- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Configuring multiple VRFs on a 9500 pair to segregate remote sites
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configuring multiple VRFs on a 9500 pair to segregate remote sites
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 01:32 PM
We have multiple remote locations connecting to a central site which has a pair of 9500s. In between the remote sites and the central sites is AT&T's ASE switched Ethernet service. I need to come up with a solution to keep the remote sites from reaching each other. I thought of using a separate VRF instance for each site, but I wasn't sure if this is a scalable solution (we currently have 30-40 remote sites). In addition to the Internet connection for all remote sites being at the central site, there are several other resources the remote sites will need access to (e.g., servers in a virtual data center). Am I on the right track here?
- Labels:
-
Catalyst Switch
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 01:39 PM
Hi
You are. The limitation you need to look is:
● ASIC tables for switching scale up to 256K MAC addresses and routing scale up to 2M routes.
The number of VRF is not the problem but the routing can be.
Now, for internet access and shared resources, you need to work with routing leak between VRF or VRF and Global Routing table.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 01:54 PM
if the Delivery is 1G bearer then that should be ok to terminate on Cat 9500, if this is less than 10-100MB you may see some issue on the interface level. how about other ends remote site ?
you can call as WAN Edge Access switch, all Layer 2 will terminate here. will all remote sites use the Internet from the central Site Internet Pipe
then you need to look decent Firewall with next-gen firewall features Like IPS and content filtering (on the Perimeter side)
When you mentioned DC firewall you may need some Firewall DC network to protect the services.
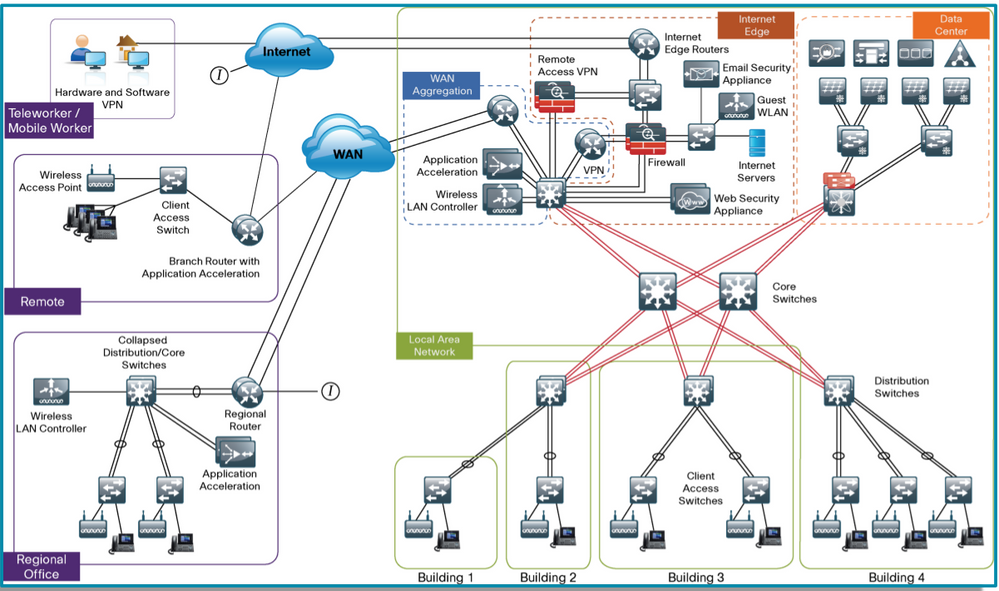
example one I copied from cisco Live ;
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 03:23 PM
Hi there,
Use of VRFs and route leaking between them could grow into a painful admin overhead. Your switched Ethernet service should provide you with a q-in-q capability, this means a tagged packet from a remote site could arrive at the central site and retain the same VLAN ID. This could be switched on the 9500 towards a firewall Layer 3 sub-interface. The firewall would provide ACLs to control inter-site communication and also permit access to the central and internet based services.
Ideally you would want to police the inter-site traffic before it left the remote site as this would save WAN bandwidth, but would require careful curation of 40+ ACLs on 40+ different devices. Granted this could be automated, but using a single firewall at the central location mitigates this.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 05:58 AM
Yes, I was worried that the VRF idea would be hard to maintain. I was hoping for a simpler solution, but I think some people here are trying to push the VRF solution.
Wouldn't an ACL on the central site stop inter-site traffic? Each site's routes are summarized down to 4, and it's really one of those 4 that we're really interested in restricting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 06:42 AM
Agreed, ACLs at the central site would be the simplest solution but placing those ACLs at the remote site WAN links would be best.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 06:46 AM
I'm not sure I understand why separate ACLs on the remote site end would be better than 1 at the central site
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 07:37 AM
One point I just though of... there really isn't much site-to-site traffic currently. The issue driving this is the concern to prevent malware spreading from one remote site to others.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 07:42 AM - edited 06-26-2022 01:26 PM
What's to say your central services don't become a focal point of infection and circumvent any ACLs you have in place. Perhaps having a central firewall which acts as the routing hub for all of the WAN sites is the best option. Something like a Palo Alto excels in this position.
cheers,
Seb.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide