- Cisco Community
- Technology and Support
- Networking
- Switching
- Need help on access-list
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 06:22 PM - edited 03-07-2019 10:22 AM
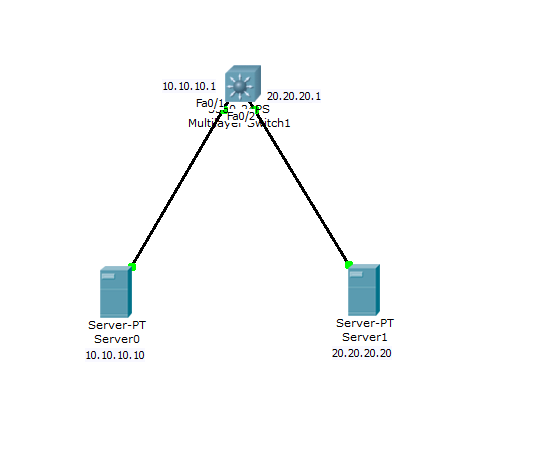
This is my topology.
I have created two vlan (201 and 202)
I want to create an access-list on the layer 3 switch.
Server0 must be able to connect to server1 using HTTP only and deny any other ports.
Server1 must also be able to connect to Server0 using HTTP only and deny other ports.
Please do help me I don't know what I am doing wrong.
Thank you in advance
Below is my config:
version 12.2
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname Switch
!
!
!
ip routing
!
!
spanning-tree mode pvst
!
!
!
interface FastEthernet0/1
switchport access vlan 201
switchport mode access
!
interface FastEthernet0/2
switchport access vlan 202
switchport mode access
!
interface Vlan1
no ip address
shutdown
!
interface Vlan201
ip address 10.10.10.1 255.255.255.0
ip access-group 101 in
!
interface Vlan202
ip address 20.20.20.1 255.255.255.0
ip access-group 102 in
!
ip classless
!
!
access-list 101 permit tcp 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 eq www
access-list 102 permit tcp 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 eq www
!
!
line con 0
line vty 0 4
login
!
!
!
end
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 07:21 PM
I believe your problem lies with return traffic. When 10.10.10.10 sends an http request to 20.20.20.20 all is fine. But when 20.20.20.20 replies to 10.10.10.10 it is using the source port of 80 and a different destination port.
So what should work is this:
access-list 101 permit tcp 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 eq www \\ When accessing the website on 20.20.20.0/24
access-list 101 permit tcp 10.10.10.0 0.0.0.255 eq www 20.20.20.0 0.0.0.255 \\ When replying to http requests from 20.20.20.0/24
access-list 102 permit tcp 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 eq www \\ When accessing the website on 10.10.10.0/24
access-list 102 permit tcp 20.20.20.0 0.0.0.255 eq www 10.10.10.0 0.0.0.255 \\ When replying to http requests from 10.10.10.24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 07:19 PM
Hi,
It should be like ths.
access-list 101 permit tcp 10.10.10.10 0.0.0.0 20.20.20.20 0.0.0.0 eq www
access-list 102 permit tcp 20.20.20.20 0.0.0.0 10.10.10.10 0.0.0.0 eq www
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 07:21 PM
I believe your problem lies with return traffic. When 10.10.10.10 sends an http request to 20.20.20.20 all is fine. But when 20.20.20.20 replies to 10.10.10.10 it is using the source port of 80 and a different destination port.
So what should work is this:
access-list 101 permit tcp 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 eq www \\ When accessing the website on 20.20.20.0/24
access-list 101 permit tcp 10.10.10.0 0.0.0.255 eq www 20.20.20.0 0.0.0.255 \\ When replying to http requests from 20.20.20.0/24
access-list 102 permit tcp 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 eq www \\ When accessing the website on 10.10.10.0/24
access-list 102 permit tcp 20.20.20.0 0.0.0.255 eq www 10.10.10.0 0.0.0.255 \\ When replying to http requests from 10.10.10.24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 07:43 PM
Thank you very much for all your help.
@mahmoodmkl
thanks for the respose bro
i used
access-list 101 permit tcp 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 eq www
access-list 102 permit tcp 20.20.20.0 0.0.0.255 10.10.10.0 0.0.0.255 eq www
in order to allow all http connections from the 10.10.10.0 /24 network or 20.20.20.0/24.
@gabriel hill
Thank you for you help sir that fixed my problem.
I have another question regarding the config you game.
I needed to specify the return destination and port because I am using a layer 3 switch and it is stateless? correct sir?
also another question why do I need to put the return access-list in the Inward direction instead of out?
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 08:02 PM
\\ I needed to specify the return destination and port because I am using a layer 3 switch and it is stateless? correct sir?
Yes that is correct. You could do some simple CBAC that would make this stateful.
\\ also another question why do I need to put the return access-list in the Inward direction instead of out?
Simply because it's easiest that way (At least for my brain, left-to-right kind of guy). You could make it work with the "out" direction but then your logic changes for your ACL's. The "in" and "out" direction is subject to where the traffic is coming from.
For example: Traffic coming from 10.10.10.0 going to 20.20.20.0
ACL "IN" vlan 201 THEN----> "OUT" vlan 202
So in the "out" direction on vlan 202 you would need to allow 10.10.10.0 to go to 20.20.20.0 (opposite of the "in" direction on vlan 202)
So to use the "OUT" direction you would have to reverse your ACL's. Simple apply 101 "OUT" on vlan 202 and ACL 102 "OUT" on vlan 101.
I hope this makes sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2012 08:30 PM
@gabriell Hill
Thank you very much for all the help I get it now
It has something to do with the three way handshake.
best regards and have a great day.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide