Working in Network Security for a service provider, we are often asked to monitor connections for which we have no administrative access. Examples of this are leased-line connections like MPLS circuits, but could also be extended to VPN tunnels. This article describes how to use an SLA monitor on a Cisco ASA in combination with syslog messaging to provide a "push" notification that an event has occurred that has caused the SLA monitor to fail or recover.
Topology
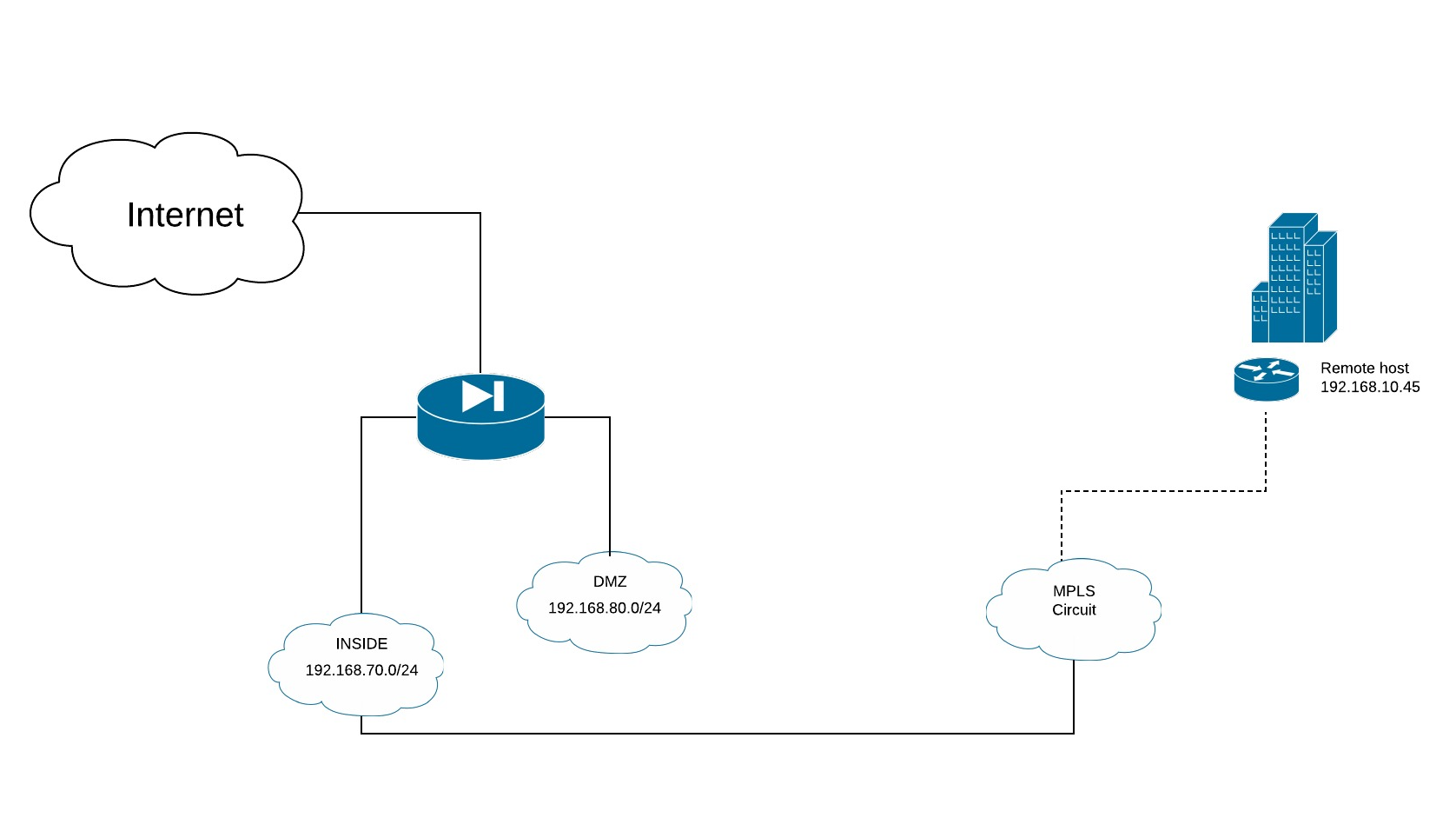
In this example, let's presume a simple topology where the ASA has a INSIDE and DMZ segment. There is an MPLS circuit attached to the INSIDE VLAN.
Objectives
Configure an SLA monitor that sources from the ASA on the INSIDE interface and ping monitors the host at 192.168.10.45, which is on the remote end of the MPLS circuit
Configure a "fake" static route that utilizes the SLA monitor
Identify the syslog messages generated by SLA failure or recovery events
Configuration
Refer to the above topology for the following configuration
SLA Monitor
sla monitor 10
type echo protocol ipIcmpEcho 192.168.10.45 interface inside
num-packets 3
frequency 10
!
sla monitor schedule 10 life forever start-time now
!
track 1 rtr 10 reachability
Static Routes
Note that we are using APIPA address space (169.254.0.0/16 - RFC 3330) to avoid creating any static route that could interfere with local or remote networks.
! Bogus route to track ensures syslog message 622001 is generated
route inside 169.254.0.1 255.255.255.255 192.168.10.45 track 1
Syslog Messages
The syslog server will need to filter on the following syslog messages. A syslog collector such as Kiwi or a more sophisticated system like Zenoss or Splunk can filter on these messages and trigger actions such as sending emails, sending text messages, or generating tickets, etc. In addition to the syslog collector, one could also configure an EEM action on the ASA responding to these syslog messages/events. The configuration provided will generate syslog message 622001 for both the failure and recovery events.
Syslog Messages Host DOWN
Mar 15 2018 17:46:08 FW-ASA : %ASA-6-622001: Removing tracked route 169.254.0.1 255.255.255.255 192.168.10.45, distance 1, table Default-IP-Routing-Table, on interface inside |
Syslog Messages Host UP
Mar 15 2018 17:43:33 FW-ASA : %ASA-6-622001: Adding tracked route 169.254.0.1 255.255.255.255 192.168.10.45, distance 1, table Default-IP-Routing-Table, on interface inside |
Summary
While this kind of configuration is not what SLA monitors were designed for, we can leverage this functionality and a bogus static route to create a syslog event for which we can push reachability changes. This is often useful when dealing with a 3rd party provider to which we have no access to the leased line provider's monitoring tools or telemetry, or where traditional monitoring methods like SNMP are not available.
One could set up a number of the monitors for multiple circuits and associate the static route APIPA address with each leased line and then, using the syslog filtering action features, create custom alerts that could contain the circuit ID, common name, contact phone numbers, and other useful information.
