Approximately 37% of the customers get stalled in the implementation of their Secure Endpoint solution. Here are 4 strategies you can use to get the most out of your investment in Secure Endpoint.
1. Utilise features that stop day zero attacks
As a starting point, utilise detection features to help uncover exploits and vulnerabilities in user devices to fend off day zero style attacks. Key base features to implement are Malicious Activity Prevention (MAP) and Exploit Prevention (EP). Here’s where Malicious Activity Prevention and Exploit Prevention fall in the protection spectrum.
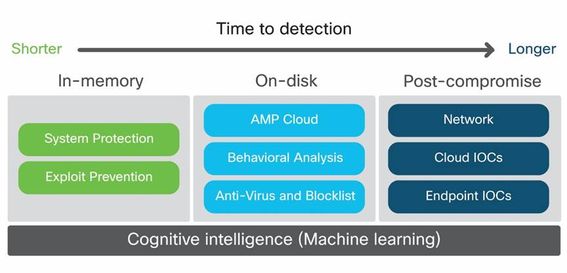
Check out this post if you want to utilise this feature in your environment or read more about exploit prevention in detail in this whitepaper
2. Employ additional features
On top of MAP and EP, there are some other protection mechanisms you can use to broaden the scope of protection:
- System Process Protection (connector version 6.0.5 and later) blocks attacks on critical Windows system processes compromised through memory injection attacks by other processes.
- Device Flow Correlation allows to monitor network activity and determines which action the AMP Connector should take when connections to malicious hosts are detected.
- Behavioral Protection prevents malicious activity that matches a set of behavioral signatures.
If you wish to utilise these features, check out this blog post which guides you through enabling one of them. Get more details about MAP, EP, and other protection mechanisms in this whitepaper.
3. Expand connector deployment to first group of users
Once you complete alpha and beta deployment (Lab or Gold user groups), it’s time to go into production and start expanding it into other user devices in your organisation. Cisco recommends using Cisco AnyConnect client, Microsoft SCCM, Altiris, Jamf etc. As a guideline, you should aim to deploy anywhere between 25-50% of the licensed connectors. To help you with this, here's a primer on the deployment strategy in this best practices guide.
To learn more about how you can expand your connector deployment, check out this blog post
3. Convert connectors from Audit to Protect mode
Lastly, and perhaps the turning point in the deployment, is to convert connector groups into protect mode. Audit is a great way to tune policies in the alpha stage which helps you identify exclusions, but it doesn’t prevent any malicious activity. About 55% of the users fail to convert connectors to protect mode, resulting in slow time to value and your organisation is left vulnerable to malware. We recommend extending the below features to at least 30% of your licensed connectors at this point of your roll out. Here’s a good example of a policy set you can use for Workstations:
● Files: Quarantine
● Network: Block
● Malicious Activity Protection: Quarantine
● System Process Protection: Protect
● Script Protection: Quarantine
● Exploit Prevention: Block
● Exploit Prevention - Script Control: Audit
● Behavioral Protection: Protect
We have a detailed walk through on how to turn on protect modes on detection engines in this blog post here. Read more about each of the features described above in the Secure Endpoint user guide.
Comment below with questions on these features.
