- Cisco Community
- Technology and Support
- Networking
- Switching
- Portfast port and bpduguard purpose confusion
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 06:49 AM
read Cisco Doc always come across Portfast port should connect only end points as they transist to fwd w/o listen/learning stage.
how ever, i also read that if a portfast port receive bpdu, it will still goes into blk stage (stp still working).
In this case, then wat is the purpose of enable bpduguard to err-disable the port when receive bpdu??????
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 07:24 AM
Hi Charlie,
The problem with PortFast is that the port becomes Forwarding without verifying if it is safe to do so. Till the BPDUs arrive, the resulting traffic flooding in the switching loop may be so intense that the CPU on the switches won't be able to process BPDUs anymore.
If you think about it, neither the natural PortFast behavior (stop treating the port as an edge port and instead handle it as a regular non-edge port) nor the BPDU Guard (err-disable the port) provide perfect protection exactly because till they realize something's wrong, it may be too late to take action; the CPU on the switches may be swamped. Both PortFast and BPDU Guard are purely software-based mechanisms, implemented in the IOS/IOS-XE running on the switch, and so if the CPU is choking, neither of them has a better chance of saving the situation.
The existence of the PortFast behavior and BPDU Guard just allows you to pick your poison if an edge port (a port where PortFast is enabled) receives a BPDU because it is clearly not an edge port, then:
- You can either forget that the port was considered as an edge port, and start using it as a regular non-edge port. That is what the default PortFast does.
- ... or you can disable the port because there should never have been anything connected to it that sends out BPDUs anyway. That is what BPDU Guard does.
Please feel welcome to ask further!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 07:24 AM
Hi Charlie,
The problem with PortFast is that the port becomes Forwarding without verifying if it is safe to do so. Till the BPDUs arrive, the resulting traffic flooding in the switching loop may be so intense that the CPU on the switches won't be able to process BPDUs anymore.
If you think about it, neither the natural PortFast behavior (stop treating the port as an edge port and instead handle it as a regular non-edge port) nor the BPDU Guard (err-disable the port) provide perfect protection exactly because till they realize something's wrong, it may be too late to take action; the CPU on the switches may be swamped. Both PortFast and BPDU Guard are purely software-based mechanisms, implemented in the IOS/IOS-XE running on the switch, and so if the CPU is choking, neither of them has a better chance of saving the situation.
The existence of the PortFast behavior and BPDU Guard just allows you to pick your poison if an edge port (a port where PortFast is enabled) receives a BPDU because it is clearly not an edge port, then:
- You can either forget that the port was considered as an edge port, and start using it as a regular non-edge port. That is what the default PortFast does.
- ... or you can disable the port because there should never have been anything connected to it that sends out BPDUs anyway. That is what BPDU Guard does.
Please feel welcome to ask further!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 09:06 AM
In addition to Peter's usual excellent information, you might use BPDUGuard, to disable the port, as a very strong signal that a BPDU, on that port, is unexpected! A PortFast only port, especially if there's not a L2 loop, will continue to function "normally" and the issue of BPDU being seen, where unexpected, might go unnoticed.
BTW, even on non-PortFast enabled ports, it's still possible for L2 loop to be connected, so even with STP and BPDUGuard L2 loops are still a possible risk. This is one of the reasons, there are recommendation for using more L3 LAN topology to "shrink" L2 LAN topology.
If you're wondering how to negate STP, consider having (non STP switch)<>(STP switch)<>(non STP switch), interconnect the two non STP switches.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 07:42 AM - edited 06-26-2021 09:17 AM
Friend the Portfast behavior is different if you config it
global Mode
interface Mode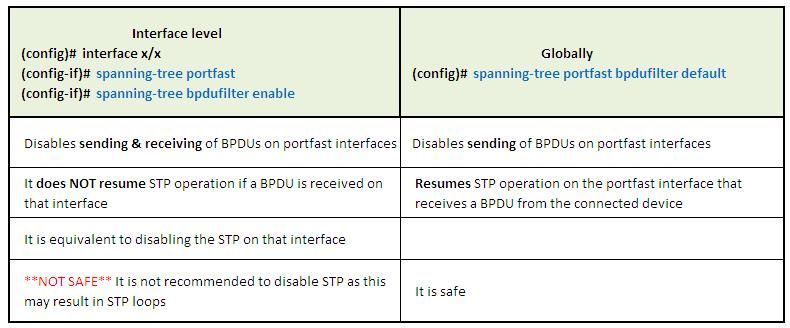
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 09:02 AM - edited 06-26-2021 09:08 AM
i am confused why the need for bpduguard since portfast port can by itself go into stp blk (to disable any loop) when it receive bpdu hence no need to configure bpduguard.
i do not understand why u bring bpdufilter feature into this as it is completely a different feature to ignore/not to send configuration bpdu on ports.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 09:29 AM
Yes friend it confuse because we deal with regular SW but
L2 Loop can happened without connect to SW!!
Yes this can via VM server.
VM Server connect to two different SW through the Access Port,
VM Server may forward BPDU from one SW to other, this is make loop.
how we can solve this
BPDUguard with Portfast and this make SW2 when receive BPDU from port connect to VM Server go to err-disbale instead of go to STP forward, because of if it go to STP forward then it may be SW2 elect this port as root port and send all traffic to SW1 and loop happen, so in this case the only solution is make admin solve this err-disable after check the VM Server connect.
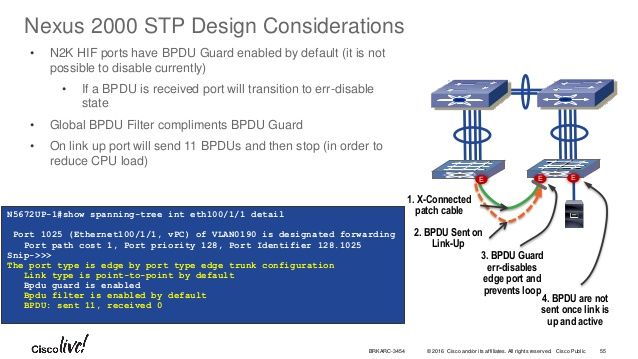
BPDUguard is enable by default in N2K
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2021 10:17 AM
I would say use BPDU guard instead of BPDU filter. As @Peter Paluch correctly points out, you should never see a BPDU on a port with portfast enabled. It SHOULD go into blocking after the listening and learning time expires, but I have seen cases where it did not. The key thing about this is with portfast enable, you can have a loop while frames are forwarding before listening and learning are finished. The general idea as I understand it is that it is better to shut down a port that is misbehaving to preserve the rest of the network. I consider "spanning-tree portfast bpduguard default" to be a mandatory thing in global config for edge switches.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide