User Experience Enhancements
As part of the Cisco Common User Experience program, we are working towards a more uniform user experience and terminology alignment. This program runs across all Cisco security products.
New features added to Cognitive Intelligence beta GUI
As part of our continuous efforts to improve productivity and drive efficacy, additional features have been added for customers with Early Access to the new GUI enabled:

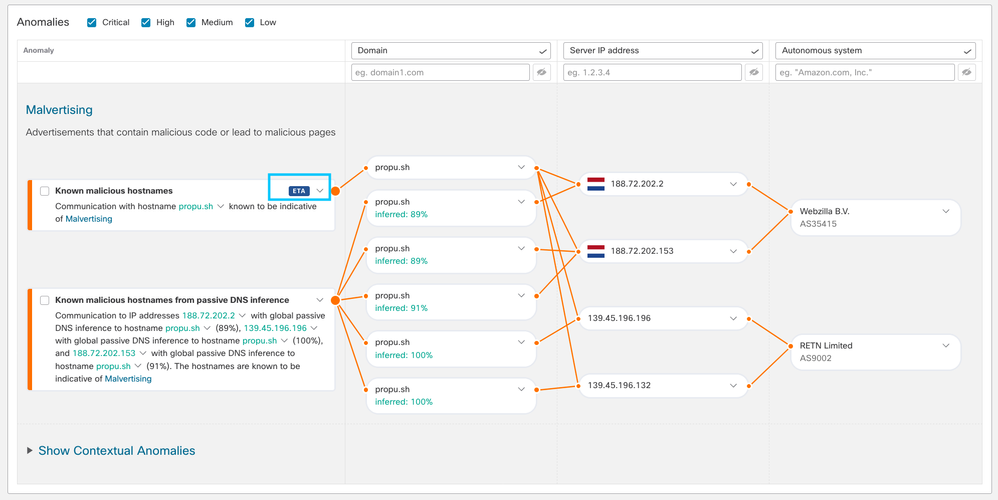
ETA tag is visible at anomaly level
Now you can have full visibility of which specific anomalies were discovered using ETA data.
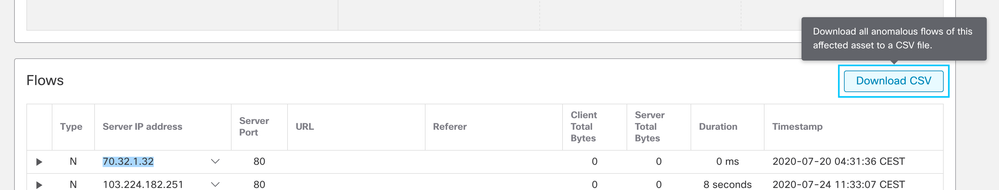
Download of flows where anomalies were found is now available
During the investigation of a specific asset, it’s possible to download all the flows related to anomalies found for that specific asset.
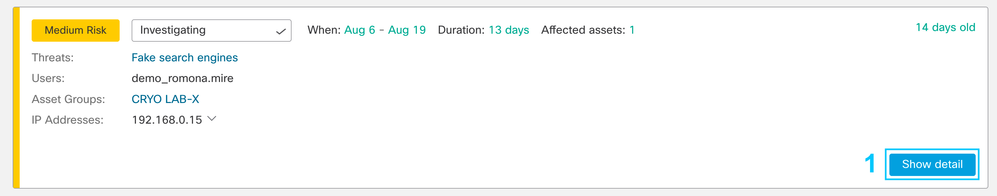
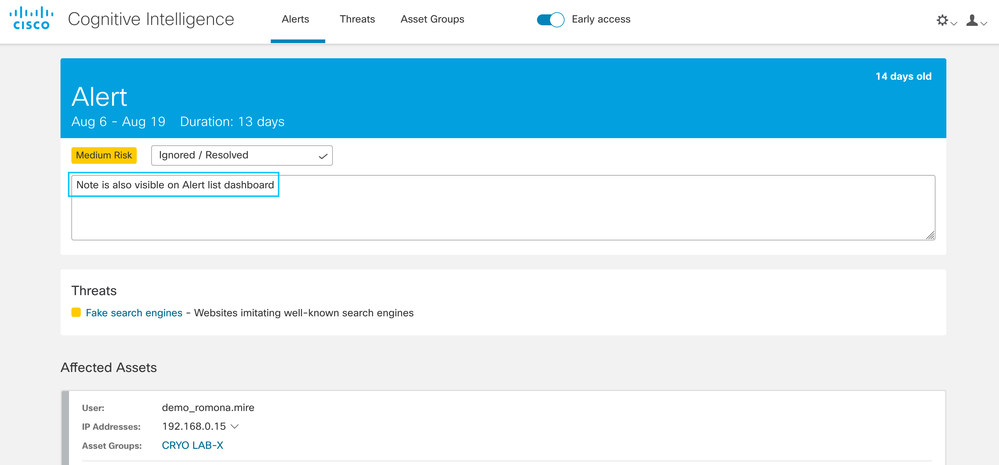
Adding notes in Alert Detail
Now you can add your own comments in the Alert Detail view, enabling you to track specific findings from your investigation and have all the information about the threat together. The notes are enabled when an alert is placed in any state different from “New/Triage” (Investigating, Remediating, Remediated/Resolved, False Positive/Resolved, Ignored/Resolved).
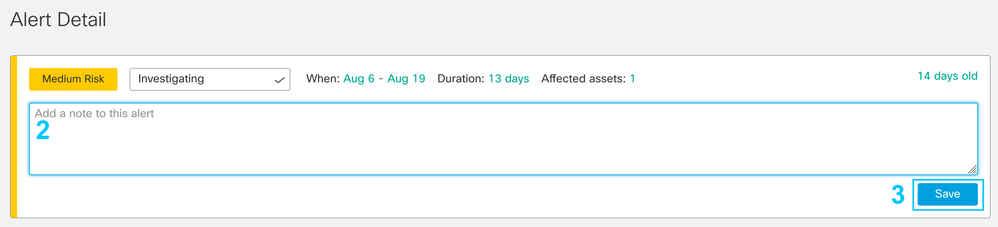
After saving the changes, the note is visible, and if necessary, it can be modified:
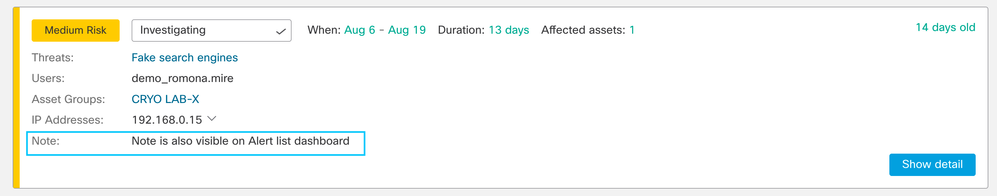
It will also be visible on the Alert Dashboard:
Efficacy feedback
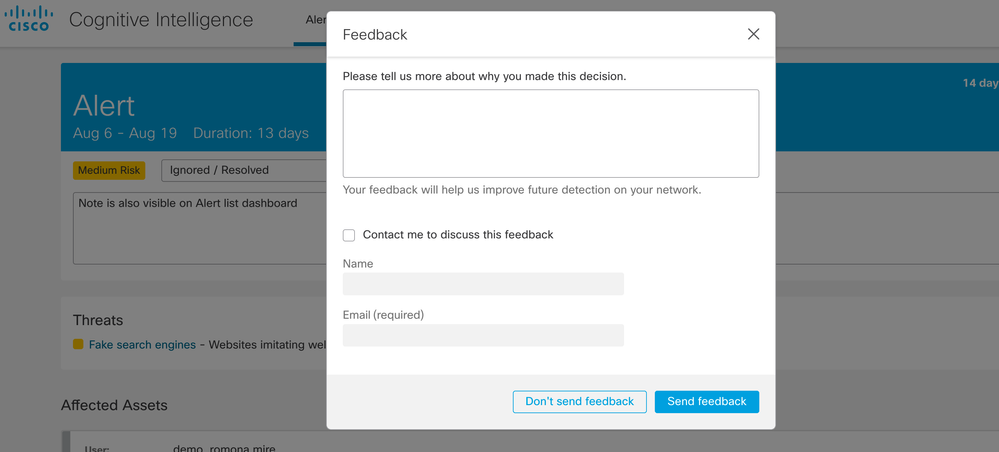
When closing an alert with a state of “False Positive/Resolved” or “Ignored/Resolved,” the Cognitive development team kindly asks you to provide any feedback regarding the alert. This feedback is used to evaluate the value and accuracy of threats.
Threat tool tip
When you hover over the name of a specific threat, you see at-a-glance a brief summary of the most relevant information.
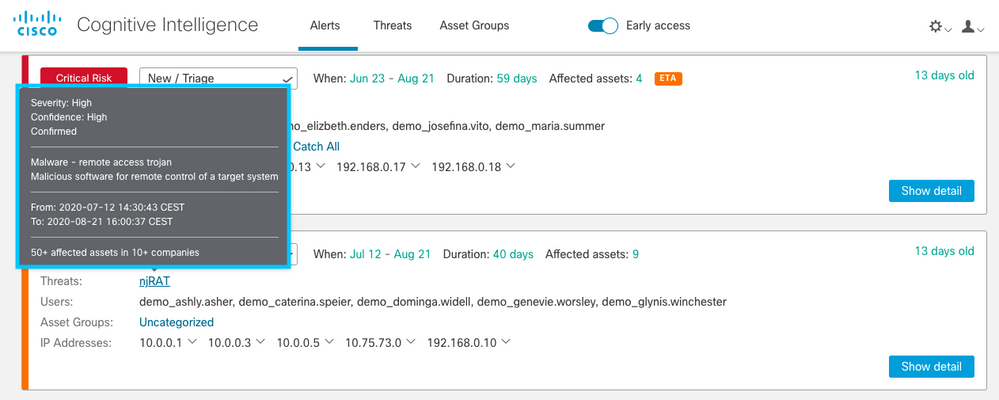
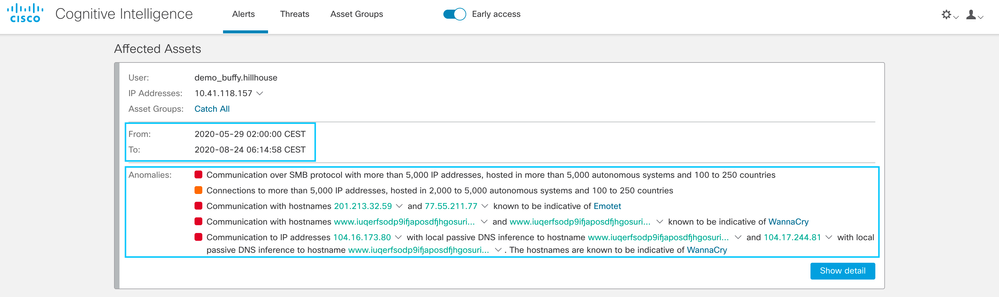
Alert Detail includes additional fields
Now it’s possible to see a short description of all the anomalies related to this alert, and the time period that the alarm covers.
New Confirmed Threats
List of new Confirmed Threat types in August:
|
Name
|
Category
|
Risk
|
Description
|
|
Taidoor
|
Information Stealer
|
Critical
|
Taidoor is a remote access trojan (RAT) which gives the attacker complete remote control and administration of the infected device. This RAT is associated with a number of advanced persistent threat (APT) groups.
|
|
ARS VBS Loader
|
Malware Distribution
|
High
|
ARS VBS Loader is designed to download and execute other malware. It also contains a command‐and‐control (C2) application that is acting as a remote access trojan (RAT). RATs are used in targeted attacks, espionage, financial theft, and stealing of sensitive corporate information.
|
|
Kentrum
|
Malware/ Remote Access Trojan (RAT)
|
Critical
|
Ketrum is a remote access trojan (RAT) which gives the attacker complete remote control and administration of the infected device, including the ability to execute commands. Ketrum merges features from backdoor families Ketrican and Okrum.
|
|
GuLoader
|
Malware Distribution
|
High
|
Threat related to the GuLoader malware dropper which is designed to distribute other malware such as remote access trojans, ransomware, and so on.
|
|
Maze
|
Malware / Ransomware
|
High
|
Maze encrypts all files on an infected system and demands ransom to recover the files.
|
Leveraging Cognitive Intelligence
Cognitive Intelligence capabilities are available to AMP customers with a compatible web proxy such as the Cisco Web Security Appliance, and all Stealthwatch Enterprise customers. Reach out to your account executive to learn how to turbocharge your existing cybersecurity investment with Cognitive.
