- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco AnyConnect - Same IP as LAN?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-03-2013 03:38 PM - edited 02-21-2020 07:03 PM
I am trying to see if this can be done... I know the best practice is to give VPN clients IP addresses on a different subnet than the ASA's interfaces, but in my current situation, I need them to have the same addresses as the company LAN. We have many existing client VPN's from a head office router, where changing ACL's on every tunnel to accommodate AnyConnect clients is not an option. I need to find a way that AnyConnect clients can connect to our Remote Access Firewall, but still allow traffic through existing Client VPN tunnels, without modifying the existing client VPN configurations. A diagram might explain it better (see below).
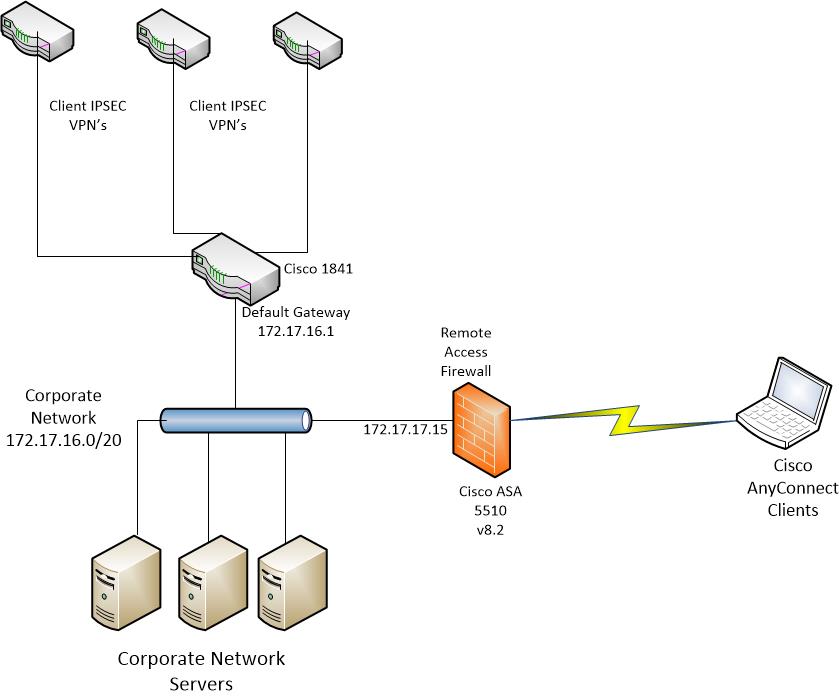
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2013 02:08 AM
Hi John
Yes, this can be done. I've done this plenty of times using AnyConnect.
You can even tell the ASA to allocate IP Addresses to AnyConnect clients using your main network DHCP server(s).
You'll need to create NAT exclusion rules on the ASA so that this traffic isn't NATd, and also add routes on the ASA for the remote subnets that you want to be able to communicate with.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2013 02:08 AM
Hi John
Yes, this can be done. I've done this plenty of times using AnyConnect.
You can even tell the ASA to allocate IP Addresses to AnyConnect clients using your main network DHCP server(s).
You'll need to create NAT exclusion rules on the ASA so that this traffic isn't NATd, and also add routes on the ASA for the remote subnets that you want to be able to communicate with.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2013 02:29 AM
Thanks Barry, you're right. I thought it would be a little more complicated than that, but indeed, it works.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide