For example we have 2 routers and ipsec tunnel between. Packets from lo0 to lo0 ipsec protected.
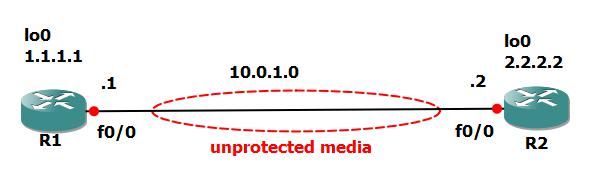
If attacker knows ipsec preshared key he can not decrypt packets traversing unprotected media.
But he can use MITM attack. And I will show you how it works.
Attacker can install 2 more routers as shown red.
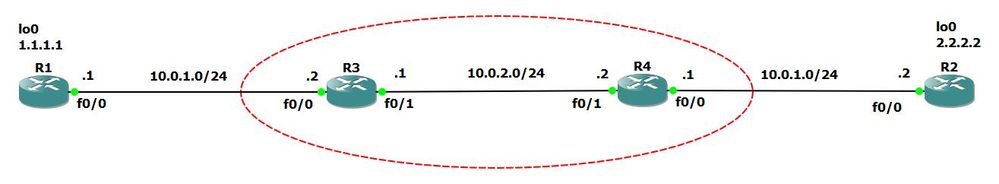 Router R1 believes it is connected to R2 and ipsec is terminated on R2, but actually on R3
Router R1 believes it is connected to R2 and ipsec is terminated on R2, but actually on R3
and R2 believes it is connected to R1 and ipsec is terminated on R1, but actually on R4
R1 lo0 can ping R2 lo0 but packets can be captured in clear between R3 and R4
Configuration files included.
