- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2018 11:13 PM - edited 03-08-2019 01:42 PM
Hello Community,
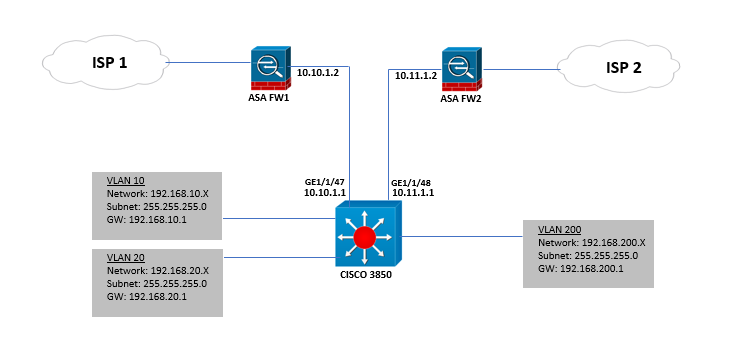
We have this network design:
Could you please help me how to configure PBR on our Cisco 3850 switch.
We have VLANs 10 and 20 and added a Guest Wifi network on VLAN 200. Also we have two ISP and two firewalls. Right now all traffic to internet is routed on ISP1 and works well.
We need to achieve the following:
- VLAN 10 and 20 traffic going to internet should utilize the ISP1.
- VLAN 200 traffic going to internet should utilize the ISP2.
Thank you in advance.
Solved! Go to Solution.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 09:36 AM
In an earlier post it showed that you were applying the policy route map to the interface
interface vlan 200
ip policy route-map PBR
but this most recent post does not show the route map applied to the interface
interface Vlan200
ip address 192.168.200.1 255.255.255.0
ip nat inside
end
You need the route map applied to interface vlan 200 for the PBR to work as expected.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 10:21 AM - edited 02-14-2018 10:30 AM
Hi Richard,
That's my issue now. I have applied the policy route-map on the int vlan 200 but it's not taking.
Doing sh run int vlan 200 will not show the policy being applied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 12:33 PM
Thanks for this information. What version of code is this 3850 running?
In looking at the release notes it appears that the implementation of PBR for the 3850 is not full featured in comparison to IOS routers. I wonder if it would make any difference if you remove the parameters for verify-availability and for track from your route ma.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 01:24 PM - edited 02-14-2018 01:29 PM
Hello
Adding to ricks comments what sdm template are your using?
sh sdm prefer
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 01:56 PM
Hi Paul,
See below output
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 01:54 PM
Hi Richard,
Switch version is 03.06.06E.
After removing the line set ip next-hop verify-availability 10.11.1.2 1 track 10 under route-map PBR the policy is applied on int vlan 200. I will test tomorrow in the site when users are connected on that VLAN. I am currently accessing the switch remotely and no users are active yet. I'll let you know. Thanks!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2018 04:25 AM - edited 02-15-2018 07:00 AM
Hi Richard,
After checking on the users traffic, i can see PBR is working fine now. And also checking on users browser and typing "What's my IP address"it will show the Public IP of the ISP2 so it means internet request from VLAN 200 is routed on the correct ISP.
Removing the parameters for verify-availability and for track from the route map resolved my issue.
This is the working configuration:
!
ip sla 5
icmp-echo 10.11.1.2 source-ip 10.11.1.1
ip sla schedule 5 life forever start-time now
access-list 100 permit ip 192.168.200.0 0.0.0.255 any
!
route-map PBR permit 10
match ip address 100
set ip next-hop 10.11.1.2
!
interface Vlan200
ip address 192.168.200.1 255.255.255.0
ip nat inside
ip policy route-map PBR
Thanks a lot for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2018 06:56 AM
Thank you for posting back to the forum to confirm that PBR is now working, for confirming that the issue was the attempt to use verify-availability, and for giving the working config. I am glad that our suggestions led you to the solution. Thank you for marking this question as solved. This will help other readers in the forum to identify discussions that have helpful information.
Verify-availability is a nice feature in PBR. It is unfortunate that your version of code does not support it. Perhaps a newer version of code does support it or perhaps Cisco will add this in a future release.
In addition to the specifics about PBR I believe that there are some important lessons to be learned from this discussion:
- features like PBR are implemented differently on different platforms. Just because something works on a router does not necessarily mean that it will work on a layer 3 switch. And something that works on one layer 3 switch does not necessarily mean it will work on a different model of layer 3 switch.
- if you are having difficulty in implementing something, then start with a very simple basic config for that thing. Once you have the simple basic config working then add features till either you have the whole thing working or until you find the feature that does not work on that platform.
- we tend to think that layer 3 switches like 3850 are equivalent to routers. This reminds us that there are some subtle differences.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2018 05:16 AM
Hello Richard,
I have a quick question.
If someone is using VPN client, does the PBR still work?
We know that VPN clients will changed their source IP address and how the switch behave in this case?
Thanks and regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2018 08:35 AM
There was not mention of vpn in the discussion up to this point so we do not know how it is implemented. Would I be correct in assuming that the vpn is running on one of the ASA and the client accesses resources in vlan 200 from the ASA? And it is not clear whether you want the PBR to process for the vpn client or not.
Even though we do not know how or where the vpn is running I believe that we can still answer your question. The way that you have configured it PBR is running on interface vlan 200 and it looks for any IP packet arriving on the interface from a device with an IP address of 192.168.200.? and forwards that packet to the ASA connected to ISP2. (remember that access list 100 does permit 192.168.200.0 to any). So it does not matter what address the vpn client is using. If the packet has source address of 192.168.200 then PBR is going to process it. If you did not want PBR to process packets from vpn client then you would need to alter access list 100 to deny packets with destination address used by vpn client before it does the permit any.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 09:55 AM
Hi Richard,
Thank you for your response.
Actually, the client is located inside on VLAN 200 and accessing the Internet, and if a PBR is working well should be routed on ISP 2. Some clients on guest WiFi (VLAN 200) are using mobile phones with VPN enabled on them (commercial VPN) to bypass the firewall. Our Firewall for guest network have policies to block some websites and applications but we cannot control the users from using their own VPN enabled mobile device to access blocked websites and applications.
If you said,
So it does not matter what address the vpn client is using. If the packet has source address of 192.168.200 then PBR is going to process it. If you did not want PBR to process packets from vpn client then you would need to alter access list 100 to deny packets with destination address used by vpn client before it does the permit any.
I'm assuming that the PBR doesn't work well because the network traffic on the ISP 1 is been affected with the heavy traffic from guest users. If i look at our bandwidth utilization on ISP 1, it is reaching the maximum and the weird thing is why the inside interface of the Firewall 1 have high throughput and it gives a warning to our ISP 1 that we are reaching 80-90% bandwidth utilization. Why the inside zone of the firewall 1 is giving warning to the ISP? It should be the outside zone which is the interface connecting to ISP.
INSIDE ZONE THROUGHPUT
INSIDE ZONE THROUGPUT
During the heavy traffic, if i check the wireless controller to see what's going on, i can see some users on guest WiFi network are utilizing high bandwidth usage. If i disable this users on the WC, i observe that the bandwidth utilization on ISP 1 decreases but on ISP 2 is not affected.
My question is, why the ISP 1 is affected with heavy bandwidth usage of users in Guest network? And why the inside zone of firewall 1 high throughput is affecting the ISP 1?
Need your advise.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2018 08:37 AM
To be able to answer well your question I need to understand what IP address these users are using. My assumption was that they were using addresses in 192.168.200. And in that case they should have been forwarded to ISP 2. If they are using addresses that are not 192.168.200 then the situation you are describing would make good sense. So what IP addresses are these clients using?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2024 04:00 AM
I have the same concern sir but i am not really savvy with switch PBR config. I do have C3850 switch and i want to route my users from vlan 30 to FW1 which is fortigate and i want to route users from vlan 50 to FW2 which is also fortigate.
may i ask sir if i need to create a pbr config for both routes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2024 09:59 AM
There is much that we do not know about your environment and that makes it difficult to give good advice. In general I would say that you do not need PBR for both routes. One of those probably could use the normal default route, and the other would use PBR.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2024 10:14 AM
also 1 more thing sir, is it necessary to use ip nat inside to the involved vlan?