Prerequisites
Cisco ASA with or without OS installed.
Console Connectivity to device
Correct ASA OS to selected hardware model (Eg. asa941-lfbff-k8.SPA) downloaded from cisco web site
Correct ASDM maching to selected ASA software
TFTP server which connected to same network
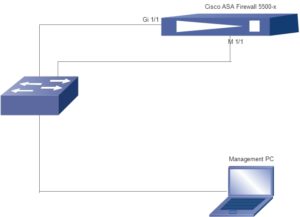
Steps of formatting:
- Connect to the console connectivity connected to asa 5500-x device
- Reload the device and go to ROMMON Mode using break sequence.
Use BREAK or ESC to interrupt boot.
- Use ROMMON Mode with below commands to upload ASA OS
rommon 1 > erase disk0: – will take 5-10 minutes
rommon 1 > ADDRESS=192.168.3.43 – address for ASA device
rommon 2 > NETMASK=255.255.255.0
rommon 3 > SERVER=192.168.3.29 – address of TFTP server
rommon 4 > IMAGE=asa941-lfbff-k8.SPA – OS file Name
rommon 5 > sync
rommon 6 > tftpdnld
ADDRESS: 192.168.3.43
NETMASK: 255.255.255.0
GATEWAY: 192.168.3.1
SERVER: 192.168.3.29
IMAGE: asa941-lfbff-k8.SPA
MACADDR: 18:8b:9d:40:51:6e
VERBOSITY: Progress
RETRY: 40
PKTTIMEOUT: 7200
BLKSIZE: 512
CHECKSUM: Yes
PORT: GbE/1
PHYMODE: Auto Detect
Receiving asa941-lfbff-k8.SPA from 192.168.3.29!!!!!!!!!!!!!!!!!!!!
File reception completed.
Boot buffer bigbuf=348bd018
Boot image size = 69454656 (0x423cb40) bytes
[image size] 69454656
[MD5 signaure] 449c9c79c65dfc756b843a1285267d53
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces… done.
Populating dev cache
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
Logical sector size is zero.
dosfsck(/dev/sdb1) returned 1
mount: wrong fs type, bad option, bad superblock on /dev/sdb1,
missing codepage or helper program, or other error
In some cases useful info is found in syslog – try
dmesg | tail or so.
mount: /dev/sdb1 is write-protected, mounting read-only
mount: wrong fs type, bad option, bad superblock on /dev/sdb1,
missing codepage or helper program, or other error
In some cases useful info is found in syslog – try
dmesg | tail or so.
Processor memory 1242769653
Compiled on Sat 21-Mar-15 11:42 PDT by builders
Total NICs found: 13
i354 rev03 Gigabit Ethernet @ irq255 dev 20 index 08 MAC: 188b.9d40.516e
ivshmem rev03 Backplane Data Interface @ index 09 MAC: 0000.0001.0002
en_vtun rev00 Backplane Control Interface @ index 10 MAC: 0000.0001.0001
en_vtun rev00 Backplane Int-Mgmt Interface @ index 11 MAC: 0000.0001.0003
en_vtun rev00 Backplane Ext-Mgmt Interface @ index 12 MAC: 0000.0000.0000
INFO: Unable to read firewall mode from flash
Writing default firewall mode (single) to flash
Verify the activation-key, it might take a while…
Failed to retrieve permanent activation key.
Running Permanent Activation Key: 0x00000000 0x00000000 0x00000000 0x00000000 0x00000000
The Running Activation Key is not valid, using default settings:
Licensed features for this platform:
Maximum Physical Interfaces : Unlimited perpetual
Maximum VLANs : 5 perpetual
Inside Hosts : Unlimited perpetual
Failover : Disabled perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Disabled perpetual
GTP/GPRS : Disabled perpetual
AnyConnect Premium Peers : 2 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 10 perpetual
Total VPN Peers : 12 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
Total UC Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Cluster : Disabled perpetual
This platform has a Base license.
INFO: Unable to read cluster interface-mode from flash
Writing default mode “None” to flash
Encryption hardware device: Cisco ASA Crypto on-board accelerator (revision 0x1)
Cisco Adaptive Security Appliance Software Version 9.4(1)
————————–
Output Omitted!
————————–
INFO: Starting SW-DRBG health test…
INFO: SW-DRBG health test passed.
Pre-configure Firewall now through interactive prompts [yes]? – press Enter
Firewall Mode [Routed]: – press enter
Enable password [<use current password>]: – press enter
Allow password recovery [yes]? – press enter
Clock (UTC): – set date
Year [2017]:
Month [Mar]:
Day [17]:
Time [06:11:12]:
Management IP address: 192.168.3.43
Management network mask: 255.255.255.0
Host name: asa
Domain name: cisco.com
IP address of host running Device Manager: – press enter
- After configurations asa will prompt to asa exe mode
- Format the flash using below command: this will take 10-20 minutes
asa# erase flash:
- Copy OS file to flash
asa# copy tftp: flash:
Address or name of remote host []? 192.168.3.29
Source filename []? asa941-lfbff-k8.SPA
Destination filename [asa941-lfbff-k8.SPA]?
Accessing tftp://192.168.3.29/asa941-lfbff-k8.SPA…!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Done!
Computed Hash SHA2: ca4413c9743cd0e59444215b771e836e
015ef147da4f2ab69bf8d917dfa1822f
6416e860f4bde6243ad9c5873aa0c172
ccd950a7fc6c8019dc09856e186c3990
Embedded Hash SHA2: ca4413c9743cd0e59444215b771e836e
015ef147da4f2ab69bf8d917dfa1822f
6416e860f4bde6243ad9c5873aa0c172
ccd950a7fc6c8019dc09856e186c3990
Digital signature successfully validated
Writing file disk0:/asa941-lfbff-k8.SPA…
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
69454656 bytes copied in 151.520 secs (459964 bytes/sec)
- Verify file with ‘asa# show flash:’ command
asa# sh flash:
–#– –length– —–date/time—— path
10 69454656 Mar 17 2017 06:40:31 asa941-lfbff-k8.SPA
- Configure Boot path
asa(config)# boot system flash:/asa941-lfbff-k8.SPA
INFO: Converting flash:/asa941-lfbff-k8.SPA to disk0:/asa941-lfbff-k8.SPA
- Enable core dump
asa(config)# coredump enable
- Save Configurations
asa(config)# copy running-config startup-config
- Check Boot image is configured correctely
asa# sh bootvar
BOOT variable = disk0:/asa941-lfbff-k8.SPA
Current BOOT variable = disk0:/asa941-lfbff-k8.SPA
CONFIG_FILE variable =
Current CONFIG_FILE variable =
- Reload device
asa# reload
Proceed with reload? [confirm]
asa#
***
*** — START GRACEFUL SHUTDOWN —
Shutting down isakmp
Shutting down sw-module
Shutting down License Controller
Shutting down File system
***
*** — SHUTDOWN NOW —
Process shutdown finished
Rebooting…..
Rom image verified correctly
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE
Copyright (c) 1994-2015 by Cisco Systems, Inc.
Compiled Thu 06/18/2015 12:15:56.43 by builders
Current image running: Boot ROM1
Last reset cause: PowerCycleRequest
DIMM Slot 0 : Present
Platform ASA5506 with 4096 Mbytes of main memory
MAC Address: 18:8b:9d:40:51:6e
Use BREAK or ESC to interrupt boot.
Use SPACE to begin boot immediately.
Located ‘.boot_string’ @ cluster 16989.
#
Attempt autoboot: “boot disk0:/asa941-lfbff-k8.SPA”
Located ‘asa941-lfbff-k8.SPA’ @ cluster 10.
###########################################################
——————–
Output Omitted!
———————
- Set ip addresses and login settings
asa(config)# conf t
asa(config-if)# int m 1/1
asa(config-if)# no ip address
asa(config-if)# int gi 1/1
asa(config-if)# ip address 192.168.3.43 255.255.255.0 -applying ip address to inside network interface
asa(config-if)# no shut
asa(config-if)# nameif inside
asa(config)# http server enable – enabling http server for asdm connectivity
asa(config)# http 192.168.3.0 255.255.255.0 inside
asa(config)# username cisco password cisco privilege 15
asa(config)# aaa authentication http console LOCAL
asa(config)# aaa authentication ssh console LOCAL
asa(config)# aaa authentication enable console LOCAL
- Copy ASDM image to ASA
asa(config)# copy tftp: flash:
Address or name of remote host [192.168.3.29]?
Source filename [asdm-761.bin]?
Destination filename [asdm-761.bin]?
Accessing tftp://192.168.3.29/asdm-761.bin…!!!!!!!!!!!!!
Writing current ASDM file disk0:/asdm-761.bin
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
asa(config)# asdm image flash:/asdm-761.bin -setting asdm for asa
- Activate ASA licenses with activation key
asa(config)# activation-key XXXXXXX XXXXXXX XXXXXX XXXXXX XXXXXX
Validating activation key. This may take a few minutes…
Failed to retrieve permanent activation key.
Failover is different.
running permanent activation key: Restricted(R)
new permanent activation key: Unrestricted(UR)
WARNING: The running activation key was not updated with the requested key.
Proceed with update flash activation key? [confirm]
The flash permanent activation key was updated with the requested key,
and will become active after the next reload.
