- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: P2P Connection Between Switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
P2P Connection Between Switch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 06:45 AM - edited 03-08-2019 01:56 PM
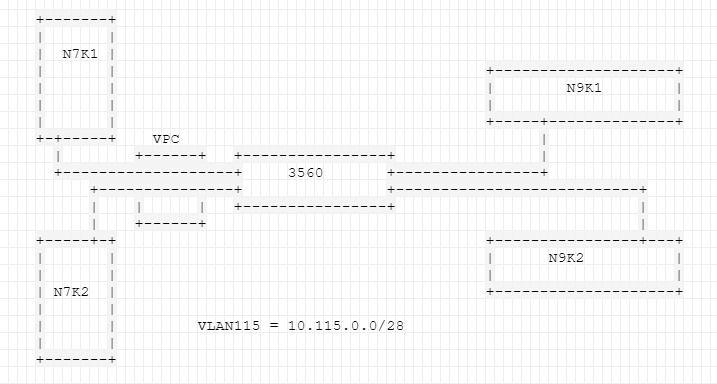
I am trying to create a point to point layout between 2 sets of Nexus equipment. Normally you connect the connection directly into the device, but where this comes in it will connect to a switch on both ends for distribution and then connect to the core. I was trying to configure this using VLAN 115 and keeping the devices on their own but I can not get them to see or ping one another. I have VLAN 115 configured with the IPADDR. How can I keep the point to point configuration through L2?
N7K1
interface Vlan115
description * P2P DC1 to DC2 *
no ip redirects
ip address 10.115.0.2/28
hsrp 1
preempt delay minimum 300 reload 600
timers msec 250 msec 750
ip 10.115.0.1
N7K2
interface Vlan115
description * P2P DC1 to DC2 *
no ip redirects
ip address 10.115.0.3/28
hsrp 1
preempt delay minimum 300 reload 600
timers msec 250 msec 750
ip 10.115.0.1
N9K1
interface Vlan115
description * P2P DC1 to DC2 *
no ip redirects
ip address 10.115.0.13/28
hsrp 1
preempt delay minimum 300 reload 600
timers msec 250 msec 750
ip 10.115.0.14
N9K2
interface Vlan115
description * P2P DC1 to DC2 *
no ip redirects
ip address 10.115.0.12/28
hsrp 1
preempt delay minimum 300 reload 600
timers msec 250 msec 750
ip 10.115.0.14
3560
switchport mode trunk
switchport trunk allowed vlan add 115
switchport nonego
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 07:05 AM
Where are the user/server vlans terminated? Are they on the 9ks, if yes, then you need layer-3 links between the 9ks and the 7ks (one /30 between n9k-1 and n7k-1 and one between n9k-2 and n7k-2).
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 11:02 AM
I have clients and servers on bother sides. This will be for an existing network to connect the 2 networks together. Each side has their own networks and servers. I would like to connect them with fiber instead of using VPN which is currently used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 12:32 PM
Ok, in that case as I noted before you can simply use /30 or /29 for each link. So, you would need 2 SVIs with 2 vlans (one per link) on the 9k, 7k and same vlans trunked to the switch in the middle (layer-2 only).
You can run OSPF for all connections.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 07:05 AM
Thats a single point of failure with the 3560 in the center like that , with those switches you should think about a real vpc design for full resiliency liek below screenshot or at least use a stack of 3560s even 2
If its vpc to the 3560 from both the 7k and 9ks then the vpc needs to be created on the 7k and 9k side and then standard PO on the 3560 side and each needs to allow vlan 15 through , is that done with vpc domain ? that should allow reachability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 11:08 AM
I understand this is a single point of failure for both ends. We are only paying for 1 connection that will need to be terminated in the DMARC. Even if I was able to get the fiber up to the top of the building where the server room resides. It would only be connected to one of the Nexus. When system maintenance occurs on that unit the connection will be lost.
I am trying to get this connection to work as a P2P to route traffic a crossed.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide