- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Flexconnect VLAN Based Central Switching
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Flexconnect VLAN Based Central Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2018 06:19 AM - edited 07-05-2021 09:01 AM
Hi,
I am new to Wireless networks and a I have some clarifications.
I have a scenario wherein my client needs to upgrade to a new WLC 5520. They have a two sets of 5508 WLC. One pair is configured for HQ office and another pair is for Remote Sites. HQ APs are pointed to HQ WLC and Remote APs to REMOTE WLC.
HQ is setup as LOCAL MODE (central switched)
REMOTE is setup as FLEXCONNECT (local switched)
HQ and REMOTE WLC have the same SSID for the sake of this post let just say the SSID is "WLAN_NAC". WLAN users are authenticated through a NAC appliance and NAC will dictate based on policy which vlan they will belong. This WLAN "WLAN_NAC" is associated to the WLC management interface.
However, based on their current setup they have few dynamic vlan interfaces configured but it's not associated to any WLAN. Does this mean the WLC is not using this interfaces?
I am studying on what would be the best approach for migration. Below are my queries and clarifications.
1. Is it possible to maintain the same "WLAN_NAC" SSID
2. Enable AAA Override, Flexconnect Local Switching and VLAN Based Central Switching on "WLAN_NAC"
Traffic Flow:
a. HQ user will connect to WLAN_NAC ssid after it passed the NAC posture check, NAC will assign the user to vlan 231 and will be centrally switch.
b. Remote user will connect to WLAN_NAC ssid after it passed the NAC posture check, NAC will assign the user to vlan 250 and will be local switch.
3. Create a flexconnect group for Remote Sites and configure AAA VLAN ACL Mapping. Map the vlan 250 for local switching.
4. Create a flexconnect group for HQ, but no AAA VLAN ACL Mapping configuration. If HQ user connects to WLAN_NAC ssid, and NAC assign the user to vlan 250 for example, will it be centrally switched? What IP address will the user gets? is it from VLAN 250 subnet or WLC MGMT Subnet? I read an article that states that, "if vlan is not configured it will use a default vlan" what is the default vlan?
Thanks in advanced for the time and support.
- Labels:
-
Aironet Access Points
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2018 09:34 AM - edited 08-22-2018 09:35 AM
All the answers are here -
Traffic flow on WLANs configured for Local Switching when FlexConnect APs are in connected mode are as follows:
- If the VLAN is returned as one of the AAA attributes and that VLAN is not present in the FlexConnect AP database, traffic will switch centrally and the client is assigned this VLAN/Interface returned from the AAA server provided that the VLAN exists on the WLC.
- If the VLAN is returned as one of the AAA attributes and that VLAN is not present in the FlexConnect AP database, traffic will switch centrally. If that VLAN is also not present on the WLC, the client will be assigned a VLAN/Interface mapped to a WLAN on the WLC.
- If the VLAN is returned as one of the AAA attributes and that VLAN is present in the FlexConnect AP database, traffic will switch locally.
- If the VLAN is not returned from the AAA server, the client is assigned a WLAN mapped VLAN on that FlexConnect AP and traffic is switched locally.
In short, RADIUS returns a VLAN number when the User Auths. If the VLAN exists on the AP, they get switched at the AP. If it doesn't exist on the AP but it does exist on the WLC, it gets switched on that VLAN at the WLC. If it doesn't exist on the AP or WLC, the user gets switched at the WLC using the Default VLAN for the SSID as defined in the WLC's config. Remeber that AP Group (if applicable) will override the default config you see in the SSID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2018 09:38 AM
Details here:
When the User Auths the RADIUS Server returns a VLAN ID. If the VLAN is found to exist at the AP, the User gets switched at the AP. If the VLAN does not exist at the AP but it does exist in the WLC, the Client gets switched via that VLAN through the WLC. If the VLAN does not exist on the AP or the WLC, the Client gets switched at the WLC using the default VLAN defined for that SSID. Remember that if AP Groups are configured, those VLAN settings will override the default ones you see in the Global SSID definition.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 05:12 AM
Hi Richard,
Thank you for your prompt response. I have another inquiry about your statement below.
If the VLAN does not exist at the AP but it does exist in the WLC, the Client gets switched via that VLAN through the WLC.
My setup is as follows:
WLC Dynamic Interface
User VLAN: 133
Quarantine VLAN: 103
Management VLAN: 125
Radius/Remediation Server VLAN: 203
Vlan 133, Vlan 103, Vlan 125 and Vlan 203 are configured as SVI in the firewall. Each SVI is consider as one zone.
AP--ACCESS SWITCH--CORE SWITCH--WLC
|
|
FIREWALL----RADIUS/REMEDIATION SERVER
The AP is connected to an access switch via trunk port, allow all vlan 133,103,125 and native vlan as 125. WLC is connected onto the core switch as trunk port and allow all vlan 133,103,125. The radius/remediation is behind the firewall.
My SSID and AP are flexconnect mode. I do not have ACL AAA VLAN MAPPING configured inside the flexconnect group. So all my traffic will be centrally switched. The radius server returned a vlan value of vlan 103 quarantine as expected, but after that the test laptop stuck in vlan 103 and was not able to reach the remediation server (this is also the radius server) radius and remediation server is just one appliance. With this being said, the radius/remediation wont return a user vlan id coz it was not able to validate the posture check.
My question now, if all my data traffic is tunneled inside the capwap data through the wlc. my data traffic is going through the wlc before it get switched and will performed normal routing on the firewall?
From the firewall logs, the traffic flow was; source ip: laptop vlan 103 subnet-192.168.103.103 destination ip: Remediation server 192.168.203.10. But the outgoing interface used to reach the server was WLC management zone, instead of Quarantine Vlan zone and so it is being dropped. Is this the correct behavior?
I tested the same traffic flow using Local Mode and everything is working. After the radius assigned a vlan 103 the test laptop was able to reach the radius/remediation server so the radius returned a user vlan id after it pass the posture check. Same result also if I did a flexconnect local switching. All traffic is going to the correct zone. (quarantine zone to radius/remediation server zone)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 06:23 AM
In the SSID, have you enabled the 'allow aaa override' and 'ISE RADIUS NAC' options (both under the advanced tab)?
Also, if you review the Client's connection information (via "Monitor > Clients" in the GUI, then drill down to the particular Client you're testing with) - does the WLC say it is mapping the Client to the expected Interface?
Lastly, and just thinking forwards to the next step (putting back in proper VLAN after remediation), did you setup the RADIUS Servers to support CoA when you defined them in the WLC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 07:10 AM - edited 08-24-2018 07:16 AM
Hi Richard,
First, we are using Aruba Clearpass Policy Manager as Radius/Remediation.
does the WLC say it is mapping the Client to the expected Interface? - Yes we are seeing the user is on quarantine vlan (vlan 103). And its stuck there. From the clearpass onguard agent, it cannot reach the clearpass server. From here I know that there's something wrong on the routing/switching but I cannot pinpoint where it is. Coz if I configure the wireless as local switching or local mode everything works fine. Btw, we are using WLC 5520 version 8.3.143 and AP is 1852E.
allow aaa override and vlan based central switching - is enabled.
'ISE RADIUS NAC' options - i cannot enabled this it gives me an error ( Unable to set the Radius NAC state). and we are not also using ISE. So I am not sure if this is applicable to my setup. Even though this is not enabled, flexconnect local switching and local mode is working. Only flexconnect central switching that is giving me this problem.
did you setup the RADIUS Servers to support CoA when you defined them in the WLC?- Yes, CoA is enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 10:43 AM
ISE / Clearpass - basically the same thing as they both use RADIUS CoA. Do look up Cisco's ISE/WLC integration guides.
Not being able to set the ISE NAC thing will cause you problems in the long run, although not necessarily causing this problem, so you do need to get to the bottom of that. Do you have RADIUS Accounting Servers defined?
Are you imposing any ACLs dynamically? Have you tried setting it to Permit IP Any Any just to get it working?
If you create an open SSID on VLAN 103 (ie, without any RADIUS, ACLs, etc on the WLC) - can you connect to your remediation server? If you can't connect even in this state, it's a VLAN/IP/FW issue.
Let us know how you get on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 11:35 PM
Hi Richard,
I cannot enable the ISE NAC when vlan-based-central switching is enabled and vise-versa. If I enable vlan-based-central switching I am getting an error below.
"The following errors occurred while updating the WLAN: VLAN Based Central Switching is not supported when any Layer 3 web redirect security type is enabled"
Are you imposing any ACLs dynamically? - None.
If you create an open SSID on VLAN 103 (ie, without any RADIUS, ACLs, etc on the WLC) - can you connect to your remediation server? - yes it is reachable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2018 02:31 PM
Hey guys, have you got to the bottom of this issue. I am having exactly same problem with cisco 5500. if both Data and Remediation are locally switched then all good also if both are centrally switched but when I try to do the remediation centrally and Data locally then the AP is ignoring the VLAN tag coming from Cisco ISE and put the client direct into Data VLAN. it behaves like before the "VLAN Based Central Switching" has been introduced!!!
I had veriosn 8.3 then upgrade to latest version 8.5 but still no joy :(
thoughts !!
Thanks,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2019 04:58 PM
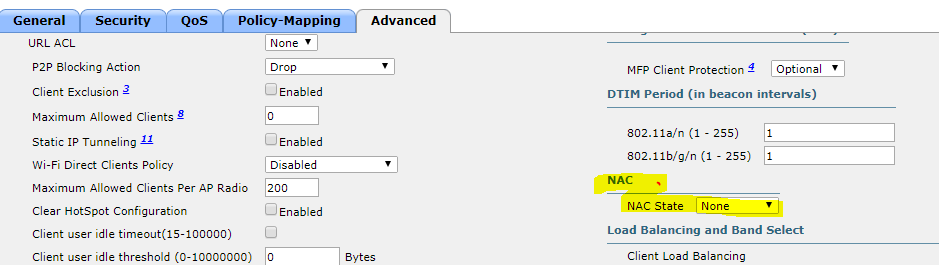
Disable NAC State.
WLAN (id) > Advanced > NAC state to none.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide