- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Wireless 5508 802.1x Part 2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2011 08:04 AM - edited 07-03-2021 09:15 PM
With stephens help I was able to get most of my Wireless 802.1x setup configured properly. I'm not having a problem with the client authenticating using user/pass credentials. I have a Wireless XP Client (testing with), which connects to a LWAP, which connects to a WLC 5508, and then Cisco ACS for authentication. I put in my user credentials of tylerp (test account) with the correct password but nothing happens, it just keeps asking me to enter in
credentials after a few seconds. I started Wireshark on my laptop and I can see the following.
Source
Cisco_1e:3a:8f
Destination
IntelCor_85:9e:46
Protocol
EAP
Information
Request, Identity [RFC3748]
It looks like it's asking the client for credentials but when I submit my credentials I dont see any response via wireshark. I'm not sure why that is.
I have included several photos from my WLC/ACS configuration. Any help would be great!
Solved! Go to Solution.
- Labels:
-
Wireless Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 08:16 AM
In the client, which setting did you pick? Microsoft Protected EAP (PEAP) or Microsoft Smart card or other certificate?
for PEAP it should look like this. You can uncheck the Validate server certificate box, so you don't need to push the ACS cert while testing.
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 08:40 AM
Looks like we're making progress here. Here is a new monitor log from the ACS.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 08:46 AM
ok, so still getting the Selcted Identity Source is Deny access. In the policy, are you allowing AD? And in the AD config of the client, did you select the grant dial-in permissions?
HTH,
Steve
----------------------------------------------------------------------------------------------------------
Please remember to rate helpful posts or to mark the question as answered so that it can be found later.
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 09:00 AM

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 09:09 AM
You are not hitting your SecureWireless profile. You need to define your network access policy better so that ACS can differentiate between that policy and the SecureWireless.
Thanks,
Scott Fella
Sent from my iPhone
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 09:16 AM

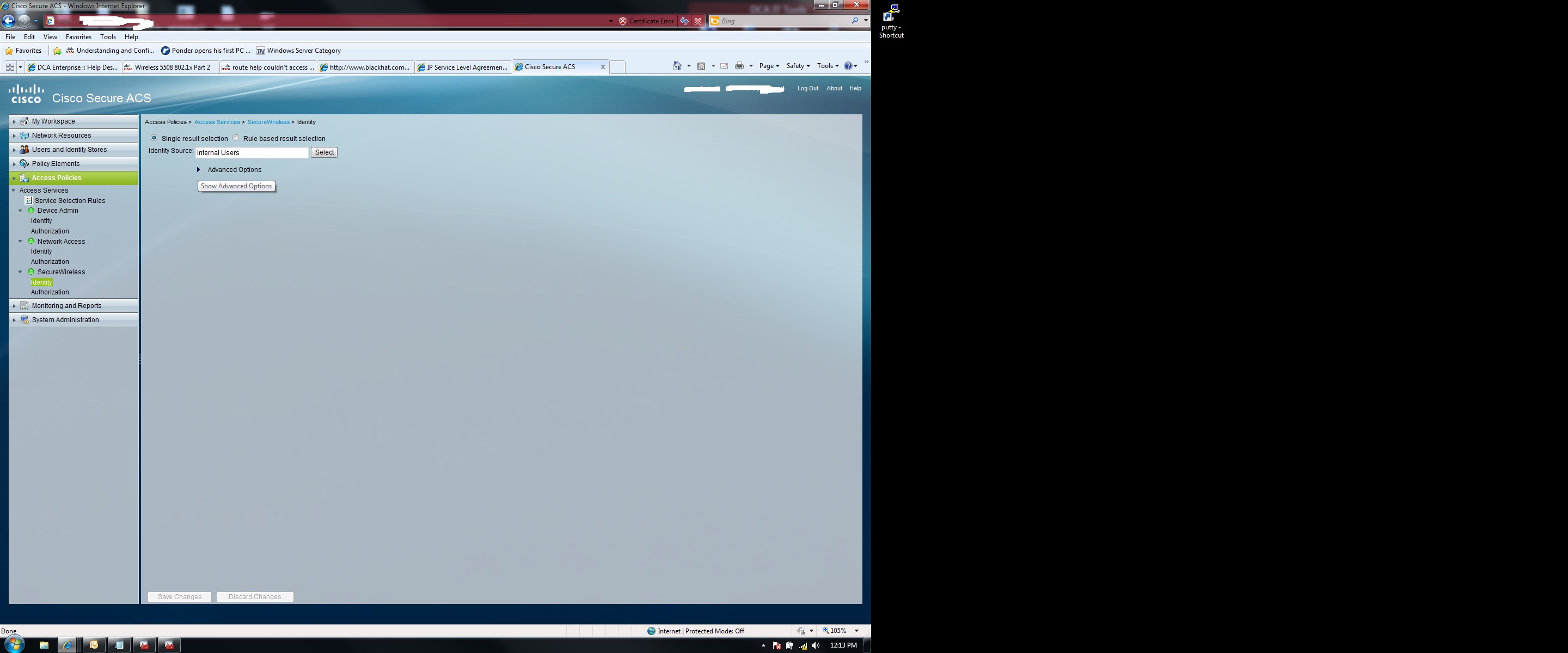
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 09:56 AM
What is using the network access policy? Can you disable that for the mean time just to see if the SecureWireless policy is being hit.
Sent from Cisco Technical Support iPhone App
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 10:37 AM
Did you add the WLC to its own NDG? I see that your network access policy is for your VPN and your rule base is using NDG and VPN Database, but your wireless is hitting that policy. For your network access policy, you can add a lookup for nas ip address and use the ip of your VPN device. That should make it hit your SecureWireless policy.
Sent from Cisco Technical Support iPhone App
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 12:09 PM
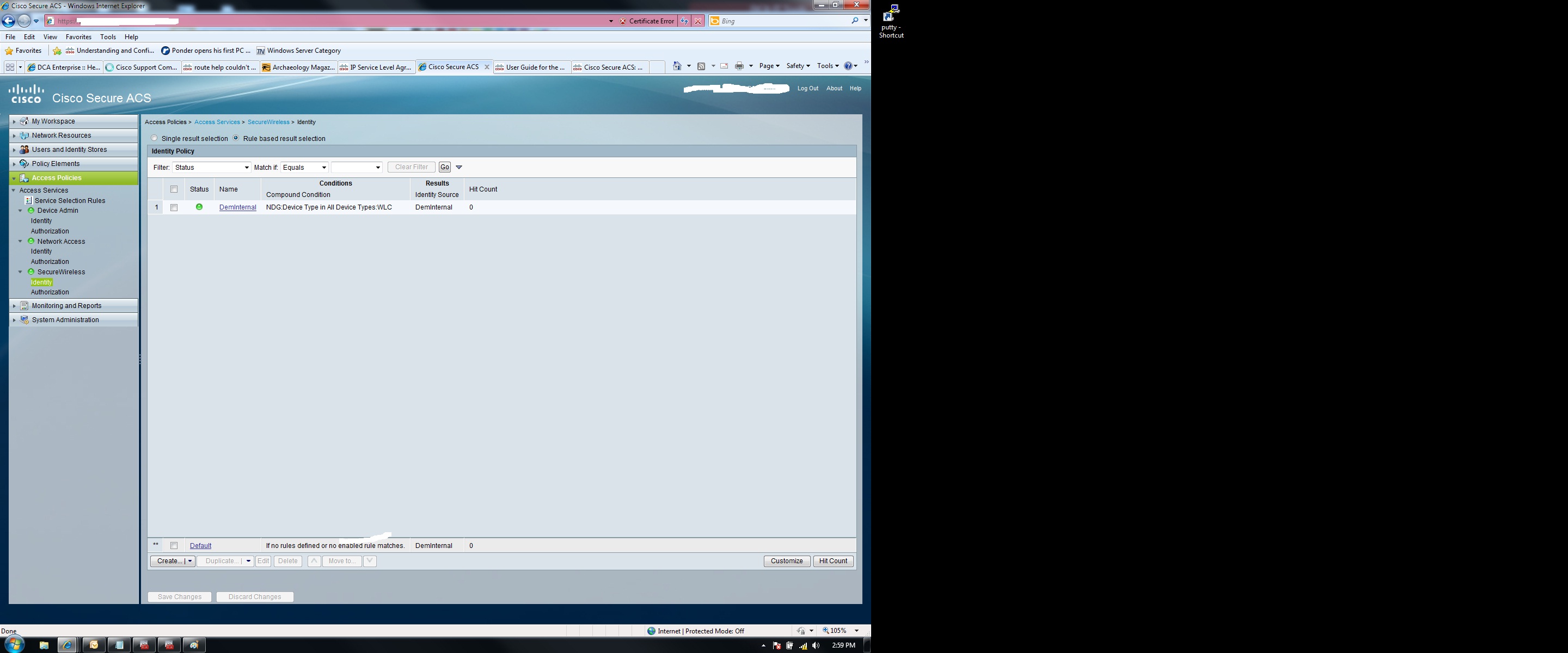
I'm still getting the error message. I must not be configuring the access policy correctly. Which I'm sure you know..


- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2011 01:55 PM
Change your VPN rule base and your wireless rule base to add device ip.
For example:
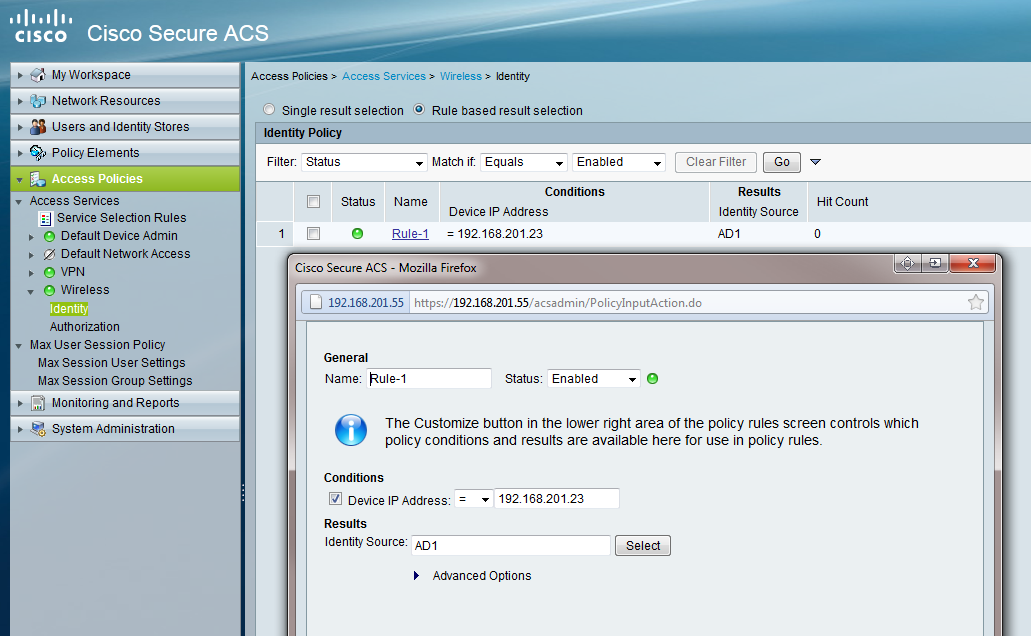
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2011 05:03 AM
Well, I tried a few things you suggested. I'll throw in some pictures. It's still giving the same identity error message.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2011 05:38 AM
Good News!!!! Problem has been fixed. I will include the following screenshot, which has the solution. Maybe you can help me understand why it worked doing this.
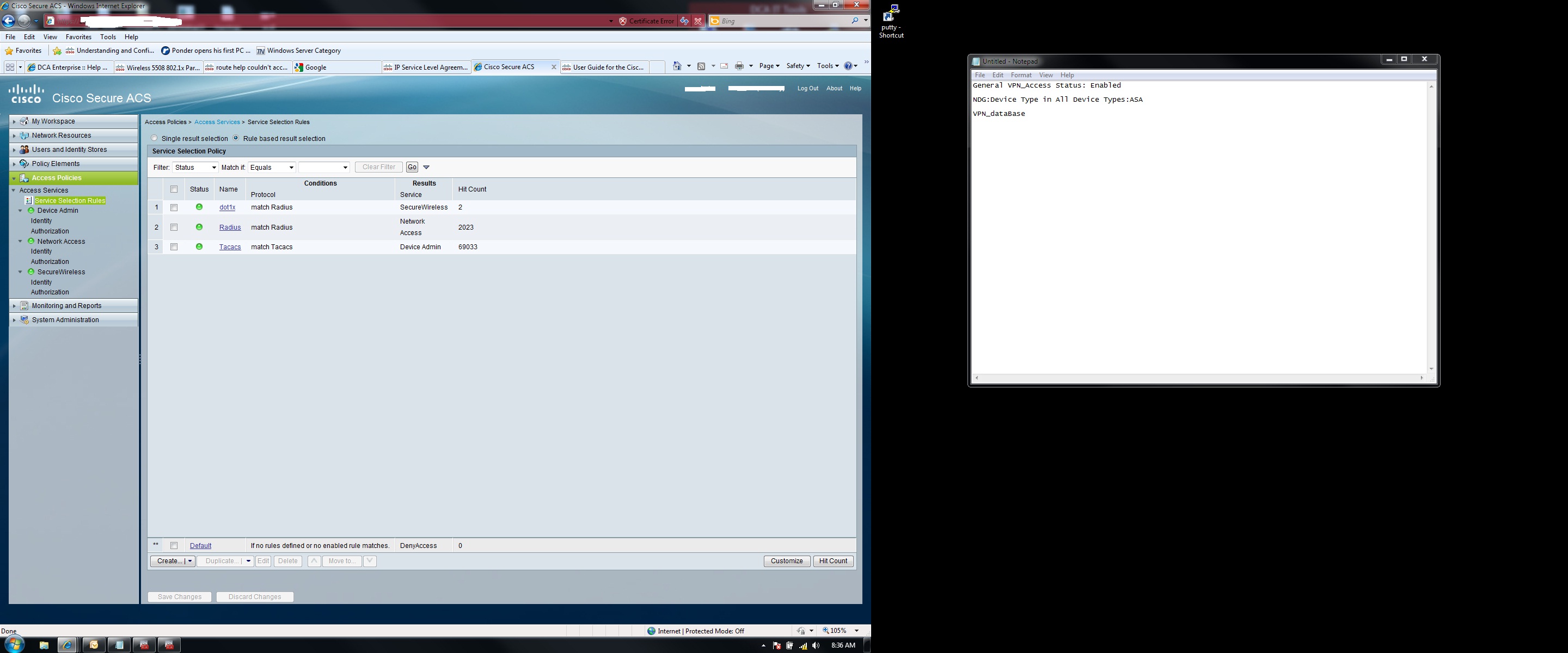
BTW, points will be dished out to everyone that helped! I got to do a few things shortly, but trust me, points will be dished out
Before the service selection was Radius, Tacacs+, then dot1x. Putting dot1x at the top did the trick. Someone may have mentioned that
in one of the previous posts, it's just been such a long discussion...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2011 06:27 AM
Just make sure your VPN is working also.
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2011 06:38 AM
I tried that afterwards and had to move the dot1x to position 3 because VPN stopped working as far as authentication goes. Now I know the problem is with hte selection policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2011 06:55 AM
Please correct me if I'm wrong. If I create a "service selection policy" such as dot1x, which I have already done, and then I made it to the Secure Wireless Access Policy, and move it to the top of the selection order. Whenever something comes
into the Cisco ACS wanting to authentication via RADIUS, it's going to match dot1x and try to run the access policy of SecureWireless. So when I moved this to the top, that's why it worked, but when I tried to VPN, it matched the first rule which was dot1x, and the AD groups I have selected for the Network Access Access Policy, are not there, since it goes to SecureWireless. If that's the case, my question is, How can I order the service selection policy so both of these will work?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


