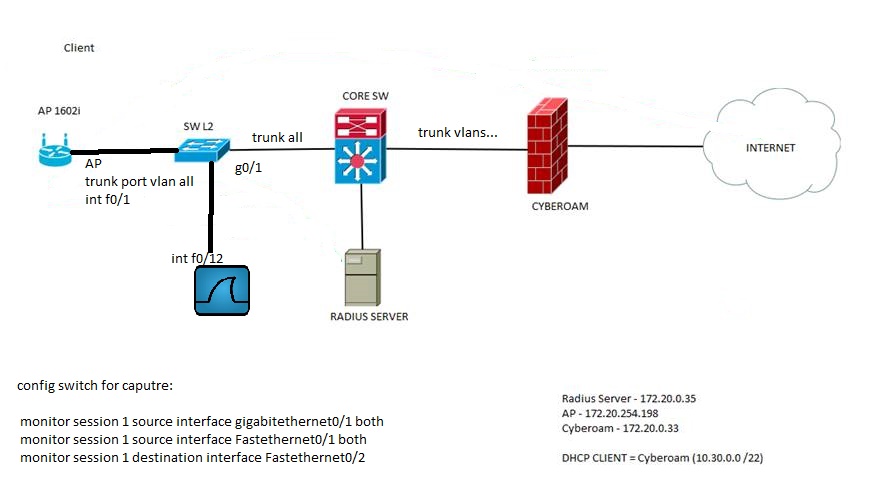
I made a new test:
SW
monitor session 1 source interface Fa0/1 both
monitor session 1 destination remote vlan 41
CORE
monitor session 1 source remote vlan 41
monitor session 1 destination interface g7/5
but I do not see traffic (accounting) from ap to cybroam!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2016 06:56 AM
resolved.
problema with AP (1602i) firmware ... upgraded to version ap1g2-k9w7-mx.152-4.JB6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2016 10:26 AM
the config on access point:
aaa group server tacacs+ tac_admin
server 172.20.254.1
aaa group server radius rad_eap
server name 172.20.0.35
aaa group server radius rad_mac
aaa group server radius rad_admin
aaa group server radius rad_pmip
aaa group server radius dummy
aaa group server radius rad_acct2
server name 172.20.0.33
aaa authentication login eap_methods group rad_eap
aaa authentication login EAP_MTD group rad_eap
aaa authentication login mac_methods local
aaa authorization exec default local
aaa accounting network acct_methods2 start-stop group rad_acct2
aaa session-id common
!
dot11 ssid Public
vlan 40
authentication open eap EAP_MTD
authentication network-eap EAP_MTD
authentication key-management wpa version 2
mbssid guest-mode
!
interface Dot11Radio0
encryption vlan 40 mode ciphers aes-ccm
ssid Public
interface Dot11Radio0.40
encapsulation dot1Q 40
no ip route-cache
bridge-group 40
bridge-group 40 subscriber-loop-control
bridge-group 40 spanning-disabled
bridge-group 40 block-unknown-source
no bridge-group 40 source-learning
no bridge-group 40 unicast-flooding
!
interface Dot11Radio1
encryption vlan 40 mode ciphers aes-ccm
ssid Public
interface Dot11Radio1.40
encapsulation dot1Q 40
no ip route-cache
bridge-group 40
bridge-group 40 subscriber-loop-control
bridge-group 40 spanning-disabled
bridge-group 40 block-unknown-source
no bridge-group 40 source-learning
no bridge-group 40 unicast-flooding
!
interface GigabitEthernet0.40
encapsulation dot1Q 40
no ip route-cache
bridge-group 40
bridge-group 40 spanning-disabled
no bridge-group 40 source-learning
!
interface BVI1
ip address 172.20.254.198 255.255.255.0
no ip route-cache
ip default-gateway 172.20.254.254
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 32 include-in-access-req
radius-server attribute 25 access-request include
radius-server timeout 10
radius-server vsa send accounting
radius-server vsa send authentication
!
radius server 172.20.0.33
address ipv4 172.20.0.33 auth-port 1645 acct-port 1813
key 7 XXXXXXXXXXXXXXXXXXXX
!
radius server 172.20.0.35
address ipv4 172.20.0.35 auth-port 1812 acct-port 1646
key 7 XXXXXXXXXXXXXXXXXXXXXXXXX
I don't understand how I can see accounting packages in wireshark...
help me!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
