- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: Topology Feedback
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Topology Feedback
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 03:52 AM
Hi All,
I am designing a network that is connected to a corporate network.
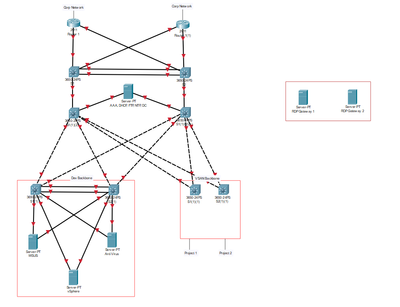
The private network contains a Project network and a Developers Network. My topology is below.
Please could I have some feedback on how it can be improved as this is for a university assignment. Also I would like to implement firewalls and the RDP gateway but am unsure of where to place them.
Daniel Growth
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 05:09 AM
Hi Daniel,
I'm sure you'll find plenty of people in the Cisco Community forums that would be happy to discuss your topology with you. Are you able to share more of the assignment specifics with the community? Networks have become very versatile, and I'm not how helpful any of use can be just "giving feedback" (I have a background in secure private networks which would be different than the feedback you'd get from someone who, say, works for a web services company and has a focus on high availability and fault tolerance).
Off the cuff, there are a few things I notice about your network topology that you may want to consider revisiting.
1) You seem to have made a very traditional 3-tier (access, distribution, core) L2 topology here... to support 4 servers and a SAN. Can I ask why? A collapsed-core model (where core and distribution layers are combined) would be a more common choice in 2019, especially since you appear to be using all layer 3 switches?
2) There are no subnets indicated on this topology, but is your intention to have 2 separate points of ingress and egress on the network? At a glance, this looks like one network segment hosting a few servers--have you considered using Hot Standby Redundancy Protocol or Gateway Load Balancing Protocol to merge your 2 routers into one logical gateway? If your goal is fault-tolerance, I would recommend using HSRP or GLBP. If you have a very compelling reason to use 2 gateways to return to the same parent network (route tagging for unidirectional routing??? I doubt it?), then it's fine the way it is.
3) You may want to consider looking into a Virtual Switching System (VSS), which would allow you to logically merge pairs of switches in the topology (presumably you don't have a budget for this imaginary topology--so you could use expensive enterprise gear). VSS eliminates the needs for redundant switches (that's actually why it was invented) and would make your topology look a little cleaner.
4) I'm actually working on a project at work right now using RD servers in an off-campus subnet for maintenance access to specialty services servers. I can tell you that our RD servers are basically the back end of our Threat Management Gateway ( [Untrusted internet] --> [Threat Management/Fireway :: Remote Desktop Servers] --> [Specialty Services servers] ).
Which brings us to
5) Firewalls: If this topology is in fact meant to connect to an intranet (another trusted network) I'm not sure what the need for a firewall would be. You use firewalls to police potentially untrusted traffic from coming into your network from an external network. That being said, if you were running some sort of high-security service out of this network, you may put a firewall at the edge of either the service or the network if you didn't think a regular router with Access Control Entries would do it (typically in a topology like this, if you wanted to police traffic, you would put ingress ACEs on your gateway routers to prevent traffic from coming in except from authorized sources). For the scope of this project, based on my best guess, your firewalls should on the external side of your routers OR (less likely) at the edge of the "dev backbone" area.
I hope this information has been helpful, and please let me know if you have any more questions or would like more feedback.
Please rate/mark this answer if it's been helpful to you.
Good luck on your assignment!
-Zac
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 03:17 AM
Hey,
Thanks for the information its offered great insight. My assignment is a long and complicated one because I am a higher degree apprentice meaning I work full time and my employers pay for my university studies. In a nut shell I have to design and propose a network to the business for an isolated project and dev network.
The ISP is done through the corporate lan so i wont need to worry about adding one in.
Daniel Growth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 05:18 AM
Daniel,
Having your employer pay for your school is a pretty sweet deal. Based on the nature of that program and some of your vocabulary, I would guess you live in Europe. As an American, I will be paying off a crippling student debt for the rest of my life unless I fall ill and medical bankruptcy gets me first, so good for you getting an education on the cheap!
How "isolated" do you want these two proposed networks to be from each other or from the corporate LAN? A cheap ASA will do a pretty good job keeping networks from communicating with each other, but so will a VLAN and/or an Access Control List in a router. Not sure how deep into it you want to get, but there are probably about a thousand options to run (what would be called) a small stub network off of your corporate LAN. If you want to discuss it any further I'm happy to do so.
Good luck with school and work!
-Zac
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide