We are excited to announce that the new REST API of global threat alerts (formerly Cognitive Intelligence and CTA) is available now to all customers of Secure Network Analytics and Secure Endpoint who have enabled the global threat alerts capability.
Read, configure, and correlate all global threat alerts data
For many organisations, being able to access their data programmatically is key. It allows them to build automation that will save time, provide a consistent experience, correlate information, and unify all their relevant security monitoring information in one place.
In order to provide these capabilities to all global threat alerts customers, all visible data in the global threat alerts dashboard is now available through the REST API. There are numerous API calls focused on getting information about alerts, with the possibility of getting them grouped per asset group or threat, and with all the additional behavioural context contained in the security events.
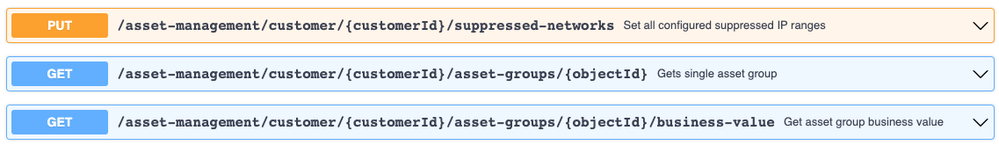
Figure 1: Global threat alerts REST API has both reading and configuring capabilities.
The API is not read-only; users are allowed to change the configuration of their global threat alerts environment.For example, you can increase the specific business value of a critical asset group or change the severity assigned to a threat.
All visible data in the global threat alerts dashboard is now available through the REST API
Stream all your alerts to a centralized SIEM
If you have a Security Information and Event Management (SIEM) solution in your network, now you can leverage the new REST API to pull alerts and all the relevant KPIs from global threat alerts into your SIEM.
In order to facilitate the collection of data, we have prepared extensive documentation and a couple of scripts that will make your life easier. One of them is aimed at automating the pulling of events to your Splunk SIEM, and the other will retrieve and renew the necessary token to authenticate securely in order to use the APIs. You can see all of them on Cisco Security GitHub.
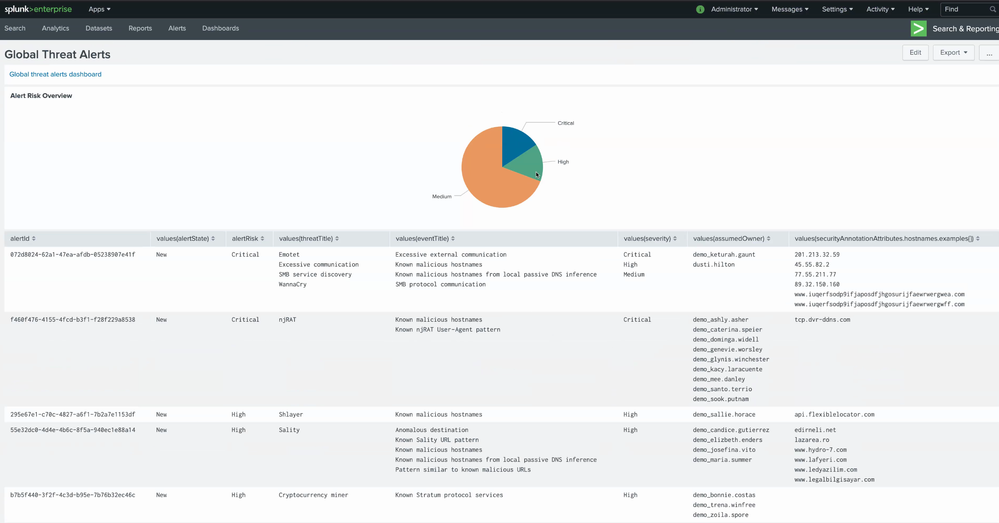
Figure 2: Now you can customize your SIEM dashboards with all the information from global threat alerts.
Many possible use cases, one API
Main use cases include:
- Export all event and behaviour context to your SIEM
- Make programmatic changes to threat/asset groups priorities
- Update alert details: state/notes
- Trigger automation/remediation workflows in your organization (for example, from SecureX)
Conclusion
Being able to access all the detections and behavioral context from global threat alerts through the REST API is very valuable; it opens up many possibilities for automation, correlation of the data, and exporting of this information to a centralized SIEM.
You can start using the global threat alerts REST API today. See all the capabilities and first steps that you need to complete on our REST API documentation site.
