- Cisco Community
- Technology and Support
- Small Business Support Community
- Switches - Small Business
- Re: Solution was easy for me.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RADIUS authentication SF300-24P
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2012 01:49 AM
RADIUS authentication SF300-24P
We have just purchased 20x SF300-24P switches to be installed at our remote offices and we are unable to get RADIUS authentication to work. We already use RADIUS on all our primary network CISCO switches (e.g. 4506s¸ 3560s, 3750s, AP1231Gs,etc) and these work fine so we know the RADIUS server is working.
We are trying to use RADIUS authentication to gain management access onto these switches. Quite simply although we can see that the RADIUS server is accepting the username and password being sent, however the switch says “authentication failed” when to receives the response. We are using Microsoft NPS RADIUS Clients for authentication purposes.
We have upgrade the switches to the latest firmware 1.1.2.0, via the console it seems to have a very cut down IOS version so we cannot use the typical CISCO command set to configure the RADIUS as we normally would. Looking at the web GUI there seems to be a number of options missing including the Accounting port. When debugging is switch on there is no indication to say that any of the settings have been misconfigured.
Any advice you could offer would be gratefully received.
Mike Lewis
- Labels:
-
Small Business Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2012 12:45 AM
Well,
now reading your "
the reason i called the auth logic broken was that radius returned a user not found error, not user auth failed", I got confused what do you mean with "radius returned" ?!? Do you mean AAA server sends something like that (I don't have time to study full RADIUS spec), or WEB GUI of the switch (based on radius method) announces this on screen? Be exact. If the earlier is the case, then I don't understand why solve your case at this forum.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2012 04:17 PM
In my RADIUS logs, i get the following 2 lines when i try to login with the local default (cisco/cisco) ID:
rlm_krb5: [cisco] krb5_g_i_t_w_p failed: Client not found in Kerberos database
Login incorrect ( [ldap] User not found): [cisco] (from client switch port 0)
these are the messages that the RADIUS servers logs via syslog. i would have to fire up a capture to get the exact response that the switch sees.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2013 11:59 PM
Hello,
can someone tell me in short what i have to do for successful login into sg300-10 switch with latest 1.2.7.76 firmware. Authentication is against FreeRadius, which sends Access-Accept with
Service-Type = Administrative-User
Cisco-AVPair = "shell:priv-lvl=15"
but http login interface is saying that username or password is incorrect and in log is:
%AAA-W-REJECT: New http connection, source 192.168.110.101 destination 192.168.253.3 REJECTED
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2013 03:19 PM
i would imagine you got the Access-Accept message by running "radiusd -X", right? stop the running service and run it from the command line, if you didnt. if the above is the output from that, them maybe you need to figure out the quoting around the reply strings. since i no longer have radius auth freestanding (the auth is against LDAP/Kerberos), i can only tell you what i have in there.
i have the radius schema loaded into LDAP, and my user object has this attribute:
radiusreplyitem: Cisco-AVPair = "shell:priv-lvl=15"
when i run "radiusd -X" and log into my switch, i see:
Cisco-AVPair = "shell:priv-lvl=15"
it might be that you dont have the correct "client" or other setting set correctly for radius. clients.conf needs to have:
client ip.add.re.ss {
secret =
shortname = switch
nastype = cisco
}
note that the above has to be added to the conf file and the "secret" line under "client localhost" must match the "secret" line under the client definition you add. excluding the LDAP/Kerberos config changes i made, that is what i think you need to get things working. the "radiusd -X" debugging is really helpful, and i would suggest using it if you havent done so already. good luck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 11:45 AM
Brendan
I´m using SF300-8 with the latest fimware version - 1.3.0.62. The configuration of my Freeradius is correct, because I can authenticate the users on other cisco switches and routres, and the conf is the same as shown above. The configuration of the SF300 is very strait forward, but the SF300 still having problem with the authentication...
Do you know if there any problem with radius authentication with this firmware?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 11:46 AM
I´m using SF300-8 with the latest fimware version - 1.3.0.62. The configuration of my Freeradius is correct, because I can authenticate the users on other cisco switches and routres, and the conf is the same as shown above. The configuration of the SF300 is very strait forward, but the SF300 still having problem with the authentication...
Do you know if there any problem with radius authentication with this firmware?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2014 12:36 AM
Was a solution ever fond to this issue??
I just bought 5 SG300-10 and I can't get Radius authentication to work :-(
I am using Microsoft NPS as Radius server, and this setup is working fine with my 200+ Cisco Catalysts.
The Radius server logs tells me it authenticates the users from the SG300's just fine, and I have tried returning these Cisco-AV-Pairs to the SG300:
"shell:priv-lvl=15"
shell:priv-lvl=15
"priv15"
priv15
But none gives me access to the switch.
Switches are runing software 1.4.0.88
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2014 06:22 AM
Hi Denis,
It works when Accept message has Service Type set to Administrative and not Login.
Regards,
Aleksandra
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 11:36 AM
what is the exact configuration can you post we have the same issue, any advise how to fix it out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 04:18 AM
Hello. Need Any help.
We've bought 5 switches SG350-10P, and no one of them did not authenticate users with AAA.
Cisco config:
hostname AS-NNNNNNN encrypted radius-server key XXXXXXXXXXXXXXXXXXXXX encrypted radius-server host 172.16.X.YYY retransmit 2 key XXXXXXXXXXXXXXXXXXXXXXXx priority 1 usage login radius-server host source-interface vlan 9 radius-server host source-interface-ipv6 vlan 1 aaa authentication login SSH local radius aaa authentication enable SSH enable radius aaa authentication login Telnet local radius aaa authentication enable Telnet enable radius aaa authentication login Console local radius aaa authentication enable Console enable radius line telnet login authentication Telnet enable authentication Telnet password QQQQQQQQQQQQQQQQQQQQQQQQQ encrypted exit line ssh login authentication SSH enable authentication SSH password QQQQQQQQQQQQQQQQQQQQQQQQQ encrypted exit line console login authentication Console enable authentication Console password QQQQQQQQQQQQQQQQQQQQQQQQQ encrypted exit ip ssh server ip ssh password-auth interface vlan 9 name MGMT ip address 172.16.X.Y MMM.MMM.MMM.MMM exit ip default-gateway 172.16.X.1
Windows NPS next:
| 2147483503 | 2019-Sep-17 13:45:48 | Warning | %AAA-W-REJECT: New ssh connection, source 172.16.X.Y destination 172.16.X.Z REJECTED |
| 2147483504 | 2019-Sep-17 13:45:48 | Warning | %AAA-W-REJECT: New ssh connection, source 172.16.X.Y destination 172.16.X.Z REJECTED |
| 2147483505 | 2019-Sep-17 13:45:48 | Warning | %AAA-W-REJECT: New ssh connection, source 172.16.X.Y destination 172.16.X.Z REJECTED |
All other Devices (2960, 1900) are use this NPS server without problems.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2016 05:32 AM
Solution was easy for me. Service-Type needs to be set to Administrative-User
a.florio Auth-Type := System
Service-Type = Administrative-User,
cisco-avpair = "shell:priv-lvl=15"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 06:09 AM
In Windows 2k16 - there is only Service-Type = Administrative
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 06:33 AM
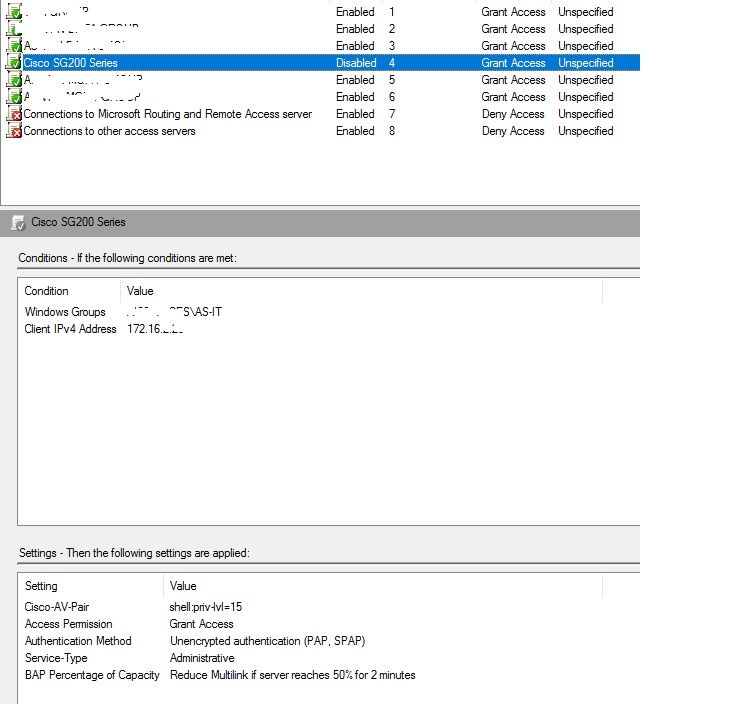
All done: check in log that your first polices are not used. I made my SG300 policy on first place
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2022 08:19 PM
What exactly did you configure?
I have configured NPS as per your screenshots.
Verified that the correct policy is being accessed.
Still get an invalid user name or password at the login screen.
NPS does authenticate the user and return and access granted message.
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide