- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- M2 MAC Pro WiFi 6e Fails to join when Fast Transition set to ADAPTIVE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2023 11:55 PM
Latest M2, M2Max, M2Pro, MAC Book Pro WiFi 6E cannot connect to Cisco WiFi when Fast Transition (FT) is set to "Adaptive"
Is anyone else having issues with the Latest M2 Mac Book Pros (with WiFi 6E) not connecting to Cisco AIROS Controller-based Networks if Fast Transition (FT) is set to ADAPTIVE? Tested on the Latest 8.10.183.0 with 9130,3800,3700 Series AP. Also Tested on 8.5.182.2 with 3600 series APs. Other Mac and IOS devices work fine.
No other vendor can support Adaptive mode, it is proprietary to Cisco and Apple. The result is that all non-iOS devices (inc MacOS < v12 ) will connect and roam without FT. But iOS devices can “Adapt” (upscale) their ‘Authentication and Key Management’ suite (AKM) to connect with FT even though the SSID does not support it.
If the SSID FT option is set to ENABLED the M2 WiFi6e device can connect.
If the SSID FT option is set to DISABLED the M2 WiFi6e device can connect.
The devices ASSOCIATES and does 802.1x Auth but then cannot get an IP address and gets self-assigned IP then disconnects. This is all happening on WiFi 5Ghz (no 6Ghz)
from the apple site
802.11r
When your device roams from one AP to another on the same network, 802.11r uses a feature called Fast Basic Service Set Transition (FT) to authenticate more quickly. FT works with both pre-shared key (PSK) and 802.1X authentication methods. iOS 10 and later, iPadOS and macOS 12 include support for adaptive 802.11r on Cisco wireless networks. Adaptive 802.11r offers FT without the need to enable 802.11r on the configured Cisco wireless network. To support adaptive 802.11r, the Cisco network must be using controller code version 8.3 or later.
Solved! Go to Solution.
- Labels:
-
Wi-Fi 6
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2023 12:40 AM - edited 02-14-2023 12:41 AM
Hi,
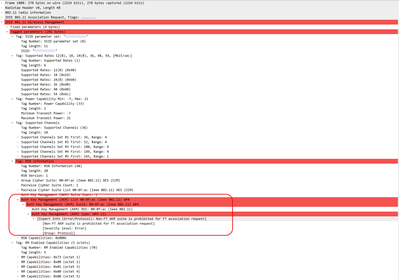
I have found the problem, and I have found the solution. The issue seems to be that the MacBook fails when you have CCKM turned on (CCKM authentication key management will be deprecated soon.) and I used tools like Metageek Tonic to see the same result you got, it loops a couple of times before leaving the BSS. Then I turned off CCKM since I am used to that being disabled on a C9800 controller with a warning that it will de deprecated soon.
Below is a capture in Tonic, where we see the "loop" and I looked in the pcap and got the same fault you got.
[Non-FT AKM suite is prohibited for FT association request]
So, after it was turned off. My Macbook Pro 2023 can successfully join my FT-adaptive SSID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 06:56 PM
Apple has fixed this bug on MAC OS 13.4.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 12:03 AM
- Try client debugging for those clients who can not connect : https://www.cisco.com/c/en/us/support/docs/wireless/aironet-1200-series/100260-wlc-debug-client.html , you can have debugs analyzed with : https://cway.cisco.com/wireless-debug-analyzer/
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 12:12 AM - edited 02-10-2023 12:25 AM
Already done that below is when FT set to ADAPTIVE.... (Next is to get a traffic wireless AIR Capture)
| Client made new Association to AP/BSSID BSSID AP |
| WLC recognizes that the client is 802.11r-capable |
| The WLC/AP has found from client association request Information Element that claims PMKID Caching support |
| The Reassociation Request from the client comes with 0 PMKID |
| Client has successfully cleared AP association phase |
| WLC/AP is sending an Association Response to the client with status code 0 = Successful association |
| Client will be required to Reauthenticate in 0 |
| seconds |
| WLC/AP is sending EAP-Identity-Request to the client |
| RADIUS Server permitted access |
| Client will be required to Reauthenticate in 0 |
| 4-Way PTK Handshake, Sending M1 |
| 4-Way PTK Handshake, Received M2 |
| 4-Way PTK Handshake, Client did not respond with M2 |
| 4-Way PTK Handshake, Retransmitting M1 retry #1 |
| 4-Way PTK Handshake, Received M2 |
| 4-Way PTK Handshake, Client did not respond with M2 |
| 4-Way PTK Handshake, Retransmitting M1 retry #2 |
| 4-Way PTK Handshake, Received M2 |
| 4-Way PTK Handshake, Client did not respond with M2 |
| 4-Way PTK Handshake, Retransmitting M1 retry #3 |
| 4-Way PTK Handshake, Received M2 |
| 4-Way PTK Handshake, Client did not respond with M2 |
| 4-Way PTK Handshake, Retransmitting M1 retry #4 |
| 4-Way PTK Handshake, Client did not respond with M2 |
| Client has been deauthenticated |
| Client expiration timer code set for 10 seconds. The reason: Roaming failed due to WLAN security policy mismatch between controllers (configuration error). It can also be used to report EAPoL retry errors, and GTK rotation failure (in 8.5) |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 12:24 AM
This is the log when FT is set to enabled.
| Client made new Association to AP/BSSID BSSID AP |
| WLC recognizes that the client is 802.11r-capable |
| The WLC/AP has found from client association request Information Element that claims PMKID Caching support |
| Client is entering the 802.1x or PSK Authentication state |
| Client has successfully cleared AP association phase |
| WLC/AP is sending an Association Response to the client with status code 0 = Successful association |
| Client will be required to Reauthenticate in 0 |
| seconds |
| WLC/AP is sending EAP-Identity-Request to the client |
| Client sent EAP-Identity-Response to WLC/AP |
| RADIUS Server permitted access |
| Client will be required to Reauthenticate in 0 |
| seconds |
| WLC creates a PMK cache entry for this client, which is used for FT with AKM:802.1xin this case, so the PMKID is computed with the AP MAC address |
| 4-Way PTK Handshake, Sending M1 |
| 4-Way PTK Handshake, Received M2 |
| 4-Way PTK Handshake, Sending M3 |
| Client has completed PSK Dot1x or WEP authentication phase |
| Client has entered DHCP Required state |
| Received DHCP request from client |
| WLC begins FT fast-secure roaming over-the-Air with this client and performs a type of preauthentication, because the client asks for this with FT on the Authentication frame that is sent to the new AP over-the-Air (before the Reassociation Request). |
| Local roaming event triggered with the new AP to which the client roams. |
| WLC recognizes that the client is 802.11r-capable |
| FT fast-secure roaming is successful for this client. |
| Client is entering the 802.1x or PSK Authentication state |
| WLC/AP is sending an Association Response to the client with status code 0 = Successful association |
| Client has completed PSK Dot1x or WEP authentication phase |
| Received DHCP request from client |
| Received DHCP OFFER from DHCP server |
| Received DHCP request from client |
| Received DHCP ACK from DHCP server |
| Client has entered RUN state |
| Received DHCP ACK, assigning IP Address x.x.x.x |
| Received DHCP ACK from DHCP server |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2023 03:00 AM
This seems like a Client issue when using ADAPTIVE mode as AP is retransmitting M1 (it's not receiving the right M2 as the debug says there is an M2).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2023 03:02 PM
Hi,
Strange that you are allowed to use adaptive at all. Since WPA3-SAE does not support FT, so you have to set it to disabled. In later versions you will have FT+SAE (Don't know if that is supported on Aireos) but with FT+SAE you have to set it to Enabled. It's no such thing as Adaptive WPA3-SAE on a C9800 for example.
Added pictures from a C9800.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2023 08:57 PM
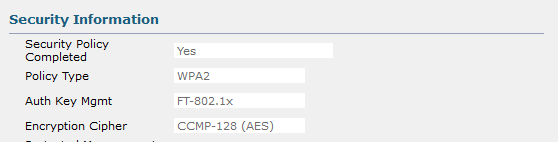
Thank you for this info and the pictures. In My case using a Cisco AIROS Controller 8.10.183.0 and there is No 6GHz or SAE or OWE
It is just simple 2.4 Ghz and 5 Ghz WiFi 4,5,6 With WPA2 AES Other MAC >v12 and IOS devices and New Samsung work fine. It is just the new M2 Based Mac Book Pro that does not. When FT is set to ADAPTIVE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 03:39 AM
Thank you! I have now because of you renewed my ISE license, and renewed my Windows Server 2022 license that had 1 day left on them.
Then I have configured a WPA2/3-Enterprise SSID with FT-Adapitve and my MacBook Pro 2023 model (with 6E) joined both 2.4 and 5GHz. My telemetry data say the client supports FT. I captured the association with my WlanPi, and I see that FT is enabled in the beacon. This was tested on 9136 and 9166, I have a 9120 I can test with later and maybe turn on my virtual AireOS, been a while.
Added a picture from my configuration on a 9800, and a picture of a probe response where we se Mobility Domain IE, and AKM-suite WPA meant for non-FT clients. This seems to work, but I would need to roam after I have charged the battery a bit to see it working in action. Will comment on that later.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 04:09 AM - edited 02-12-2023 04:20 AM
Thank you for confirming that it is not a problem with CAT OS (could you try with WPA3 not ticked and protected management frames disabled) it would be great if you could test with AIROS and 9120. I have tried with two controllers AIROS CONTROLLERS. Latest 8.10.183.0 with 9130,3800,3700 Series APs. Also Tested on 8.5.182.2 with 3600 series APs and both times can not get M2 Macbook pro to join with same debug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 06:55 AM - edited 02-12-2023 06:56 AM
I regret I did not have a capture going on at this point, this is what happened.
- I turned off WPA3, and set PMF to disabled
- I tried joining the SSID and I got a popup from MacOS saying it could not join this network, but it still joined but jumped back to a different SSID a few seconds later.
- Then I tried joining a different SSID then back again, but then MacOS got stuck loading the adaptive SSID constantly, and the weird thing is that it continued to load that SSID even if I joined a different one.
- I could not get that loading away, so I had to disable the 9120 and turn it back on so MacOS could not hear the adaptive SSID anymore (I could have disabled the SSID, but I was already in the AP config menu). Turn off and on the WLAN card on the MacBook did not work, each time It joined a working SSID but loaded the adaptive SSID in the background (clearly a bug)
- Turned off and on WLAN on the MacOS again after I had disabled the AP and enabled it again, and now it works with WPA2, PMF Disabled and FT-adaptive but wow that was unstable.
I have yet to get a working ft-enabled or ft-adaptive roam to work, I got an error that the controller could not validate the PMKID for fast roaming for example. Below is from the debug when it started working. I will have the debug running, and do a bit more captures.
| 2023/02/12 15:37:35.790 | dot11 | Association success for client, assigned AID is: 1 |
| 2023/02/12 15:37:35.790 | client-orch-sm | Client started layer 2 authentication (either dot1X or PSK) |
| 2023/02/12 15:37:35.794 | client-auth | Entering 802.1X authentication process |
| 2023/02/12 15:37:36.473 | client-auth | Starting EAPOL 4-Way Handshake |
| 2023/02/12 15:37:36.474 | client-keymgmt | Sent M1 for EAPOL 4-Way Handshake |
| 2023/02/12 15:37:36.479 | client-keymgmt | Received and validated M2 for EAPOL 4-Way Handshake |
| 2023/02/12 15:37:36.479 | client-keymgmt | Sent M3 for EAPOL 4-Way Handshake |
| 2023/02/12 15:37:36.482 | client-keymgmt | Received and validated M4 for EAPOL 4-Way Handshake |
| 2023/02/12 15:37:36.482 | client-keymgmt | Negotiated the following encryption mechanism: AKM:11W-DOT1X Cipher:CCMP WPA Version: WPA2 |
| 2023/02/12 15:37:36.482 | client-orch-sm | Client passed layer 2 authentication |
| 2023/02/12 15:37:36.482 | client-orch-sm | Policy profile is configured for local switching |
| 2023/02/12 15:37:36.482 | client-orch-state | Starting Mobility Anchor discovery for client |
| 2023/02/12 15:37:36.487 | client-orch-state | Entering IP learn state |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2023 11:25 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 12:26 AM
Interesting! I will bring up my vWLC lab this week and test. When I test it works all the time, but I have a yet to get a working FT roaming happening. But our config is now pretty similar. None of my captures mentioned this, good find!
If you could share all the WLAN config, then I will replicate at home with all APs I can find.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 03:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 04:13 PM
Confirmed this is also an issue with the new IPAD Pro M2 with (WiFi 6e chipset) Waiting to test a MAC M2 Mini (with WiFi 6e chipset)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2023 12:40 AM - edited 02-14-2023 12:41 AM
Hi,
I have found the problem, and I have found the solution. The issue seems to be that the MacBook fails when you have CCKM turned on (CCKM authentication key management will be deprecated soon.) and I used tools like Metageek Tonic to see the same result you got, it loops a couple of times before leaving the BSS. Then I turned off CCKM since I am used to that being disabled on a C9800 controller with a warning that it will de deprecated soon.
Below is a capture in Tonic, where we see the "loop" and I looked in the pcap and got the same fault you got.
[Non-FT AKM suite is prohibited for FT association request]
So, after it was turned off. My Macbook Pro 2023 can successfully join my FT-adaptive SSID.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide