- Cisco Community
- Technology and Support
- Collaboration
- Unified Communications Infrastructure
- Cisco CUCM 12.5 TVS Certificate template
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco CUCM 12.5 TVS Certificate template
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2021 06:08 PM - edited 05-23-2021 06:09 PM
According to the following link:
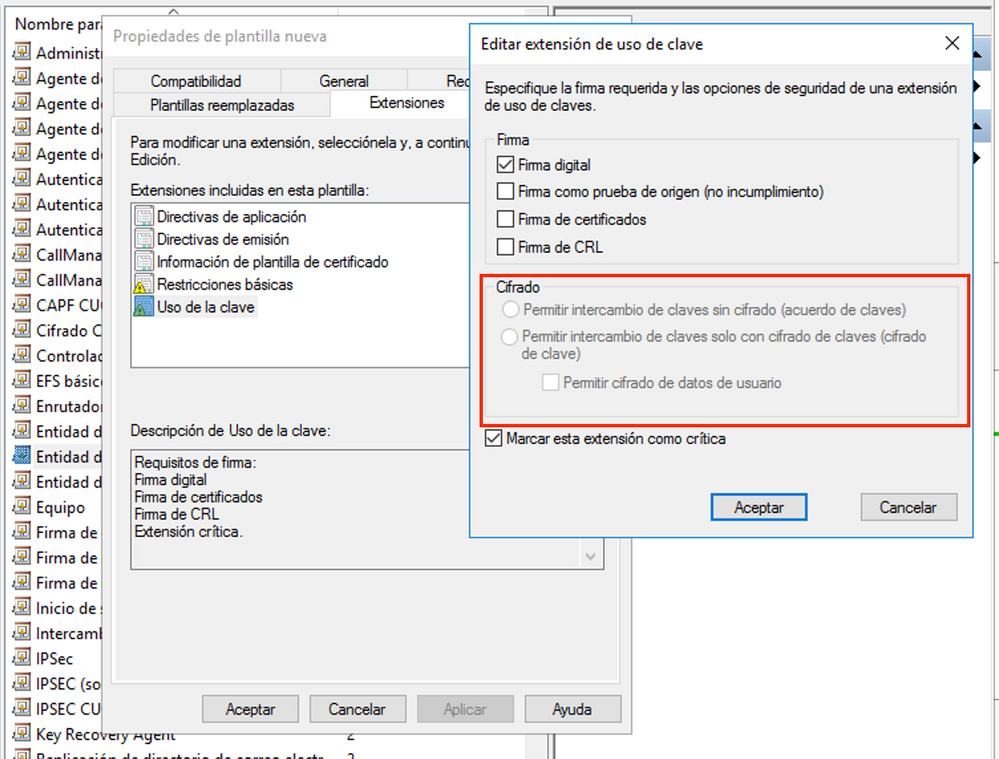
The TVS certificate requires the check
- Allow key exchange only with key encryption (key encipherment)
- Allow encryption of user data
The problem is that those checks appears blocked or grayed out. Will it be fine if we don't check or is there a problem with the template, or the document got an error? Microsoft server 2016 is being used to sign the certificate
Thanks for your help
- Labels:
-
Call Control
-
Unified Communications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2021 10:58 PM
No idea what the screenshot says as it seems to be in Spanish. If I where to venture into a guess I would say that it’s the configuration or setup of the CA that is restricting these settings to be shown. However I’m by far no expert in Microsoft CA setup.
AFAIK these settings are imperative for the functionality, so if you where to use CA signed certificate for TVS these have to be set as per the document. If you cannot set them you’ll be better off to use self signed certificate for TVS.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2021 07:33 AM - edited 05-24-2021 07:33 AM
Actually I just want to sign the necessary certificates for MRA, Jabber and SIP trunks and not all the ones listed in the document.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2021 11:19 PM - edited 05-23-2021 11:20 PM
The guide you shared is asking to duplicate the Root Certification Authority template.Did you followed below step or you choose different template ? Looks like the template issue.
TVS Template
Step 1. Find the Root Certification Authority template and right-click on it. Then select Duplicate Template, as shown in the image.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2021 07:13 AM
Hi folks.
The server is in Spanish, but the options are the same, all the templates have been created except for the TVS certificate, in fact all the steps have been followed correctly. Is it possible then to use the self signed TVS certificate then?
Thanks for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2021 08:14 AM - edited 05-24-2021 08:28 AM
The CA mentioned In the document is 2012 and yours is 2016. I am not a Microsoft expert and not sure if there is any additional setting to enable it. but I think even without that option checked your MRA will work. I don’t think my server team has done that.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2021 08:21 AM
Yes you can use a mix of CA signed and self-signed certificates. For example we only use CA signed certificates where is is absolutly required to get a seamless UX for users. For more information on this have a look at this document I wrote some time ago. Cisco UC Certificates Renewal Guide

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2021 08:17 AM
The document seems to be inconsistent, images from steps 2-3 are correct when creating a copy of the root certificate authority, notice there are only TWO rows of tabs. Application Policies from root CA has none listed when you copy the template. Notice 3 has certificate signing and CRL signing selected.
Steps 4-5 however, have THREE rows of tabs, adding to that, that the Application Policies in the document show that Server Authentication is already listed, means that those screenshots are from Web Server template, which would enable you to choose the options from step 4. But the options that were show on 3 as already selected are now grayed out.
Whoever wrote this mixed two certificate templates in the same procedure.
Looking at the self-signed from my lab, it's even missing Enhanced Key Usage:
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
IP security end system (1.3.6.1.5.5.7.3.5)
It never mentions to add IP security end system.
It does have certificate signing under Key Usage: Digital Signature, Key Encipherment, Data Encipherment, Key Agreement, Certificate Signing (bc)
and AFAIK, only root CA or subordinate CA templates allow you to choose certificate signing.
Already sent feedback with the link in the doc, suggest you do the same and explain TVS procedure mixes templates and is wrong so it's corrected.
java
if this helps, please rate
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide