- Cisco Community
- Technology and Support
- Collaboration
- IP Telephony and Phones
- ATA 186 Port 80 vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2018 07:26 AM - edited 03-18-2019 12:33 PM
Hello Community!
Looking for a way to disable the web interface of these devices either from CUCM or local side. Our Security Dept has flagged these with a port 80 vulnerability and which our CUCM provider has yet to provide any reasonable action. Suggestions were to input an ACL however that would be a last resort and not knowing if that will block any other functionality.
Suggestions would be greatly appreciated.
Thanks,IP Telephony and Phones
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2018 07:43 AM
Hi, you can modify the bit 7 of OpFlag of the common configuration file on the tftp server:
The bit 7 is used to configure "web configuration access", 0 allow web config, 1 do not allow.
This metho is not so easy. Probably you can check on whiwhat is the IP of the default gateway of your ATAs and configure an ACL to block all accesse on the port 80.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 06:58 AM - edited 10-04-2018 07:04 AM
If the device is giving you trouble with the web interface and assuming you are using a manage switch why not write an ACL to block port 80 traffic at the switchport? It should not not block any functionality aside from the web interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2018 07:43 AM
Hi, you can modify the bit 7 of OpFlag of the common configuration file on the tftp server:
The bit 7 is used to configure "web configuration access", 0 allow web config, 1 do not allow.
This metho is not so easy. Probably you can check on whiwhat is the IP of the default gateway of your ATAs and configure an ACL to block all accesse on the port 80.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 08:30 AM
our provider with no luck.
Can this be changed locally in the web interface then once applied will
stop the access?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 08:36 AM
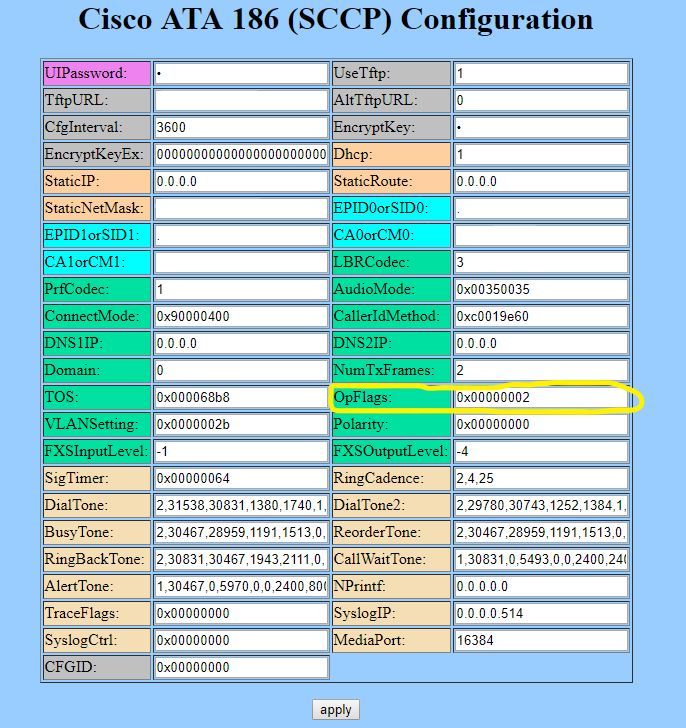
OP flag parameter is available over the web interface from the Network Parameters Link in the left menu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 08:52 AM
Here's what I see.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 09:00 AM
Thats the setting. Looks like you are on an older Firmware version than I am used to. Adjust the bit that was suggested and see if that works for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 01:56 PM
I was able to test this one at my desk. Now to work with the vendor for mass fix.
Thank you ALL !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 07:52 PM
Curious why an open port 80 is in and of itself insecure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 05:21 AM
unsecure due to that port. If it was 443, we would be moving on.
I did find this morning after a reboot, the device somewhat reset itself
and the web interface is enabled.
This is what my opsflag looks now.
0x00000012
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 06:58 AM - edited 10-04-2018 07:04 AM
If the device is giving you trouble with the web interface and assuming you are using a manage switch why not write an ACL to block port 80 traffic at the switchport? It should not not block any functionality aside from the web interface.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide