- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: aaa authentication dot1x default group radius none
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 05:56 AM
Hi,
I do have Radius implemented for 802.1x,
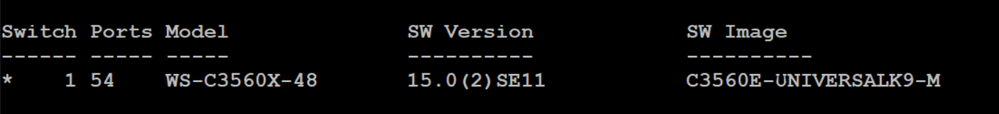
I am using the following switch:
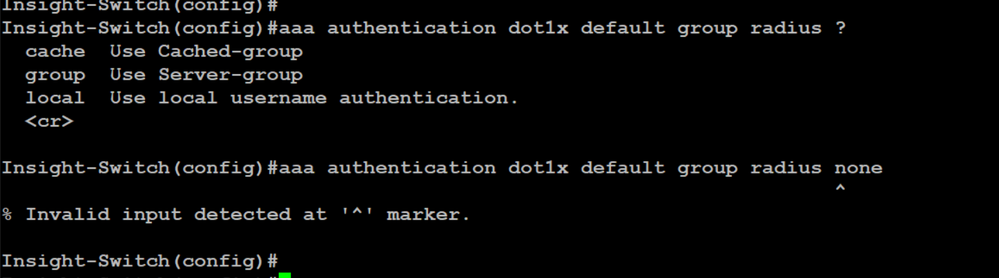
I want the switch to allow user access if Radius server is down. The issue with the following command, I dont get "none" option:
aaa authentication dot1x default group radius none
According to Cisco documentation that this command is valid:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr-book/sec-cr-a1.html
Can you please help me on what to do on this ?
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 08:16 AM - edited 04-09-2019 08:22 AM
Hi,
Thanks for the feedback. With multiauth mode you can also try the below interface command:
"authentication event server dead action reinitialize vlan 1"
(instead of "... authorize vlan 1").
There are known bugs related to the critical Vlan for various platforms and various IOS releases. If unsuccessful you MAY consider to update your IOS.
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 04:36 AM
any help please ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 05:13 AM - edited 04-02-2019 07:18 AM
Hi,
I am not sure what is your VLAN and Switch configuration but try like this:
aaa new-model ! aaa authentication dot1x default group radius aaa authorization network default group radius ! dot1x system-auth-control ! interface GigabitEthernet1/0/2 switchport mode access authentication event fail action authorize vlan 2 --> If authentication failed then Assign VLAN 2 authentication event no-response action authorize vlan 3 ---> If no responce then it will assign VLAN 3 authentication event server dead action authorize vlan 3 ----> If all confgured server dead marked
authentication host-mode multi-host authentication port-control auto dot1x pae authenticator
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 05:57 AM - edited 04-02-2019 06:06 AM
Hi,
Yes, the option "none" is not available with your IOS release. You can achieve what you aim via the "authentication event server dead action authorize" interface configuration command.
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2019 06:42 AM
Hi dears,
sorry for the late update on this,
I tried the suggested commands, but unfortunately the issue still persists, the switch does not allow the endpoint to access the network if Radius is down. I tried several variations of the following commands:
interface GigabitEthernet0/17
switchport mode access
authentication event fail action authorize vlan 1
authentication event server dead action authorize vlan 1
authentication event no-response action authorize vlan 1
authentication event server alive action reinitialize
authentication host-mode multi-auth
authentication order dot1x
authentication priority dot1x
authentication port-control auto
authentication periodic
authentication violation restrict
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
snmp trap link-status permit duplicates
dot1x pae authenticator
dot1x timeout quiet-period 30
spanning-tree portfast
end
anything can be done?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 08:16 AM - edited 04-09-2019 08:22 AM
Hi,
Thanks for the feedback. With multiauth mode you can also try the below interface command:
"authentication event server dead action reinitialize vlan 1"
(instead of "... authorize vlan 1").
There are known bugs related to the critical Vlan for various platforms and various IOS releases. If unsuccessful you MAY consider to update your IOS.
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 03:18 AM
Thank you, this solved my problem.
"authentication event server dead action reinitialize vlan 1"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide