Hi Guys, i have this issues "Smart License usage is out of compliance." ... what is the solution of this error Thanks !
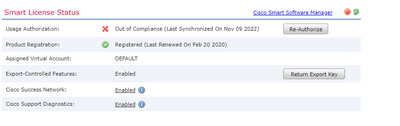
Hi Guys, i have this issues "Smart License usage is out of compliance." ... what is the solution of this error Thanks !

We have run into an issue with an ASA5516-X device where we cannot issue new deployments. All deployments fail, creating an entry in pigtail deploy like this:NGUI: 04-01 19:59:51 ajp-nio-8009-exec-5: ERROR ExceptionHandlerAspect:48 - Managed NGFWApp...
how deep do I need to lear about Zone-Based Firewall . on the book OCG on page 435 and 436 , it is just have page. on the Domain 2.0 I don't find it . but yet on the exam I have couple question about firewall. any advice
I'm wondering if there is a way to remove ALL network-objects from an network object-group with one command. I figured the easiest way to do this is to negate the object-group and re-create it. If the object-group is used on a ACL it is not possibl...
How to I use the Real-Time Log Viewer in ASDM to search for XXX.XXX.XXX.1 and it not show XXX.XXX.XXX.123, for example? I want to see only the IP ending in .1, NOT the ones ending in .12, .11, .134, .150, etc.I have tried adding quotes, as in "XXX.XX...
Hello, for reasons of compliance we are required to syslog URL visited.With the config below (not full) I am able to see the IP visited, and this only for http.Is there a way to syslog the http and https URLs ?parameter-map type urlf-glob PERMITTEDSI...
Hello, Cisco Gurus!Anyone setup route-based IPSec tunnel on the same ASAv that hosts multiple policy-based S2S VPN's? Cisco says it's possible, but didn't provide any best practices. Specifically, we're interested in placing our internal sources (whi...
Hello Family,Hope you are well,Needed help figure out how to migrate IPsec tunnels from one FTD to another using Secure Firewall Migration Tool .What do i need to worry/cater for to ensure seamless migration - no downtime.Thank you.
Hello all,I am having an issue where I am getting a ERR_CONNECTION_REFUSED whenever I visit a website without HTTPS in the URL. I have narrowed it to the firewall blocking the traffic because the direct connection to the internet via the modem doesn'...
Hi All,I'm trying to allow traceroute through the firewall as per the below doc, however, when I update the Platform Settings to permit traceroute on Inside, Outside and another zone, SLA monitor which is tracking the primary ISP goes down and failov...
Can anyone help me out with this. I've got Switches setup in ISE to use TACACS to authenticate the logins. I'm looking to setup DOT1X on the ports, along with MAB. I have the config in ISE set but i'm trying to determine exactly how to setup the s...
Is it possible for the FMC to run a report to indicate what rules are inactive/disabled? What about reporting what objects are not being used?I know beside various items there is a "report" icon, or "export to csv" but this isn't giving me the info I...
I would like to upgrade FMC, due to this upgrade I would like to create ticket support on Cisco Portal. In the portal it requests me provide "Product Seri Number or VLN" Please guide me how can I get these information in my FMC server
Greetings! Hope somebody can guide me how is it supposed to be done! Sorry, I'm a noob and seems to can't find an answer.Lets say I have 3 subnets/vlans/interfaces with security levels:inside (90)dmz (10)outside (0)lets say I want to allow http/https...
My FTD (FDM) running code 7.2.5.1-29 is getting the following message on the Smart License section: CONNECTION ISSUEFailed To Connect With License Server Lost connection for 0 days (Next Sync on 28 Mar 2024 11:06 PM). Please check and make sure the m...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
| Subject | Author | Posted |
|---|---|---|
| 12-31-2025 01:53 AM | ||
| 12-15-2025 09:32 PM | ||
| 12-11-2025 07:27 AM | ||
| 11-13-2025 12:52 PM | ||
| 11-03-2025 09:48 AM |
| User | Count |
|---|---|
| 5 | |
| 4 | |
| 2 | |
| 2 | |
| 1 |
