- Cisco Community
- Technology and Support
- Collaboration
- Unified Communications Infrastructure
- Expressway Weak SSL/TLS Key Exchange Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Expressway Weak SSL/TLS Key Exchange Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2022 09:10 PM - edited 06-07-2022 09:12 PM
Hi Team,
Recently I got a report from my security team, stating that there is Weak SSL/TLS Key Exchange on our expressway deployment. The report is generated from Qualys. The result said this:
PROTOCOL NAME GROUP KEY-SIZE FORWARD-SECRET CLASSICAL-STRENGTH QUANTUM-STRENGTH
TLSv1.2 ECDHE secp192r1 192 yes 96 low
On the solution tab of the report, it is stated that:
Change the SSL/TLS server configuration to only allow strong key exchanges.
On Maintenance -> Security -> Ciphers, here are the entry on the ciphers:
EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL
Here are the output when I issue xconfiguration // ciphers command:
xconfiguration // ciphers
*c xConfiguration Ciphers ForwardProxyTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL"
*c xConfiguration Ciphers ForwardProxyTLSProtocol Value: "minTLSv1.2"
*c xConfiguration Ciphers HTTPSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL"
*c xConfiguration Ciphers HTTPSProtocol Value: "minTLSv1.2"
*c xConfiguration Ciphers RemoteSyslog1TLSCiphers Value: "ALL"
*c xConfiguration Ciphers RemoteSyslog1TLSProtocol Value: "minTLSv1.0"
*c xConfiguration Ciphers RemoteSyslog2TLSCiphers Value: "ALL"
*c xConfiguration Ciphers RemoteSyslog2TLSProtocol Value: "minTLSv1.0"
*c xConfiguration Ciphers RemoteSyslog3TLSCiphers Value: "ALL"
*c xConfiguration Ciphers RemoteSyslog3TLSProtocol Value: "minTLSv1.0"
*c xConfiguration Ciphers RemoteSyslog4TLSCiphers Value: "ALL"
*c xConfiguration Ciphers RemoteSyslog4TLSProtocol Value: "minTLSv1.0"
*c xConfiguration Ciphers ReverseProxyTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL"
*c xConfiguration Ciphers ReverseProxyTLSProtocol Value: "minTLSv1.2"
*c xConfiguration Ciphers SIPTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:+ADH"
*c xConfiguration Ciphers UcClientTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL"
*c xConfiguration Ciphers UcClientTLSProtocol Value: "minTLSv1.2"
*c xConfiguration Ciphers XCPTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL"
*c xConfiguration Ciphers XCPTLSProtocol Value: "minTLSv1.2"
*c xConfiguration Ciphers sshd_ciphers Value: "aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr,aes256-cbc,aes192-cbc,aes128-cbc"
*c xConfiguration Ciphers sshd_kex Value: "ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1"
*c xConfiguration Ciphers sshd_macs Value: "hmac-sha2-512,hmac-sha2-256,hmac-sha1"
*c xConfiguration Ciphers sshd_pfwd_ciphers Value: "aes256-ctr"
*c xConfiguration Ciphers sshd_pfwd_kexalgorithms Value: "ecdh-sha2-nistp384"
*c xConfiguration Ciphers sshd_pfwd_pubkeyalgorithms Value: "x509v3-sign-rsa"
*c xConfiguration Authentication ADS CipherSuite: "HIGH:MEDIUM:!ADH:!aNULL:!eNULL:-AES128-SHA256:@STRENGTH"
I am running 12.5.4 on the expressway. May I know how to resolve it? Thank you.
- Labels:
-
Unified Communications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2022 10:32 PM
Not as such direct related to your question at hand, but I would strongly recommend you to upgrade your Expressways to 14.0.6 or even better 14.0.7 as there are a number of serious security defects that won’t be fixed in any other releases. Besides that the version that you are using is getting quite old at this point.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2022 01:14 AM
Hi Roger,
Thank you for the reply. Let me arrange an upgrade of the expressway and see how it goes. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2022 01:42 AM - edited 06-08-2022 01:42 AM
FYI these are the settings that we have for ciphers on one of our Expw that is running 14.0.7.
From what I know we have not altered these, they all should be at their default.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2022 01:46 AM
Same output from xconfig.
xconfiguration // ciphers *c xConfiguration Ciphers HTTPSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers HTTPSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers LDAPTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers LDAPTLSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers RemoteSyslog1TLSCiphers Value: "ALL:!aDH" *c xConfiguration Ciphers RemoteSyslog1TLSProtocol Value: "minTLSv1.0" *c xConfiguration Ciphers RemoteSyslog2TLSCiphers Value: "ALL:!aDH" *c xConfiguration Ciphers RemoteSyslog2TLSProtocol Value: "minTLSv1.0" *c xConfiguration Ciphers RemoteSyslog3TLSCiphers Value: "ALL:!aDH" *c xConfiguration Ciphers RemoteSyslog3TLSProtocol Value: "minTLSv1.0" *c xConfiguration Ciphers RemoteSyslog4TLSCiphers Value: "ALL:!aDH" *c xConfiguration Ciphers RemoteSyslog4TLSProtocol Value: "minTLSv1.0" *c xConfiguration Ciphers ReverseProxyTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers ReverseProxyTLSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers SIPTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:+ADH" *c xConfiguration Ciphers SMTPTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers SMTPTLSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers TMSProvisioningTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers TMSProvisioningTLSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers UcClientTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers UcClientTLSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers XCPTLSCiphers Value: "EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH" *c xConfiguration Ciphers XCPTLSProtocol Value: "minTLSv1.2" *c xConfiguration Ciphers sshd_ciphers Value: "aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr" *c xConfiguration Ciphers sshd_kex Value: "ecdh-sha2-nistp256,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1" *c xConfiguration Ciphers sshd_macs Value: "hmac-sha2-512,hmac-sha2-256,hmac-sha1" *c xConfiguration Ciphers sshd_pfwd_ciphers Value: "aes256-ctr" *c xConfiguration Ciphers sshd_pfwd_kexalgorithms Value: "ecdh-sha2-nistp384" *c xConfiguration Ciphers sshd_pfwd_pubkeyalgorithms Value: "x509v3-sign-rsa" *c xConfiguration Authentication ADS CipherSuite: "HIGH:MEDIUM:!ADH:!aNULL:!eNULL:-AES128-SHA256:@STRENGTH" OK

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 04:21 AM
To mitigate this, We have to manually change the SIP TLS Diffie-Hellman key size from the default 1024 bits, to at least 2048.
You can also refer below guide for the same at page 68 (Point 8):
For this you can login to CLI of concerned node as admin & run the command: “xconfiguration SIP Advanced SipTlsDhKeySize: 2048”
You can also refer below guide for the same at page 71
https://www.cisco.com/c/dam/en/us/td/docs/voice_ip_comm/expressway/admin_guide/Cisco-Expressway-Administrator-Guide-X12-6.pdf
For this you can login to CLI of concerned node as admin & run the command: xconfiguration SIP Advanced SipTlsDhKeySize: 2048
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2022 07:29 AM
Hi Vinod,
Thank you for your reply. I tried to apply it, but somehow still got detected by the system. Even though the DH key is now 2048.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 08:52 AM
Update:
I found that secp192r1 is actually not a cipher, it is a key exchange.
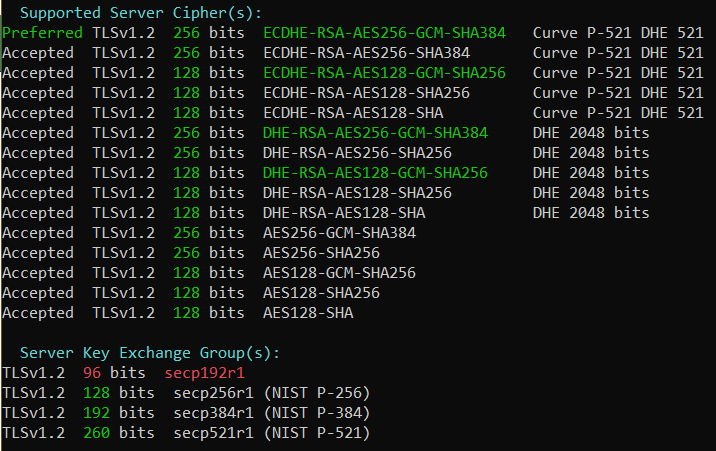
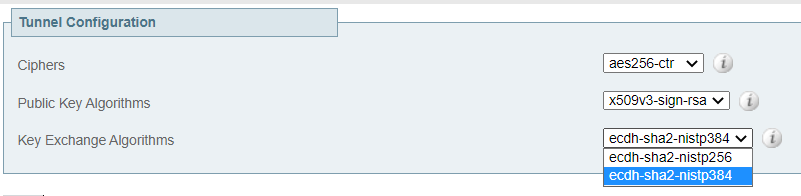
xConfiguration Ciphers sshd_kex Value: "ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1"
I did not find any secp192r1. May I know how to remove it? Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2022 08:09 AM
investigating and checking with the bug owner for a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 02:57 AM
Hi,
any update on the case?
thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 03:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2022 12:28 AM
Hi Vinod,
Got any words back from TAC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2022 04:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2022 02:28 AM
Finally cisco release bug for this Vulnerability which is now publicly visible.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwb96116
Now they are internally working to provide workaround/fixed release for this bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 01:22 AM
Hi,
"Current we have the following opened defect: https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwb96116, which has been opened to address this issue but there is no workaround, so it is not possible to allow weak cypher use or make this change, and also Expressway upgrade will not solve the problem"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




