When we discover the Email Security Appliance ESA first time, you will be lost by its complex logic and the words used under the GUI, and how the ESA’s components interacts. In other words, simply how the Packet Flow works on Cisco ESA.
To be honest, it’s the most complex product, I always said that Unity Connection for mailbox solution is the most complicated product, but finaly ESA is much complex.
To understand any product, you need to know how the packet is processed.
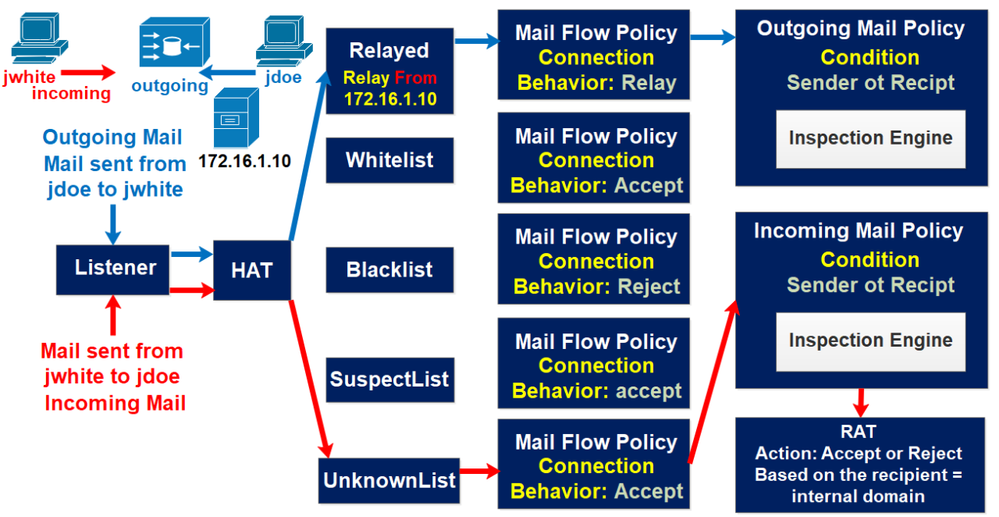
To start, Cisco ESA is based on listeners, listeners are like SMTP service running on interface.
The purpose is that we need to listen from two places:
-Public: We need public listener for incoming email, in other word ESA listens, controls and receives connection from external hosts or domains. Who is sending email for US.
The control of these connection is based on HAT (Host Access Table)
A HAT is a sender group that decides which mail policy will process the mail. If the Mail Policy associated to this HAT is defined with an Action: ACCEPT “Connection Behavior”, this means that this is for incoming mail. ESA applies an incoming mail policy with a bunch inspection engine.
-Private: We need private listener for outgoing mail, in other words, we need to route email sent from your internal domain to external hosts. If the Mail Policy associated to this HAT is defined with an Action: RELAY “Connection Behavior” and the sender IP internal SMTP server. This means that this is for outgoing mail. ESA applies an outgoing mail policy with a bunch inspection engine.
Now what about RAT Recipient Access Table? this only for incoming mail, the purpose is to relay the incoming mail from external host to our internal domain, here we specify the list of internal domain allowed to receipt the external mails. This is why we find in the RAT configuration the “Recipient” field.
To be more clear:
HAT and RAT are important components.
HAT is used to ACCEPT incoming mails and also to RELAY the outgoing mails FROM the internal server.
RAT is used to RELAY the incoming mails TO the internal server.
Notice, the definitions seems to be similare but the words “FROM” and “TO” are very importants to distinguish between them.
The second part of confusion is the Mail Flow policies, Incoming Mail Policies and Outgoing Mail Policies.
Mail Flow Policies is associated to HAT in order to answer two questions:
1-is it an incoming mail? so send to Incoming Mail Policies for further inspection using the Inspection ENGINE like Anti-virus, Anti-Spam, AMP, Content Filters etc…
2-is it an outgoing mail? so send tio Outgoing Mail Policies for further inspection using the Inspection ENGINE like Anti-virus, Anti-Spam, AMP, Content Filters etc…