- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: NAT with DMZ
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAT with DMZ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2023 01:31 AM
Hello,
Currently I have a central router that allows me to manage backup via a secondary link. It works correctly !
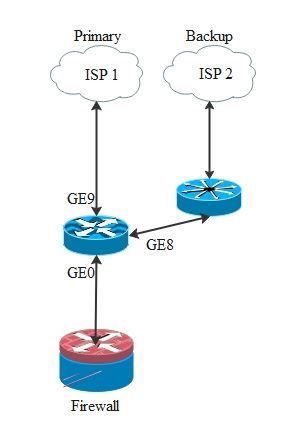
Now I have to add a firewall which will be in DMZ. All ISP-1 and IPS-2 (if ISP-1 become down) traffic must enter the Firewall.
My problem is the use of the ip nat inside source static command for DMZ to be able to manage the two ISPs in the event of a switchover.
interface GigabitEthernet0
description * DMZ to Firewall .100 *
ip address 10.0.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
interface GigabitEthernet8
description * Primary WAN *
ip address 1.1.1.1 255.255.255.252
ip nat outside
ip virtual-reassembly in
!
interface GigabitEthernet9
description * Secondary WAN *
ip address 2.2.2.1 255.255.255.252
ip nat outside
ip virtual-reassembly in
!
ip nat inside source route-map ISP-1 interface GigabitEthernet8 overload
ip nat inside source route-map ISP-2 interface GigabitEthernet9 overload
!
ip route 0.0.0.0 0.0.0.0 GigabitEthernet8 1.1.1.2 name PRIMARY track 1
ip route 0.0.0.0 0.0.0.0 GigabitEthernet9 2.2.2.2 10 name SECONDARY
!
route-map ISP-1 permit 10
match ip address 101
match interface GigabitEthernet8
!
route-map ISP-2 permit 10
match ip address 101
match interface GigabitEthernet9
!
access-list 101 permit ip 10.0.1.0 0.0.0.255 any
!
ip nat inside source static 10.0.1.100 ISP-1/ISP-2 extendableHow to manage two ip nat inside source static in the case of an active/backup link ?
Thanks
- Labels:
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2023 07:11 AM
Hello
I guess what i am trying to state is why is there a need to nat on the FW , the central rtr is already performing this along with the ISP failover correct, also the central will need to forward all traffic to the FW irrespective if NAT is on the Fw or not.
Lastly the central can also be configured to be accessed internally from the wan & lan via its pubic ip address if required via NAT hairpinning ON the central rtr
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2023 08:44 AM
I don't see the difference in operation at all... Can you show me the configuration you think ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2023 12:09 PM
Hi @sebastien3 ,
Did you already read about "list boolean" SLA? We have "and", "or" parameters. In this way, you can test ISP with HTTP, dns, ping, reachability and another stuffs as unique SLA. Maybe that is good for your scenario.
Please let me know if this help you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2023 02:24 PM
Hello
@sebastien3 wrote:
My problem is the use of the ip nat inside source static command for DMZ to be able to manage the two ISPs in the event of a switchove
Apologies its not clear to me why you need to double nat with this setup, the central router is already natting towards both ISPs?
Various nats can accomplish different things, DNAT, LB , Harpinning etc...if you need to add a rule on the FW then you don't need to double nat for this unless Im missing something fundamental to your requirements, hence why at present its a bit vague to what you want to accomplish:
Are are you wanting to use this 10.0.1.100 too..
*To reach both your isp rtrs with this internal host
*To reach this internal host externally from either ISP
* Nat the same internal host to different public ip addresses, ie: load balancing?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 08:39 AM
Hello @paul driver
*To reach both your isp rtrs with this internal host => Yes
*To reach this internal host externally from either ISP => Yes
* Nat the same internal host to different public ip addresses, ie: load balancing? => No
The firewall uses the ISP 1 exit as a priority. If ISP 1 fails then the firewall must use the exit to ISP 2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 01:29 AM
Hello
@sebastien3 wrote:
Hello,
@sebastien3 wrote:
The firewall uses the ISP 1 exit as a priority. If ISP 1 fails then the firewall must use the exit to ISP 2
Thank you clarification, so based on this above, You have a couple points of failure (Firewall and ISP1 rtr)
That first ISP1router is performing the NAT and conditional route failover between ISP1 and the other attached rtrs ISP2, so your firewalls default route should NEVER change as its WAN interface next hop ip address will be the directly connected ip address of that first rtrs LAN interface in your topology
@sebastien3 wrote:
*To reach both your isp rtrs with this internal host => Yes
*To reach this internal host externally from either ISP => Yes
As I already mentioned, this could be accomplished on that first ISP1 rtr which directly connected to your FW, as such you DONT need to perform any NAT on the firewall.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 02:09 AM
Hello @paul driver
@paul driver wrote:Thank you clarification, so based on this above, You have a couple points of failure (Firewall and ISP1 rtr)
This is not too important... The SPOF is managed (duplicate rtr and duplicate firewall in order to do a quick action).The critical point is the fiber cut ! So the ISP 1 rtr must be able to switch automatically to the ADSL router...
As I already mentioned, this could be accomplished on that first ISP1 rtr which directly connected to your FW, as such you DONT need to perform any NAT on the firewall.
You have to explain to me how because I don't understand !
Example:
A server connected behind the Firewall (192.168.200.200) needs to have its port 80 accessible on the WAN IP of the ISP 1 router.
How do you do this ?
This is why you must use ip nat inside source static 10.0.1.100 ISP-1/ISP-2 extendable
Please clarify !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 02:57 AM
This is why you must use ip nat inside source static 10.0.1.100 ISP-1/ISP-2 extendable <<- this already I send solution for it.
but you mention you want ip nat inside source static tcp not ip
I already check for solution for this point and there are no command for this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 05:42 AM
Hello @MHM Cisco World
I need ip nat inside source static tcp only for a single port to be able to connect in SSH on the router. Then everything else is sent back to the firewall...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 05:51 AM
if you SSH then NAT will done first and instead of SSH to router the traffic end in ASA, That correct,
but you missing something here you can use any other Public IP instead of using Router Public IP.
this make you sure if you SSH to Router public IP you SSH to router
and all other traffic will use other Public IP to access ASA.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide