- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Cisco 5760 - Anchor config issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 5760 - Anchor config issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2013 10:00 PM - edited 07-04-2021 12:57 AM
Hi,
I am having an issue where the 5760 Anchor WLC has 4 Subnets but half of the VLANS need to go to a seperate gateway and the other half to another gateway.
Below image is what the network looks like:
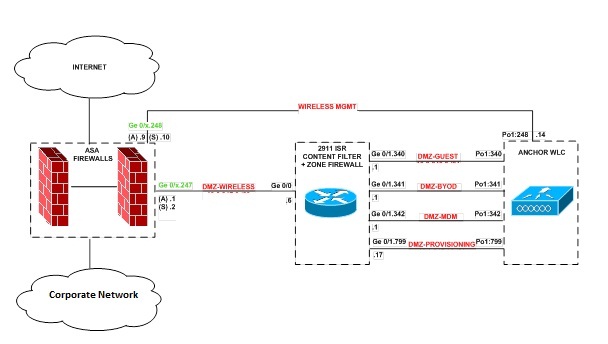
- The router (Content Filtering) is the Gateway for 4 x SSID’s/VLANs
- The Firewall is the Gateway for the Management VLAN
- The issue here is that we have 2 separate Gateways and there is no way to define separate gateways for each VLAN on the 5760 WLC
- We have an default IP route 0.0.0.0 0.0.0.0 10.1.1.254 which is pointing to the Firewall. The firewall is not the gateway for the other 4 x SSID/VLANs that exist on the Anchor so we do not want all traffic going to the Firewall, only management traffic.
Is there a way to set different gateways for different subnets/VLANs on the 5760 WLC? Keeping in mind that there is an default route pointing to the Firewall.
Also does the 5760 WLC acts as a Layer 3 device?
Thanks
- Labels:
-
Other Wireless Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2013 06:44 PM
All types of deployments listed below for the Anchor configuration.
Case solution :
Wireless WebAuth and Guest Anchor Solutions
The following sections show a WebAuthentication (WebAuth) configuration and Guest Anchor examples on the CT5760.
Note For a complete webauth configuration, please download the webauth bundle from the following URL: http://software.cisco.com/download/release.html?mdfid=284397235&softwareid=282791507&
release=3.2.2&relind=AVAILABLE&rellifecycle=&reltype=latest .The readme file has all the GUI and CLI configuration for webauth.
Configure Parameter-Map Section in Global Configuration
The parameter map connection configuration mode commands allow you to define a connection- type parameter map. After you create the connection parameter map, you can configure TCP, IP, and other settings for the map.
! First section is to define our global values and the internal Virtual Address.
! This should be common across all WCM nodes.
PARAMETER-MAP TYPE WEBAUTH GLOBAL?
VIRTUAL-IP IPV4 192.0.2.1
PARAMETER-MAP TYPE WEBAUTH WEBPARALOCAL?
TYPE WEBAUTH?
BANNER TEXT ^C WEBAUTHX^C
REDIRECT ON-SUCCESS HTTP://9.12.128.50/WEBAUTH/LOGINSUCCESS.HTML
REDIRECT PORTAL IPV4 9.12.128.50
Configure Customized WebAuth Tar Packages
Transfer each file to flash:
copy tftp://10.1.10.100/WebAuth/webauth/ webauth_consent.html flash:webauth_consent.html
copy tftp://10.1.10.100/WebAuth/ webauth_success.html flash: webauth_success.html
copy tftp://10.1.10.100/WebAuth/ webauth_failure.html flash: webauth_failure.html
copy tftp://10.1.10.100/WebAuth/ webauth_expired.html flash: webauth_expired.html
Configure Parameter Pap with Custom Pages
parameter-map type webauth webparalocal
type webauth
custom-page login device flash:webauth_consent.html
custom-page success device flash:webauth_success.html
custom-page failure device flash: webauth_failure.html
custom-page login expired device flash:webauth_expired.html
Configure Parameter Map with Type Consent and Email Options
parameter-map type webauth webparalocal
type consent
consent email
custom-page login device flash:webauth_consent.html
custom-page success device flash:webauth_success.html
custom-page failure device flash:webauth_failure.html
custom-page login expired device flash:webauth_expired.html
Configure Local WebAuth Authentication
username guest password guest123
aaa new model
dot1x system-auth-control
aaa authentication login EXT_AUTH local
aaa authorization network EXT_AUTH local
aaa authorization network default local
or
aaa authentication login default local
aaa authorization network default local
Configure External Radius for WebAuth
aaa new model
dot1x system-auth-control
aaa server radius dynamic-author ?
client 10.10.200.60 server-key cisco ?server-key cisco ?
auth-type any
radius server cisco
address ipv4 10.10.200.60 auth-port 1812 acct-port 1813
key cisco
aaa group server radius cisco server name cisco
aaa authentication login EXT_AUTH group cisco
or
aaa authentication login default group cisco
Configure WLAN with WebAuth
wlan Guest-WbAuth 3 Guest-WbAuth
client vlan 100
mobility anchor 192.168.5.1
no security wpa
no security wpa akm dot1x
no security wpa wpa2
no security wpa wpa2 ciphers aes
security web-auth
security web-auth authentication-list EXT_AUTH
security web-auth parameter-map webparalocal
no shutdown
Configure HTTP Server in Global Configuration
!--- These are needed to enable Web Services in the Cisco IOS® software.
ip http server
ip http secure-server
ip http active-session-modules none
Other Configurations to be Checked or Enabled
!--- These are some global housekeeping Cisco IOS® software commands:
ip device tracking
ip dhcp snooping
SNMP Configuration
From the CT5760 console, configure the SNMP strings.
snmp---s er v er co mmuni t y p ub l i c r o
snmp---s er v er co mmuni t y p r i v a t e r w
IPv6 Configuration
IPv6 is supported on the data path. Wireless clients will be able to get an IPv6 address.
Enable IPv6 Snooping - CT5760
There are slight differences in configurations on a CT5760 when configuring IPv6. To enable IPv6 on a CT5760, the following step must be completed.
ipv6 nd raguard attach-policy testgaurd
Trusted-port
Device-role router
interface TenGigabitEthernet1/0/1
description Uplink to Core Switch
switchport trunk native vlan 200
switchport mode trunk
ipv6 nd raguard attach-policy testgaurd
ip dhcp snooping trust
Enable IPv6 on Interface - CT5760
Based on interfaces that need IPv6 configurations and the type of address needed, respective configurations are enabled as follows. IPv6 configurations are enabled on VLAN200.
vlan configuration 100 200
ipv6 nd suppress
ipv6 snooping
interface Vlan100
description Client VLAN
ip address 10.10.100.5 255.255.255.0
ip helper-address 10.10.100.1 2001:DB8:0:10::1/64
ipv6 address FEC0:20:21::1/64
ipv6 enable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2014 08:45 AM
Hi Koevi,
I know it is almost two years since your post but I would like to know if you were able to solve this issue.
I have configured 3 GUEST SSIDs on a 5760 Anchor behind an ASA FW. The 5760 has 3 SVI (Interface VLAN 11, 12 and 13) as default gateway for the 3 Guest Client VLANs. Therefore when a client connects to, for example, GUEST1 will get an IP in VLAN 11 and the default gateway will be the SVI VLAN 11 configured on the 5760 (it has been configured as DHCP server too). From there, the client traffic will match the default route configured in the 5760 to go to the L3 outbound interface of the Firewall:
https://supportforums.cisco.com/thread/2270522?tstart=0
As a client I can ping any IP configured on the 5760 but I cannot get any further on the network (even to the IP in the other side of a link - same network). However, from the 5760 I can ping any IP with no problem at all. It seems to be something within the 5760.
Did you find out whether the 5760 is able to do routing? Do I need to enable any specific thing? I don’t see what is wrong...
It would be great if you can help me.
Thank you very much.
Joana.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
