- Cisco Community
- Technology and Support
- Service Providers
- XR OS and Platforms
- Re: ISM with NAT44 - Need help with configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2013 08:07 PM
Hello everyone,
I'm trying to set up NAT44 in the following scenario below and I'm having a hard time figuring out how to redirect the traffic. As you can see the big problem is that I have one single interface that connects to the internal network (10.0.0.0/8) and also to the tunnel destinations all in the same VRF. Can you guys give me a hand? The trafiic comes from network network 10.0.0.0/8 enters interface bundle-ether 2 (Now it needs to be translated), once it is translated, now it needs to reach the destination known via GRE tunnel.
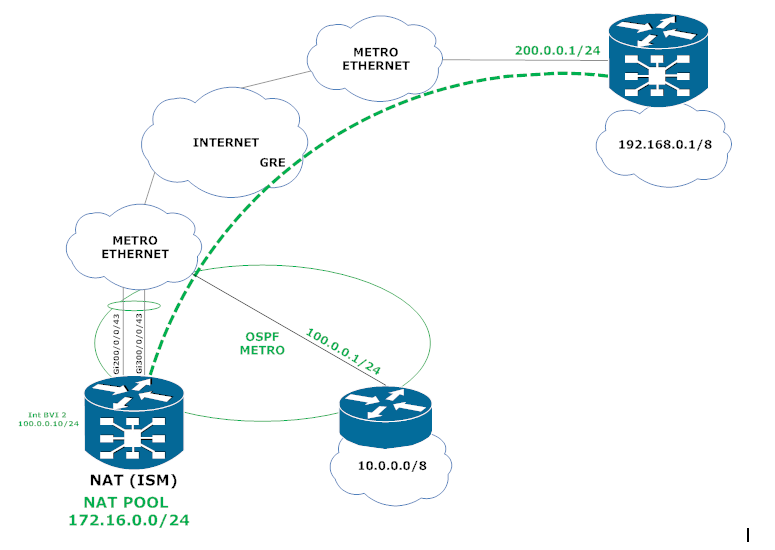
Configurations
-----------------------------------------------
!
vrf NAT_IN
address-family ipv4 unicast
!
!
vrf BLUE
address-family ipv4 unicast
!
!
hw-module service cgn location 0/3/CPU0
!
interface Bundle-Ether2
description UPLINK TO METRO ETHERNET
!
interface Bundle-Ether2.2 l2transport
encapsulation dot1q 2
rewrite ingress tag pop 1 symmetric
!
interface GigabitEthernet200/0/0/43
description LINK TO METRO ETHERNET
bundle id 2 mode active
interface GigabitEthernet300/0/0/43
description LINK TO METRO ETHERNET
bundle id 2 mode active
interface BVI2
description METRO
vrf BLUE
ipv4 address 100.0.0.10/24
!
interface tunnel-ip 101
description GRE_TUNNEL
vrf BLUE
ipv4 address 1.1.1.1/32
tunnel mode gre ipv4
tunnel source interface bvi 2
tunnel destination 200.0.0.1
!
!
interface BVI 100
vrf BLUE
ipv4 address [GATEWAY_100] [MASK_100]
!
interface BVI 200
vrf BLUE
ipv4 address [GATEWAY_200] [MASK_200]
!
interface BVI 300
vrf BLUE
ipv4 address [GATEWAY_300] [MASK_300]
!
!
interface ServiceApp1
vrf NAT_IN
ipv4 address 10.0.2.1 255.255.255.252
service cgn CGN service-type nat44
!
interface ServiceApp2
vrf BLUE
ipv4 address 10.0.2.2 255.255.255.252
service cgn CGN service-type nat44
!
interface ServiceInfra1
ipv4 address 10.0.3.1 255.255.255.0
service-location 0/3/CPU0
!
!
router static
address-family ipv4 unicast
!
vrf NAT_IN
address-family ipv4 unicast
0.0.0.0/0 ServiceApp1
10.0.0.0/8 vrf BLUE bvI 2 <NEXT HOP>
!
!
vrf BLUE
address-family ipv4 unicast
172.16.0.0/24 ServiceApp2
!
!
router ospf METRO
vrf BLUE
router-id [ROUTER_ID]
redistribute bgp 65500 metric 100
area 0
interface bvi 2
!
router ospf BLUE
vrf BLUE
router-id [ROUTER ID]
redistribute bgp 65500 metric 100
area 10
interface BVI100
!
interface BVI200
!
interface BVI200
!
!
!
router bgp 65500
address-family ipv4 unicast
!
address-family vpnv4 unicast
!
!
vrf BLUE
rd 65500:2
address-family ipv4 unicast
redistribute static
redistribute ospf BLUE
!
neighbor 1.1.1.2
remote-as 64512
ebgp-multihop 5
address-family ipv4 unicast
route-policy PASS in
route-policy PASS out
!
!
!
service cgn CGN
service-location preferred-active 0/3/CPU0
service-type nat44 nat44
portlimit 20000
inside-vrf NAT_IN
map outside-vrf BLUE address-pool 172.16.0.0/24
!
!
!
Thanks in advance,
Renato
Solved! Go to Solution.
- Labels:
-
XR OS and Platforms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2013 01:59 PM
Hi Somnath/Harold,
How can I address this issue? Once I need to have my GRE tunnel and interface BE (
inside NAT traffic enters) on the same routing table. Can't I use the global table as my NAT IN?
Thanks
Renato
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2013 07:00 AM
Hi Renato,
The inside interface must be in a VRF but the outside interface can be in the global routing table.
Regards
Harold Ritter, CCIE #4168 (EI, SP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2013 01:14 AM
Hi Renato,
This is what you have so far (for NAT):
bundle-ether 2 (NAT_IN) -- ISM -- bundle-ether 21 (NAT_OUT).
Now, if you want to send the NAT'ed traffic over a GRE tunnel, you need to do the following:
bundle-ether 2 (NAT_IN) -- ISM -- bundle-ether 21 (NAT_OUT) -- loopback cable(s) -- bundle-ether 22 (BLUE) -- Tunnel-IP 101 (BLUE)
This is because as I mentioned earlier, ISM traffic cannot be sent to / come from GRE tunnel directly.
Let me know if that works.
regards,
Somnath.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2013 06:29 PM
Hi Somnath,
Thank you for your attention again. Yes, that's the exactly the configurations I have, but the problem is, once
GRE tunnel currently only supports src/dst resolution in the global routing table and my
src/dst will be in routing table NAT_IN VRF, will I have to use MP-BGP to redistribute my
tunnel's src/dst from VRF NAT_IN to the global table?
Thanks in advance,
Renato Reis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 02:06 PM
Hi Renato,
One way to solve this restriction would be to have two interfaces (physical or logical) connected to the network. One would be in teh VRF and the other in the global.
Regards
Harold Ritter, CCIE #4168 (EI, SP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2013 03:36 AM
Hi Harold,
You hit the nail right on the head, that's the same solution we found. Now I'm gathering some thoubleshootong commands to check if it's working and test it on a production enviroment.
Thank you Harold and Somnath !!!
Regards,
Renato
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 01:32 AM
Is there a command that shows me the inside address, like show ip nat translations on regular IOS? Could you provide me some troubleshooting commands for CGN on ISM?
Thank you !
Renato
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 01:43 AM
Hi Renato,
You can use the following command:
show cgn nat44 nat1 outside-translation protocol udp outside-address <100.200.2.75> port start <1> end <65535>
Other commands useful would be:
show cgn nat44 inside-translation ...
show cgn nat44 pool-utilization ...
show cgn nat44 statistics ...
CCO documentation for all commands are available at - http://www.cisco.com/en/US/docs/routers/asr9000/software/asr9k_r4.3/cg_nat/command/reference/b_cgnat_cr42crs_chapter_01.html.
Please use the commands related to NAT44 as that is what you're using.
regards,
Somnath.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2013 03:58 PM
Thank you Somnath !
[]'s
Renato Reis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2013 03:19 AM
Hi Somnath,
Hope you are doing well ! Is there any MIB that I can use to monitor the NAT sessions and statistics?
Thanks in advance,
Renato Reis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2013 03:29 AM
Hi Renato,
We do not support any CGN MIB yet.
You can possibly use some scripts to capture CLI output periodically.
regards,
Somnath.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2013 09:16 AM
Thank you Somnath,
I have one more question, What is the impact of changing the [map outside-vrf NAT_OUT address-pool]? I'm asking that because I realized the router is using the network and also the broadcast address of the network I configured as my NAT pool as a valid IP address for translations, I guess I have to avoid it !
Thank you,
Renato
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2013 10:13 PM
Hi Renato,
Sorry, I could not get your question properly.
If you want to change the address pool while NAT traffic is going on, during the time you're changing the address, traffic will be dropped by CGv6 Application (with "No CGN Config" kind of message).
Once you configure new address pool, you may need to change your static route entry to divert O2I traffic properly.
It is ok to include .0 / .255 in the public IP pool (if that it what you're referring) - there should not be any issue.
regards,
Somnath.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2013 03:36 AM
Hi Somnath,
Thank you again ! Actually I wondering if using .0 / .255 could be an issue thats why I asked of changing the address pool would be a problem. I'm glad there is no problem using the network and broadcast address.
PS: I'd like to thank you for all your help, now we have GCN with ISM working on a production environment.
Thanks,
Renato
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2013 03:44 AM
Hi Renato,
That is a great news ! Congratulations !!
Glad to help you out !
It would be great if you can post the final configuration that you're using for your deployment here along with some of the "show" command output (like, 'show cgn ...', 'show interfaces service* [accounting]', etc.).
regards,
Somnath.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

