- Cisco Community
- Technology and Support
- Collaboration
- Unified Communications Infrastructure
- Re: MRA Expressway E complaining about RMS License "Out of Compli
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 01:45 AM
Hello!
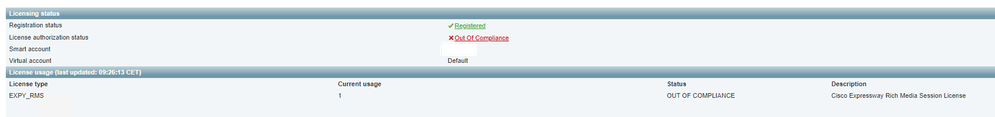
Ok. We are running an Expressway Cluster Pair that is ONLY for Mobile Remote Access.
There should not be anything going on that would require a Rich Media Session License, and yet the ExpE Nodes are complaining that they are out of compliance because of missing RMS Licenses. Its only on the Expressway Es.
Does anyone know why that is and how to prevent it.
Problem is that the Exps are now registered in a Smart Account and that will also raise an alert. Which in turn raises questions with the department responsible for managing the smart account.
Any info you be appreciated.
Thanks!
Solved! Go to Solution.
- Labels:
-
Other Unified Communications
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 02:35 AM
Now I had access to an Expressway, a re-cap:
1) Delete DNS SRV records for SIP / H.323 in the public DNS, so they are not resolved to your Expressway-Es public IP.
2) Turn off unused services: You can turn of H323 (Configuration --> Protocols --> H323), SIP/UDP (Configuration --> Protocols --> SIP --> UDP mode --> off) and SIP/TCP (Configuration --> Protocols --> SIP --> TCP mode --> off)
SIP/TLS needs to stay on for MRA!!
You can also block those protocols (H323, SIP/UDP and SIP/TCP) already on the FW infront of the EXP-E.
You can also add FW rules directly on the EXP-E under System --> Protection --> Firewall Rules
3) Add a call policy rule to block all SIP/h323 calls:
First: Activate the policy service (Configuration --> Call Policy --> Configuration --> Call policy mode --> Local CPL)
Second: Add a "block all" rule (Configuration --> Call Policy --> Rules --> New)
- Source type: From address
- Rule applies to: unauthenticated callers
- Source pattern: ".*" (without the double quotes)
- Destination pattern: ".*" (without the double quotes)
- Action: Reject
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 02:02 AM
There could be some one trying to make a B2B call which consume the RMS license. harden your expressway asper the best practices and enable the protection features on expressway.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 02:41 AM
Hello!
Thanks for your reply. Makes sense.
Any documentation on what the "best practices" are? Is there a hardening guide? I can't find anything.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 04:35 AM - edited 02-02-2023 04:37 AM
Refer admin expressway admin guide and there are some Cisco Live contents available regarding this topic.
https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2019/pdf/BRKCOL-2018.pdf

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 12:00 AM
Ok. Thank you. I will dig into that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 12:38 AM
If you have DNS SRV records for SIP / H323: delete them. You don't need them for MRA
You can also disable SIP/TCP and SIP/UDP on Exp-E. They are also not needed for MRA.
Add a policy rule that blocks everything: Source-pattern ".*" and Dest-pattern ".*" (without the double quotes).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 12:25 AM - edited 02-04-2023 12:31 AM
Hello @b.winter
I was about to post a response saying that you did a great post on this a while back where you posted a little bit more information on how to go about to set up the policy rules. Tried to find it, but got nowhere. Would you have the chance to link to it or share the information once more?
Edit: Funny enough, I did find your post and to my big surprise it was a response to the OP of this post. @JaySchiller You got this response from @b.winter back in late 2022, https://community.cisco.com/t5/unified-communications-infrastructure/mra-expressway-e-wants-to-use-rms-or-ucm-telepresenceroom/td-p/4743161, have you done the changes he suggested there?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 12:45 AM
Hello!
To be honest, I totally forgot about this post.
But, yes, I did implement the changes. And it did indeed help with the complaints about the missing Telepresence Room Licenses. Not against the missing RMS Licenses.
I would image that what @b.winter suggest might be the Answer.
"Add a policy rule that blocks everything: Source-pattern ".*" and Dest-pattern ".*" (without the double quotes)."
I did not find the time to test this yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 01:03 AM
FYI We did put in the policy back when you asked this the other time and from what we have been able to tell we have not seen any alerts for this since, nor experienced any drawbacks from it. It’s a five minutes effort, so it’s advisable to get it done so that you can get rid of these nuisance alerts.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 01:04 AM
Hi Jay,
yes, you are correct. The rule in the other post is just for registration attempts to the Expressway.
But you are now having the problem with normal SIP / H323 calls to the Expressway.
What I mean with policy rules
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/expressway/admin_guide/X14-0-2/exwy_b_cisco-expressway-administrator-guide-x1402/exwy_m_dial-plan-and-call-processing.html#reference_CEA8181662DA39369E86D65E04B51FEF section "Configuring Call Policy"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 02:35 AM
Now I had access to an Expressway, a re-cap:
1) Delete DNS SRV records for SIP / H.323 in the public DNS, so they are not resolved to your Expressway-Es public IP.
2) Turn off unused services: You can turn of H323 (Configuration --> Protocols --> H323), SIP/UDP (Configuration --> Protocols --> SIP --> UDP mode --> off) and SIP/TCP (Configuration --> Protocols --> SIP --> TCP mode --> off)
SIP/TLS needs to stay on for MRA!!
You can also block those protocols (H323, SIP/UDP and SIP/TCP) already on the FW infront of the EXP-E.
You can also add FW rules directly on the EXP-E under System --> Protection --> Firewall Rules
3) Add a call policy rule to block all SIP/h323 calls:
First: Activate the policy service (Configuration --> Call Policy --> Configuration --> Call policy mode --> Local CPL)
Second: Add a "block all" rule (Configuration --> Call Policy --> Rules --> New)
- Source type: From address
- Rule applies to: unauthenticated callers
- Source pattern: ".*" (without the double quotes)
- Destination pattern: ".*" (without the double quotes)
- Action: Reject
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 04:21 AM - edited 02-06-2023 03:09 AM
Great post @b.winter One small comment, if you have a cluster of Expressways you can not turn off H323 as that’s used by the cluster service.
Also assuming that point 3 would not be needed if there is no SRV records as outlined in point 1 and/or if these ports are not allowed through the external firewall.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 11:48 AM
Besides the suggestions made by everyone else, you may also want to make sure "Business to bussiness calls" is not running as a service on your expreway C and E servers.
From the web GUI of both expressway C and E, go to Status > Overview and click on Run service setup.
On the service setup page, uncheck the box next to "Business to bussiness calls" and click continue to save the configs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2023 11:29 PM
Thanks to all of you.
I really appreciate the help!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide