- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Cisco Mobility Express 8.10.130 and CWA with ISE Guest Portal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Mobility Express 8.10.130 and CWA with ISE Guest Portal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 12:01 AM - edited 07-05-2021 12:36 PM
Hello all, I need some advise.
I am trying to set up a Guest WLAN on Mobility Express with the ability to authorize guests through a ISE Guest Portal(Sponsored or any other kind).
I have ME 8.5.151 and i purposely upgrade it to 8.10.130.
But in this version i does not see ability to attach url_redirect ACL/pre-auth acl to WLAN. I created redirect ACL under advanced security setting, but i does not see how to map it to WLAN
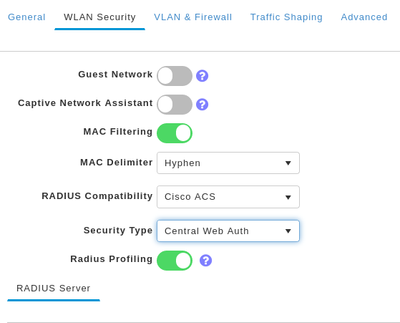
WLAN Security Settings(will see that no options for redirect acl and preauth acl):
Redirect ACL:
but in ME version 8.8.100 i see these options (automatic generated redirect ACL and ability to create preauth-acl).
Can I setup Guest WLAN with ISE Guest Portal in this version(8.10.130), or should I upgrade/downgrade to some other verison?
- Labels:
-
Mobility Express
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 10:59 AM
Have you resolved this issue yet? I am attempting the same configurations and there is a lack of documentation to cover this use case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 07:29 PM
Maybe you can refer to this deployment example:
LWA and CWA for Cisco WLC and Mobility Express
https://timnetworks.rs/wpe/2019/07/01/lwa-and-cwa-for-cisco-wlc-and-mobility-express/
Rps-Cheers | If it solves your problem, please mark as answer. Thanks !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2021 06:11 AM
Rps-Cheers
That was a good article but did not resolve the issue in 8.10.151.0. The support to add an ACL via the CLI seems to have been disabled.
(Cisco Controller) >config (Cisco Controller) config>flexconnect acl rule add me_cwa_acl_redirect_1 1 Error! Invalid ACL name. (Cisco Controller) config>flexconnect acl rule add ? <name> Enter IPv4 ACL name up to 32 alphanumeric characters. (Cisco Controller) config>flexconnect acl rule add test ? <index> Enter rule index between 1 and 64. (Cisco Controller) config>flexconnect acl rule add test 1 Error! Invalid ACL name.
However, In the Cisco Mobility Express User Guide, Cisco Wireless Release 8.10 on page 115 section "Applying the ACL to WLAN at Pre-Auth Level" It has you apply the ACL via the GUI.. I am going to try the following sections of the doc and see what happens.
Applying the ACL to WLAN at Pre-Auth Level
Applying the ACL to WLAN at Post-Auth Level
Configuring AAA Override in WLAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2021 08:11 AM
I think you should create ACL first and then add Rule.
eg.
(Cisco Controller) >config flexconnect acl create test (Cisco Controller) >config flexconnect acl rule add test 1 (Cisco Controller) >config flexconnect acl apply test
Rps-Cheers | If it solves your problem, please mark as answer. Thanks !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2021 02:14 PM
Rps,
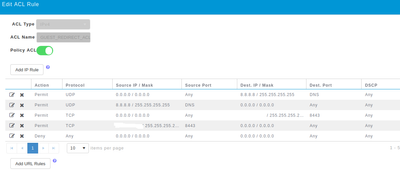
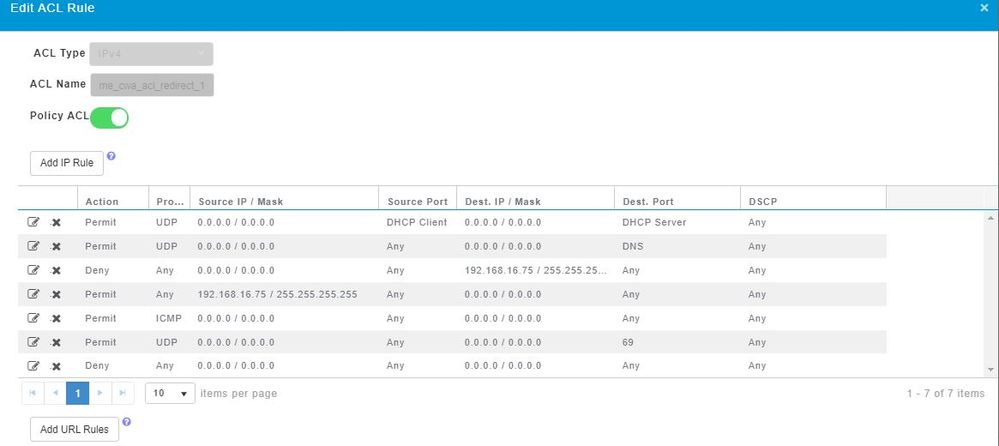
I apologize for the delay in getting back to you on this one. I had other fires to put out. So in the meantime I turned up another AP with mobility express with 8.7 code configured per the instructions and it worked. So then I upgraded it to 8.10.151.0. After the upgrade it did not work due the the ACL entries being wiped out during the upgrade process but the ACL was still configured without any entries. So I added the entries into the me_cwa_acl_redirect_1 Pre-auth acl and it started working again on the test AP. Next I copied the configuration to the existing WLC and setup a WLAN exactly like the test AP. The communication seems to be good between the ISE server and ME controller however the client gets the redirect but does not connect to the URL. Packet captures show the communication between the controller and ISE and within ISE I can see the authentication and redirect. It almost seems like a DNS issue but the host is resolvable from the client when doing a nslookup.
redirected URL from the client browser:
https://<HOSTNAME_REMOVED>:8443/portal/gateway?sessionId=03c7a8c00000097f5c730061&portal=50fbc805-6bde-4e28-8a3e-17750f938538&action=cwa&token=aa55c495b3a9f70a9dd74aeba8e57477&redirect=www.msftconnecttest.com/redirect
Windows IPCONFIG Output while connected to SSID OPEN:
Wireless LAN adapter Wi-Fi:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.225.46
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.225.1
C:\Users\VernonNelson>nslookup <HOSTNAME_REMOVED>
Server: <DNS_SERVER_NAME_REMOVED>
Address: 192.168.16.15
Name: <HOSTNAME_REMOVED>
Address: 192.168.16.75
PRE-AUTH ACL
Any ideas on where to go next would be great. Downgrading to 10.7 then back up may be an option but would prefer not to have the downtime in production.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2021 06:44 PM
Maybe you can refer to the following link to set up RADIUS Server and ACL.
Rps-Cheers | If it solves your problem, please mark as answer. Thanks !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2021 06:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2025 06:01 AM
Hello everyone,
i am trying to configure on the wlc mobility express (version: 8.10.196.0) a connection the same as yours that connects to the cisco ISE and then redirects to the web page where the user and password are asked to be created by us. I have tried following your steps but to no avail. By any chance can you tell me on this version how should I set up the acl redirect and how should I create the guest ssid?
Thank you
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide