- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD 1010 default action behavior with base license
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2022 06:57 PM
I have an FTD 1010 with only a base license and a requirement to use this as a simple Internet router/gateway. I have a dynamic NAT rule using interface PAT and one access rule that trusts outgoing traffic. If I set the default action to block I cannot get Internet traffic to flow so for now I have the default action to trust to get things going.
At the moment this is not a big deal but what would happen when/if I setup a static NAT? At that time I would want to set the default action to block to prevent unwanted traffic to the static NAT host but then it would break the dynamic NAT clients?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 12:12 AM
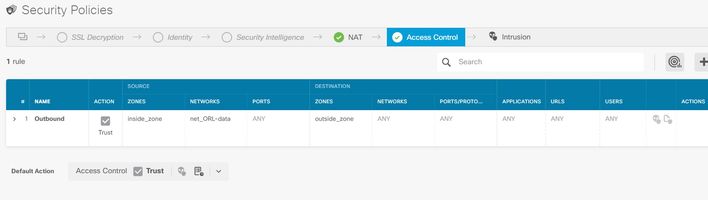
@tato386 if traffic is not matching your defined access control rule, are your physical or vlan interfaces actually assigned to the correct zones (inside_zone and outside_zone)? You do not need to define a rule using the zones, you could just use the source/destination networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 12:12 AM
@tato386 if traffic is not matching your defined access control rule, are your physical or vlan interfaces actually assigned to the correct zones (inside_zone and outside_zone)? You do not need to define a rule using the zones, you could just use the source/destination networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 06:37 AM
i do not believe this due to your License, more of config issue looks for me. not able read the image properly to suggest something here.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 07:14 AM
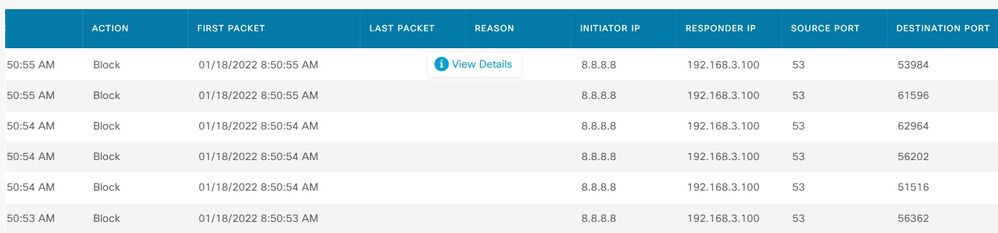
@balaji.bandi is correct it does not have anything to do with the license. It was an issue with the configuration of the security zones. The zones were one of the first things I setup and I am 99% sure I added interfaces at that time but lo and behold when I double-checked (thanks @Rob Ingram !) the zones were empty?! After adding (re-adding?) the interfaces traffic flowed correctly with block as default action. An interesting thing is that Internet traffic seems to be working perfectly normal but curiously, inbound reply from DNS servers is showing as being blocked. Should I worry about this if things appear to be normal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 07:06 AM
Do you only have the inside_zone or are there more subnets behind the FTD?
Currently, if you add a static NAT statement and an access rule allowing access to that server from the outside, and then set the default action to block, users on the inside_zone will still be able to reach the internet.
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide