- Cisco Community
- Technology and Support
- Networking
- Switching
- Normal practice for management -how access many vlans from one s
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2012 04:44 AM - edited 03-07-2019 08:04 AM
I am fairly new to networking (I am a storage guy) and I am struggeling a bit on some important concepts.
Basically, how do you setup a network in order for a server to be able to access many different management interfaces? I am asking, because the PC the server admin is using, is normally connected to a switch access port, right? And this port tags and untags frames only to one VLAN ID at the time.
They obviously want to be able to connect to many different management interfaces from their PC. Do you connect the management devices to a common native VLAN (eg. VLAN 10) that also the server admin is connected to? Or do we connect the serveradmin PC to a trunk port?? (Sorry for my low knowledge in switching, but I am working very hard to overcome this limitation).
Basically, how do you setup this so a server admin can access many different VLANS from his PC?
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2012 06:14 PM
Atle Dale wrote:
"For devices which have out-of-band management (like, for example, SAN controllers), I normally connect their management port(s) to the same VLAN - and assign that VLAN a seperate IP subnet. This is done, on Cisco switches, using the concept of "switched virtual interfaces", or SVI's. "
Well, I do - the "management" interfaces of my setup are on different subnets (and associated SVI's) than the "data" subnets - I just have them in a different VLAN/SVI combination to isolate the functions. You ONLY need an SVI if you want to access the management VLAn from a node lcoated *outside* that VLAN. remember, a VLAN is logically isolated from other VLAN's - so if you need to communicate between a node in VLAN 10 and a node in VLAN20, you need to allow an upper layer protocol (in this case, IP) to do the communicating - which means you need the SVI *OR* some other form of router (an SVI is not the only way to route between VLAN's - it's just the easiest on a layer-3 switch). If you're comnmunicating to nodes *purely* within the one VLAN, then you just need to let the IP stack do its job - since everything will be in the same subnet, it doesn't need a router to communicate with other nodes.
Can you provide an example of the config in the router that routes from one vlan to another for a given SVI (gateway)?
With a layer 3 switch, you don't need a router - the layer 3 functionality of the switch will do it for you. provided the SVI's are configured on the same layer-3 switch (which is a router), then switch/router will allow them to communicate.
From my switch again, I have the following defined
vlan 10
name MANAGEMENT
!
vlan 20
name DC_Servers
!
interface Vlan10
description Management subnet Address
ip address 10.100.2.254 255.255.255.0
!
interface Vlan20
description Data interfaces for servers in DC
ip address 10.100.1.254 255.255.255.0
!
And, if I look at the rout table on this switch, I see the following
core#sh ip route
[...]
C 10.100.2.0/24 is directly connected, Vlan10
C 10.100.1.0/24 is directly connected, Vlan20
There are, of course, other routes for other subnets/destinations - this is an edited list.
You can see from this that the switch's routing process knows about both networks - so any packet from a host in the 10.100.1.0/24 subnet - say, 10.100.1.101, one of my Windows domain controlers - configured with a default gateway of 10.100.1.254 - which they have - going to a node in the 10.100.2.0/24 subnet will hit the switch's routing process, and the switch will say "Hmmm, this subnet is on VLAN10, I need to send it to ports on that VLAN".
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2012 05:33 AM
ok, for windows servers, then, we will have to configure routing from one vlan to another, correct? But what about native vlans? Is there not a way to utilize these for management?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2012 05:53 PM
Atle Dale wrote:
I am fairly new to networking (I am a storage guy) and I am struggeling a bit on some important concepts.
Basically, how do you setup a network in order for a server to be able to access many different management interfaces? I am asking, because the PC the server admin is using, is normally connected to a switch access port, right? And this port tags and untags frames only to one VLAN ID at the time.
They obviously want to be able to connect to many different management interfaces from their PC. Do you connect the management devices to a common native VLAN (eg. VLAN 10) that also the server admin is connected to? Or do we connect the serveradmin PC to a trunk port?? (Sorry for my low knowledge in switching, but I am working very hard to overcome this limitation).
Basically, how do you setup this so a server admin can access many different VLANS from his PC?
You don't.
VLAN's are a pure layer 2 concept. Your PC (unless the NIC supports VLAN tagging/trunking) is in one VLAN, which connects to your switch in one VLAN.
The kind of management you're talking about is done via IP at layer 3 - layer 3 doesn't really care about layer 2.
Just ignore the VLAN's thing - if you can PING from one IP address to the destination IP address, then your management will work.
For devices which have out-of-band management (like, for example, SAN controllers), I normally connect their management port(s) to the same VLAN - and assign that VLAN a seperate IP subnet. This is done, on Cisco switches, using the concept of "switched virtual interfaces", or SVI's. These are virtual layer 3 interfaces which are *associated* with a given layer 2 VLAN - the numbers are the same, but the descriptions are different.
Here's a (trimmed) example from my core switch
core#sh run
Building configuration...
Current configuration : 15774 bytes
[...]
!
vlan 10
name MANAGEMENT
!
interface Vlan10
description Management subnet Address
ip address 10.100.2.254 255.255.255.0
!
Now - the first entry - vlan 10 - sets up the layer 2 VLAN used for frame tagging on trunk links, and to assign a given physical interface into that VLAN.
The second entry sets up the SVI - or layer 3 interface - which enables the IP conenctivity.
This is the configuration of a port that I have the management interface of one of my EMC SAN SP's which are the storage for my Cisco UCS plugged into
core#sh run int g1/0/23
Building configuration...
Current configuration : 205 bytes
!
interface GigabitEthernet1/0/23
description ## EMC SAN, SPA Management port
switchport access vlan 10
switchport mode access
spanning-tree portfast
spanning-tree bpdufilter enable
spanning-tree bpduguard enable
end
This SP has the following IP address/netmask configured on it
10.100.2.55/255.255.255.0
and has the default router of 10.100.2.254. I can access the web interface of this SP for management from any workstation in my network - because the routing for this layer 3 network is in my network core, and all my local switches/routers know how to get to it. Other devices are configured the same - the port the management interface is connected to is in VLAN 10, and the IP address on the device is in the /24 assigned to this management subnet.
Hope this helps!
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2012 12:52 AM
Hi Darren,
Thank you so much for your explenation. It really cleared up this foggy area for me.
Regarding:
"For devices which have out-of-band management (like, for example, SAN controllers), I normally connect their management port(s) to the same VLAN - and assign that VLAN a seperate IP subnet. This is done, on Cisco switches, using the concept of "switched virtual interfaces", or SVI's. "
-Here I thought you meant to put the management server and the out-of-band management on different subnets, but in your example you don't. So you don't really need the SVI (gateway pointing to a router/L3 switch) in your example? Only when the interfaces are on different VLANs and subnets?
Can you provide an example of the config in the router that routes from one vlan to another for a given SVI (gateway)?
Message was edited by: Atle Dale
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2012 06:14 PM
Atle Dale wrote:
"For devices which have out-of-band management (like, for example, SAN controllers), I normally connect their management port(s) to the same VLAN - and assign that VLAN a seperate IP subnet. This is done, on Cisco switches, using the concept of "switched virtual interfaces", or SVI's. "
Well, I do - the "management" interfaces of my setup are on different subnets (and associated SVI's) than the "data" subnets - I just have them in a different VLAN/SVI combination to isolate the functions. You ONLY need an SVI if you want to access the management VLAn from a node lcoated *outside* that VLAN. remember, a VLAN is logically isolated from other VLAN's - so if you need to communicate between a node in VLAN 10 and a node in VLAN20, you need to allow an upper layer protocol (in this case, IP) to do the communicating - which means you need the SVI *OR* some other form of router (an SVI is not the only way to route between VLAN's - it's just the easiest on a layer-3 switch). If you're comnmunicating to nodes *purely* within the one VLAN, then you just need to let the IP stack do its job - since everything will be in the same subnet, it doesn't need a router to communicate with other nodes.
Can you provide an example of the config in the router that routes from one vlan to another for a given SVI (gateway)?
With a layer 3 switch, you don't need a router - the layer 3 functionality of the switch will do it for you. provided the SVI's are configured on the same layer-3 switch (which is a router), then switch/router will allow them to communicate.
From my switch again, I have the following defined
vlan 10
name MANAGEMENT
!
vlan 20
name DC_Servers
!
interface Vlan10
description Management subnet Address
ip address 10.100.2.254 255.255.255.0
!
interface Vlan20
description Data interfaces for servers in DC
ip address 10.100.1.254 255.255.255.0
!
And, if I look at the rout table on this switch, I see the following
core#sh ip route
[...]
C 10.100.2.0/24 is directly connected, Vlan10
C 10.100.1.0/24 is directly connected, Vlan20
There are, of course, other routes for other subnets/destinations - this is an edited list.
You can see from this that the switch's routing process knows about both networks - so any packet from a host in the 10.100.1.0/24 subnet - say, 10.100.1.101, one of my Windows domain controlers - configured with a default gateway of 10.100.1.254 - which they have - going to a node in the 10.100.2.0/24 subnet will hit the switch's routing process, and the switch will say "Hmmm, this subnet is on VLAN10, I need to send it to ports on that VLAN".
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2012 11:16 PM
Thanks, Darren. It is crystal clear now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 01:22 AM
OK. What about if I have 2 links on the same VLAN? I assume I only need one SVI that applies for all the links? In my case I will have 2 x 10 Gbps links to a iSCSI host (not management). Just making sure here...
For the management of this storage box, I would assume normal practice is to use a dedicated switchport for management. But I have seen other ways to do it. Like trunking the required vlans to the storage box. Right?
But then how do I setup the SVIs for a trunk? Does anything changing apart from making the switchport a trunk port with the allowed VLANS? I just have to provide SVIs for the different VLANS in the trunk, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 01:51 AM
Hi Atle,
Layer 3 switch will do the routing between diff vlans.
See this example:
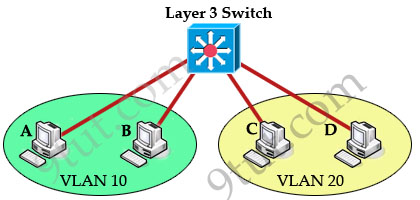
Switch configuration:
ip routing
!
interface FastEthernet0/1
switchport access vlan 10
switchport mode access
!
interface FastEthernet0/2
switchport access vlan 20
switchport mode access
interface Vlan10
ip address 192.168.10.1 255.255.255.0
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
And on hosts just assign IP addresses and default gateways (to the corresponding interface VLANs) -> hosts in different VLANs can communicate.
If you are using Router and a layer 2 switch :

To help you understand more clearly about InterVLAN, the main configuration of router & switch are shown below:
Configure trunk port on switch:
Switch(config)#interface f0/0
Switch(config-if)#no shutdown
Switch(config-if)#switchport mode trunk
Create sub-interfaces, set 802.1Q trunking protocol and ip address on each sub-interface
Router(config)#interface f0/0
Router(config-if)#no shutdown
(Note: The main interface f0/0 doesn’t need an IP address but it must be turned on)
Router(config)#interface f0/0.0
Router(config-subif)#encapsulation dot1q 10
Router(config-subif)#ip address 192.168.1.1 255.255.255.0
Router(config-subif)#interface f0/0.1
Router(config-subif)#encapsulation dot1q 20
Router(config-subif)#ip address 192.168.2.1 255.255.255.0
(Note: In the “encapsulation dot1q 10″ command, 10 is the VLAN ID this interface operates in)
I also list the full configuration of the above topology for your reference:
Configure VLAN
Switch(config)#vlan 10
Switch(config-vlan)#name SALES
Switch(config-vlan)#vlan 20
Switch(config-vlan)#name TECH
Set ports to access mode & assign ports to VLAN
Switch(config)#interface range fa0/1-2
Switch(config-if)#no shutdown
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 10
Switch(config-if)#interface range fa0/3-4
Switch(config-if)#no shutdown
Switch(config-if)#switchport mode access
Switch(config-if)# switchport access vlan 20
Hope this helps.
Regards
Please rate if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:01 AM
Thanks. So I deduce that obviously I only need to define on SVI per VLAN? All hosts in that VLAN will use the same specific gateway to that VLAN. No need to define gateways for each access port?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:04 AM
Hi Alte,
yes your are right ....every vlan have their own default-gateway,so just assign the gateway according to vlan.All routing will be done by layer 3 switch.
Regards
Please rate if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:09 AM
ok, back to my question on trunks. Please read it again. What I meant was if anything would change regarding SVI Layer-3 routing if we configured a trunk port for the cable going from a storage processor to the switch. Let's say this cable transmits a iSCSI Vlan and a mangement VLAN. Would anything change apart from configuring the port as a trunk port? Please ask me if you don't understand what I mean.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:17 AM
There is only way to configure the port as a trunk.
SP have 2 nic or what????
why do you need to transmit 2 vlan from SP.This work will be done by layer 3 switch.
if you hav layer2 switch between then
sp-----layer 2-----------------------Layer3-----then other device then you have to configure the trunking beteen layer 2 and layer3.
or you wanna ask something else??
Regards
Please rate if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:25 AM
No, as I said, the SP often has its own management interface. Then no need to configure a trunk if just iSCSI traffic is going on the link.
So I mean if this is not possible for a reason, we have to transmit 2 or maybe more VLANS through the same cable. My questions are:
1. For a Layer 3 switch, will anything change regarding the SCI config? I assume not. All the VLANS will have their SVI regarrless if th etraffic is coming from a trunk line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:34 AM
Yes, no need to change on the layer 3 switch ......layer 3 does ip routing.
it doesnt matter ..how many vlans traffic you are transmiiting from SP.....all routing done by layer 3 switch.
Regards
Please rate if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2012 02:36 AM
ok, thank you.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide