This blog aims to present an overview of various Cisco firewall products' features. It will not present configuration examples or get into details on intricacies of features and functions. But it will rather present a summary of what each function does without having to go through extensive configuration guides, product literature and white papers.
We will start with presenting Cisco ASA's Botnet filter. It is a licensed (requires subscription) feature. It uses Cisco Ironport technology to identify malicious traffic passing through the ASA. It can detect when infected clients attempt to phone home across any ports/protocols through the firewall by matching IP addresses and domain names against its internal database (downloaded to the ASA) and it can alert or drop the traffic based on the configuration.
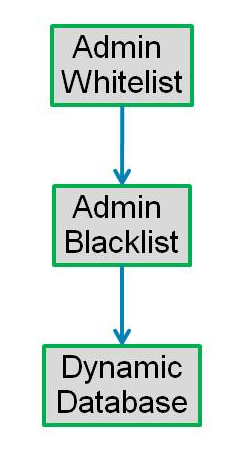
The ASA downloads all database data to its RAM. The database entries include all IP addresses/URLs and domains that are classified as malicious. On top of that the administrator can statically define Blacklisted and Whitelisted domains. Traffic that is going through the device is classified based on the database as
- Blacklist: This is traffic to or from an IP address that is considered to be malicious.
- Whitelist: This is traffic to or from an IP address that is considered to be good. It is part of administrator statically configured lists.
- Graylist: A graylist IP is one that has been resolved to one or more blacklist entries as well as one or more unknown entries.
- Unknown/None: An IP address that does not map to a domain in either a black or white list.
To summarize how the feature works, the ASA downloads the Botnet dynamic database from Cisco Ironport's servers.
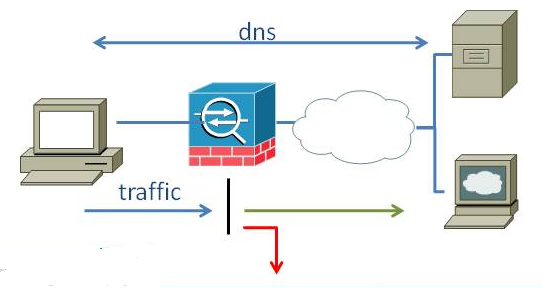
When there is a DNS request that traverses the ASA (DNS request and responses need to go through the firewall for the Botnet filter to work) the ASA snoops the IP address in the DNS response. Then it checks the DNS entry against its statically configured Whitelist, Blacklist. If there is no match it checks against the dynamic downloaded Botnet database. If there is a match either against the Whitelist, Blacklist or the dynamic Botnet database an entry is created that binds the IP address in the response with the black, white, gray, unknown property. Thus, the ASA knows that based on the Botnet feature, IP address x.x.x.x is classified as white, black, gray or unknown.
When an internal host attempts to initiate traffic destined to an IP address, the ASA checks its bindings for that IP address and if there is a match with a "black" binding entry then traffic is dropped. "White" IP addresses are let through and "gray" are dropped or permitted based on the configuration. By default graylisted traffic will be permitted. The syslogs related to Botnet filter are %ASA-4-338001 up to %ASA-4-338008 and ASA-4-338201 up to ASA-4-338204. No syslogs or statistics will be generated for "unknown" traffic. A guide on how to configure the feature can be found here.
In the future we will present other firewall features. Feedback, comments and suggestions on what readers would want to see are always welcome.
Regards,
PK
