- Cisco Community
- Technology and Support
- Security
- Security Blogs
- Session Hijacking and Web based Attacks
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Session Hijacking
Before Understanding Session Hijacking, first of all we need to understand What is Session?
What is a Session?
Session is semi-permanent interactive information interchange, also known as a dialogue, a conversation or a meeting, between two or more communicating devices, or between a computer and user.
Why are they needed?
Sessions are generally needed to ease authenticated communication between two or more parties. All the nodes, are not required to authenticate for every activity or action, because of the session which exists.
Types of Session Hijacking:
- Active Session Hijacking
- Passive Session Hijacking
Active Session Hijacking:
- Active session Hijacking involves hijacking a already authenticated session.
- Active Session Hijacking means that original user has logged in his account or profile and then attacker steal the cookies to hijack the active session and then disconnect the original user from the server.
WORKING:
- In Active Session Hijacking, attackers use client side scripts to steal the original users cookies by involving social engineering tactics which includes emails, private messaging on forums and on other social networking websites.
- Why we call it active session hijacking because attackers need to interact and need some actions to be performed by the victim to steal the session successfully which can raise the suspicion level.
Passive Session Hijacking:
- In passive session hijacking attackers does not hijack active session instead they capture the login credentials while the original user is trying to establish a new connection with the server, and attacker is sitting silently on the same network and recording the login credentials.
WORKING:
- Passive Session Hijacking involves the use of network sniffing tools that captures data packet and exploit the vulnerability of ARP protocol by poisoning the network. Attackers analyze those captured data to retrieve login credentials of the user.
- Why we call it passive session hijacking because attackers does not need to interact with the user and make him perform any specific actions. There is less risk of suspicion level.
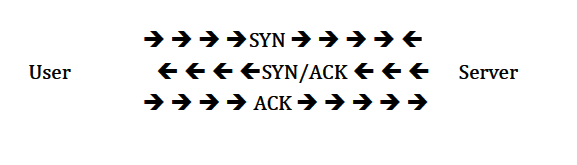
3 Way Handshake in action:
- User[192.168.0.105] initiated a connection with the server [66.220.153.11]. User sends a packet to the server with the ‘SYN’ bit set.
- The server receives this packet and sends back a packet with the SYN bit and an ISN (Initial Sequence Number) for the server.
- User sets the ACK bit acknowledging the receipt of the packet and increments the sequence number by 1.
- The two machines have successfully established a session.
TCP Session Hijacking:
TCP Hijacking is oldest type of session hijacking. TCP session hijacking actually deals with the successful prediction of the Initial sequence numbers that gets exchanged between two host. A client and the server.
Sequence Numbers are exchanged during TCP Three way handshaking.
- Host A sends a SYN bit set packet to Host B to create a new connection.
- Host B will reply with SYN/ACK bits set packet to Host A with a initial sequence number.
- Host A will reply with ACK bit set packet to Host B with Initial Sequence Number + 1
So, If attackers manage to predict the initial sequence number then they can actually send the last ACK data packet to the server, spoofing as original Host. then they can hijack the TCP Connection.
Methods of TCP Session Hijacking:
Now before predicting a initial sequence number of a TCP three way handshaking, attackers need to be in between the client and server to successfully hijack the TCP connection, for which attacker can actually use these three techniques.
- Source routing: attacker can actually use source routing in such a way that the data is being transferred between client and server through attacker. In that case attacker can see the data being exchanged and can see the Initial Sequence Number.
- Man in the middle attack: By Logically placing himself between the server and client, an attacker can similarly see the data connection going through him.
- Attacker can also use ICMP redirect to spoof himself as gateways so that data can be passed through him.
- Attacker can also hijack the TCP session by not predicting or looking for initial sequence number instead he can let the user establish a successful connection and then spoofing himself as a client by changing his MAC address with that of the original Host, attacker can send RST bit set to the server to reset the connection and starting a whole new connection from TCP three way handshaking and exchanging the new sequence numbers.
Web Based Attacks
SQL Injection
SQL which stands for Structured Query Language, is a database language designed to manage data in Relational Database Management Systems (RDBMS).
What is SQL?
- SQL stands for Structured Query Language
- SQL helps you manage Databases by letting you Insert, Update and Delete Data.
- In a nutshell, A Database is a Collection of Tables.
- A Table is collection of Cells made by Rows and Columns.
What can SQL do?
- SQL can execute queries against a database
- SQL can retrieve data from a database
- SQL can insert records in a database
- SQL can update records in a database
- SQL can delete records from a database
- SQL can create new databases
- SQL can create new tables in a database
- SQL can create stored procedures in a database
- SQL can set permissions on tables, procedures, and views
SQL Injection:
- SQL injection is a Code Injection Technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another.
- SQL Injection is used for Hacking Web Applications.
How it works?
1. The User will Provide Input to the Web Application.
- This Could be though a HTML Form (POST).
- Or a Dynamically Crafted Link (GET).
2. The Web Application will accept the Data from the User and Process it in the SQL Query as per the Web Script.
3. The Web Server will generate an Output for the User, depending upon the Script.
For Example, We enter our Login Credentials in a Login Form and Press Submit. The Server takes the Details and Checks it against its User Database. If Authenticated, you are Taken to the Desired Page.
During SQL Injection, the User will submit Malicious Input which would force the Query (which is run by the Login Script in Backend) to perform an undesired Action.
What can it Result into?
Unauthorized Use of Web Application. SQL Injection can commonly result in bypassing of User Authentication
Depending upon Database Permissions, one can also:
- Enter Data into the Database.
- Retrieved Data from the Database using SQLI.
- Data can even be Deleted.
Apart from this, one can also:
- Stop/Shutdown the SQL Server
- Gain a Web Shell
SQLi Techniques:
To Bypass Authentication, use one of the following Query in the User Input:
- ' or ‘1’ = ‘1
- “ or “1” = “1
- 1 or 1 = 1
- ‘ or 1 = 1; --
- ‘ or 1 = 1 –
To Guess Field Name:
- 1' AND table name IS NULL; --
On the Basis of the Error Produced, one can establish if the Field exists or not.
To Guess Table Name:
- 1' AND 1=(SELECT COUNT(*) FROM tablename); --
To Delete a Table:
- '; DROP TABLE tablename; --
To Write a File:
- ' union Select “data",2 into outfile "/tmp/filename.txt" –
To Get Shell:
- ' ; exec master..xp_cmdshell ' iisreset' ; --
Blind SQL injection:
Blind SQL Injection is used when a web application is vulnerable to an SQL injection but the results of the injection are not visible to the attacker. The page with the vulnerability may not be one that displays data but will display differently depending on the results of a logical statement injected into the legitimate SQL statement called for that page. This type of attack can become time-intensive because a new statement must be crafted for each bit recovered.
Tools used for SQL Server Testing:
- SQLDict
- SQLExec
- SQLbf
- SQLSmack
- SQL2.exe
- AppDetective
- Database Scanner
- SQLPoke
- NGSSQLCrack
- NGSSQuirreL
- SQLPing v2.2
Introduction to XSS (Cross Site Scripting)
- Number of Websites using a Web Scripting Language (Dynamic Websites) is rising Rapidly.
- The Rise is mainly because Web Applications are very agile, easy to use and providing great value to the users.
- However, by using Dynamic Content on the Website, your web application may become vulnerable to Cross Site Scripting Attacks.
- Also known as XSS, it is one of the most prevalent vulnerability on the Internet Today!
Cross Site Scripting (XSS)
- Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications that enables malicious attackers to inject client-side script into web pages viewed by other users. An exploited cross-site scripting vulnerability can be used by attackers to bypass access controls such as the same origin policy.
- According to a Study by Symantec, XSS based Flaws accounted for about 80% of the Total Vulnerabilities on the Websites used in the Study.
- Their impact may range from a petty nuisance to a significant security risk, depending on the sensitivity of the data handled by the vulnerable site, and the nature of any security mitigations implemented by the site's owner
Types of XSS attacks:
DOM Based (Type 0) XSS Vulnerabilities
- DOM Stands for Document Object Model
- Modern Client-Side Web Applications may take user Input from the HTML Page it self, which is processing it.
- This Input would normally be used to generate Dynamic Content on the Web Page.
- If the Input from DOM is not validated, an Attacker can add further scripts to the Web Page, which will be executed on the Client Side.
- In order to Execute a Type 0 Attack, a Higher Level of Social Engineering is required, since generally you would be required to send a Malicious Link to a User. The Link to the Malicious web page will opens a vulnerable HTML page which is installed locally on user's computer. This is done using JavaScript. Now this HTML Page can execute any commands with Local Privileges which the User has.
Non-Persistent (Type 1) XSS Vulnerabilities
- The Most Common Type of XSS Flaw
- It is a Server Side Vulnerability
- When a Web Server takes any input from a User and returns the same back to the User without any Validation, This leads to a Non-Persistent XSS Vulnerability.
Generally, when combines with a Social Engineering Attack, it can cause Security Issues over User Data.
In a Sample Scenario, Consider this:
- A is a Registered and frequent user of a Online Payment Website - PayPal.
- An Attacker Notices a XSS Flaw in a webpage of PayPal. This Webpage would display anything that you enter in an Input Field or Link.
- The Attacker Crafts a Special URL which sends such input to the Website that it includes the Attacker’s JavaScript on the Page.
- Now the Attacker does Mass Mailing, Generating Mails which seem to be from PayPal and contain this Malicious URL. Once such Email Reaches A.
- A clicks on the Link. The Web Page calls the JavaScript which A had placed using the Link. This JavaScript can Steal A’s Cookies which have been placed by PayPal and send it to the Attacker. Your Web Browser will not block Access to the Cookie it since it was accessed by the PayPal’s Website it self.
- The Attacker now has access to A’s Cookie which will Lead to the Account being Compromised.
Persistent (Type 2) XSS Vulnerabilities
- High Risk and a Crucial Vulnerability
- It is a Server Side Vulnerability
- This Attack is similar to Type 1. The User Input would be Taken and processed on the Webpage without Validating it. However, the Biggest issue here is that the Input is Stored on the Server it self and will be executed by the Web Page, every time the user visits this Web Page.
- No User Re-direction or Social Engineering is Required.
- The Script can also be Self Replicating which would make it a Web based Worm.
Consider a Scenario:
- An Attacker finds a Flaw in a Popular Blog in the User Comment Input.
- The Attacker creates a Special Code which is posted as Comment and contains link to a Malicious JS.
- Now, whenever someone would open this Blog Post, the User comment would be displayed ant the JS would also be Executed. The JS posting from the Blog can execute any Commands.
Scope
- XSS Attacks be used for the following:
- Compromising and Hijacking Accounts
- Stealing User Cookies
- Defacing Websites
- Phishing Attacks
- Posting False or Hostile Content
How to protect against XSS:

- HTML Sanitization.
- Validation, Escaping & Filtering of User Input.
- Be cautious when reading emails, discussion boards, posts, etc.
- In IE, turn security settings on High.
ALSO :
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: