- Cisco Community
- Technology and Support
- Data Center and Cloud
- Server Networking
- Re: SG350 promiscuous trunk?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2019 09:10 PM
Hello,
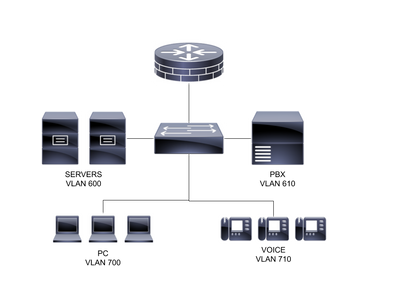
I have a SG350-52-K9-NA switch, that I would like to use for L2 as shown in the diagram below. I purchased this switch thinking I would be able to use the PVLAN feature to isolate PCs from each other, yet still permit traffic to and from other VLANs. From what I can tell (from p. 223 of the manual), this switch lacks the ability to create the promiscuous trunk port, that I think is necessary for implementing this design. I'm wondering whether anyone has any alternative configuration ideas, using this switch, which would allow me to accomplish my design goals?
The design goals of the project are:
- Prevent communication between PCs (without depending on host software firewalls)
- Allow PCs to talk to servers, which are hosted on a different subnet, behind a firewall
- Allow handsets to communicate with the PBX, between VLANs, but not with PCs or servers
- Use a router on a stick (single port) to route between all VLANs
- Use a single subnet and DHCP pool for the PC VLAN, so that address management remains uncomplicated (ie I don't want to use a /30 subnet per PC)
- Enforce network access based on DHCP lease only (ie use DHCP snooping, ARP inspection and IP source guard)
Design constraints
- Low budget (hence the SG350 and an open source router/firewall
- Firewall has two interfaces (WAN and LAN), so switch needs to tag all VLANs on the uplink to the firewall
Solved! Go to Solution.
- Labels:
-
Server Networking
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 05:55 PM - edited 01-15-2020 05:59 PM
Answering my own question, for anyone that comes across this later.
The protected ports feature does exactly what I need. The protected port feature provides a subset of the PVLAN feature set. Essentially, access ports can be used as PVLAN Isolated ports and a trunk port acts as a promiscuous PVLAN port for all connected VLANs. The protected port feature does not include the Community PVLAN functionality or the ability to trunk PVLANs across switches, but it's perfect for my requirements.
Here are the steps needed to configure the SG350 for the design above.
- Enable the protected port feature on all the PC and Phone ports
- Leave the PC and Phone ports as access ports
- Assign VLAN 700 to the PC ports, untagged
- Assign VLAN 710 to the Phone ports, untagged
- Plug the PBX into an access port with VLAN 610 untagged
- Plug the servers in access ports with VLAN 600 untagged
- Enable DHCP snooping, IP Source Guard and ARP inspection on the switch (set the trunk port as a trusted port, with all the other ports as untrusted)
- Plug the router/firewall into a trunk port with tagged VLANs 600, 610, 700 and 710
- Set up the necessary zones, rules and routes, on the firewall, to filter and route traffic as desired between the VLANs
- Use the DHCP server on the firewall/router to hand out IPs from a single subnet per VLAN (no need to use a DHCP relay with Option 82, because the DHCP server will be able to "see" each VLAN as an interface on the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2020 05:18 AM
Greetings.
Maybe try posting over in the https://community.cisco.com/t5/small-business-switches/bd-p/5976-discussions-small-business-switches area as they tend to cover the switches of that nature over there.
Kirk...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 05:55 PM - edited 01-15-2020 05:59 PM
Answering my own question, for anyone that comes across this later.
The protected ports feature does exactly what I need. The protected port feature provides a subset of the PVLAN feature set. Essentially, access ports can be used as PVLAN Isolated ports and a trunk port acts as a promiscuous PVLAN port for all connected VLANs. The protected port feature does not include the Community PVLAN functionality or the ability to trunk PVLANs across switches, but it's perfect for my requirements.
Here are the steps needed to configure the SG350 for the design above.
- Enable the protected port feature on all the PC and Phone ports
- Leave the PC and Phone ports as access ports
- Assign VLAN 700 to the PC ports, untagged
- Assign VLAN 710 to the Phone ports, untagged
- Plug the PBX into an access port with VLAN 610 untagged
- Plug the servers in access ports with VLAN 600 untagged
- Enable DHCP snooping, IP Source Guard and ARP inspection on the switch (set the trunk port as a trusted port, with all the other ports as untrusted)
- Plug the router/firewall into a trunk port with tagged VLANs 600, 610, 700 and 710
- Set up the necessary zones, rules and routes, on the firewall, to filter and route traffic as desired between the VLANs
- Use the DHCP server on the firewall/router to hand out IPs from a single subnet per VLAN (no need to use a DHCP relay with Option 82, because the DHCP server will be able to "see" each VLAN as an interface on the firewall.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide