- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco ASAv - VTI status and protocol DOWN. Where is the problem?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ASAv - VTI status and protocol DOWN. Where is the problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2017 08:40 PM - edited 03-12-2019 04:43 AM
Hi community!
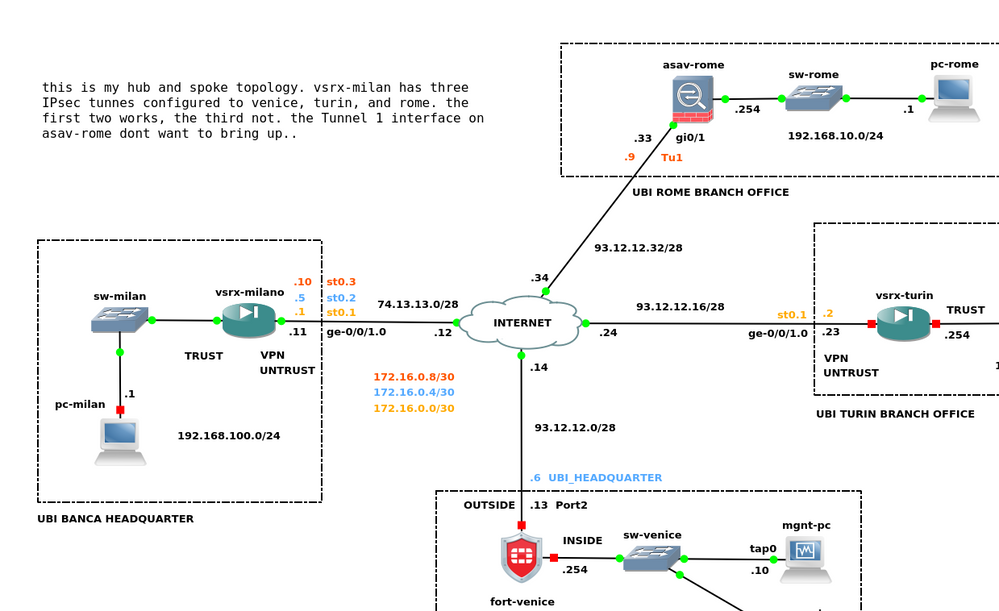
I want to configure a route-based IPsec VPN between a Juniper vSRX and a Cisco ASAv in my GNS3 LAB. the ASAv version is the 9.8(2) and I read that it supports the Virtual Interface Tunnel (VTI) feature. I created the Tunnel interface but it's both in status and protocol DOWN. Can someone help me to find the problem? I attached my ASAv's configuration. Why is the Tunnel interface DOWN? following my topology:
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2017 04:34 AM
I have a feeling that some parts are missing on your setup. How firewall are talking each other?
Take a look on this link, although the topology is two ASA this can give you a very good grasp.
https://techstat.net/cisco-asa-9-7-route-based-vpn-load-balancing-failover-setup-guide/
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 06:00 AM - edited 11-13-2017 06:16 AM
i think it's not an IPsec problem. if i create a tunnel interface on a router, his interface status goes up immediately. in my ASAv firewall instead, the tunnel interface status stays down even after i created it. it's not a good behaviour..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 06:09 AM
I didn´t ask but is it you ASA in routed mode, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 06:23 AM - edited 11-13-2017 06:23 AM
currently my ASAv firewall works in routed mode:
asav-rome# show firewall Firewall mode: Router
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 06:35 AM
Let me simulate here and I´ll let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2017 11:00 AM
I do not have much experience with VTI on the ASA but do have lots of experience with it on IOS routers. I assume the implementation on ASA is similar to IOS router. The behavior of VTI on router is quite different from the behavior of GRE. My experience, like yours, is that when you configure a GRE tunnel that it immediately comes to the up/up state (if there is a viable route toward the tunnel destination in the routing table). But VTI does not behave that way. On routers the status of VTI depends on the negotiation of the crypto relationship. Until there is a successful negotiation of SA between peers the VTI will not be up/up. So I would take a closer look at the crypto config as a possible source of the VTI down status.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 07:06 AM - edited 11-14-2017 07:21 AM
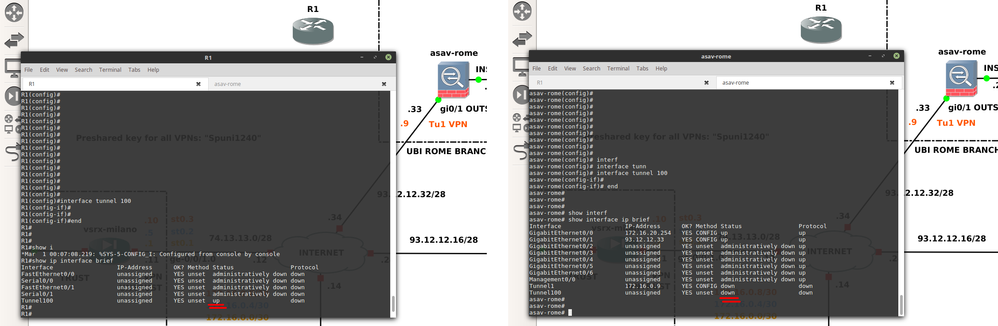
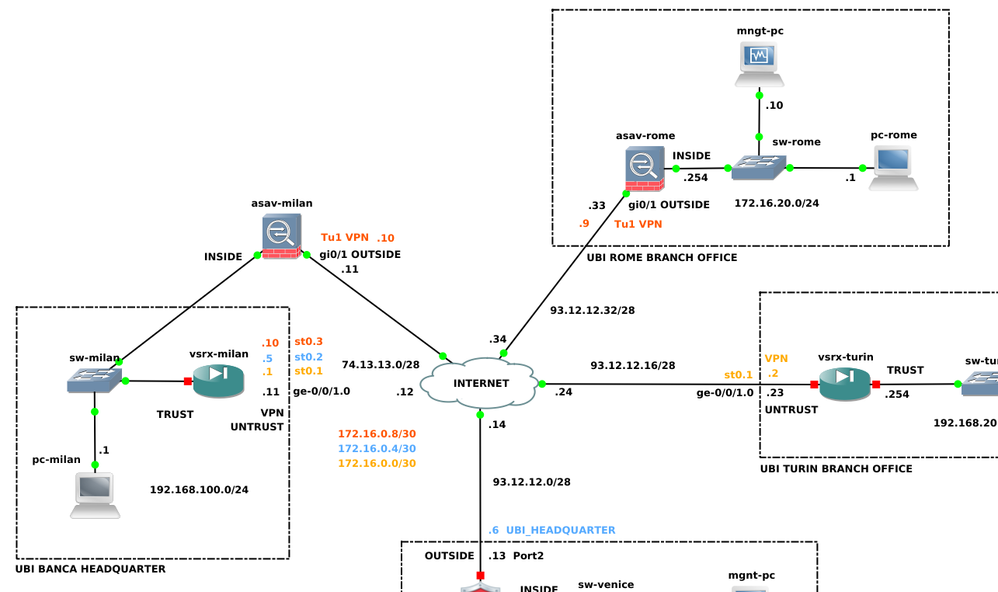
I changed a little bit my topology. I replaced my vsrx-milan with an ASAv firewall. currently my main goal is to see the IPsec tunnel works between the two ASA firewalls. I configured both, but the VTI interface is still in down state:
for me it's very difficult troubleshooting an IPsec tunnel between two interfaces in DOWN state. I attached the configurations. let me know if I have done sometimes wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 01:18 PM
I have looked at the configs that you posted and have these comments:
- both ASAv have nat that does a dynamic translation on any traffic from inside to outside. I would think you would want to configure so that VPN traffic is not translated.
- - both ASAv have an object configured for an inside network of 192.168.10.0 and use that network in the inside_in ACL. But there is no other mention of that network on either ASAv.
- Milan configuration includes a crypto map. One of the features of VTI is that you do not need a crypto map. I suggest that you remove this crypto map.
- one of the common causes of problems in bringing up ccrypto tunnels is that the shared key for authentication does not match. I suggest that you re-configure this and do it very carefully.
After you attempt to bring up the tunnel (from Milan attempt to ping something in 172.16.20.0 or from rome attempt to ping something in 192.168.100.0) then immediately use show crypto commands to look for ISAKMP and/or IPsec SAs. If there are none (and I suspect that there will not be) then turn on debug for ISAKMP, do the ping again, and post any debug output.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 02:30 PM - edited 11-15-2017 12:38 AM
- both ASAv have nat that does a dynamic translation on any traffic from inside to outside. I would think you would want to configure so that VPN traffic is not translated.
that NAT policy allows the internet traffic from inside to outside, but for the IPsec VPN it's not a problem, because the VPN traffic flows from inside to vpn and not from inside to outside. in fact the Tu1 interface has been configured with the "nameif vpn" command.
- - both ASAv have an object configured for an inside network of 192.168.10.0 and use that network in the inside_in ACL. But there is no other mention of that network on either ASAv.
that object-group it's not used in my configuration. it's a refusal of an old configuration. but the ACL is wrong, right! i changed it to allow the 192.168.100.0/24 (in asav-milan) and 172.16.20.0/24 (in asav-rome) to the internet, from inside to outside. now the internet traffic works, before it didn't work.
- Milan configuration includes a crypto map. One of the features of VTI is that you do not need a crypto map. I suggest that you remove this crypto map.
you are right! at the start with my configuration I tried to configure a crypto map, but then I read that it's not used in a route-based IPsec VPN with VTI interfaces. in this configuration we must use the crypto ipsec profile. I deleted the crypto map.
- one of the common causes of problems in bringing up crypto tunnels is that the shared key for authentication does not match. I suggest that you re-configure this and do it very carefully.
the pre-shared key is ok, it wasn't that the problem, I solved it! :)
what was the problem? my inside-acl (how did you say to me) and the routing to the internet. my default static route in asav-milan had a wrong next-hop. because of this, asav-milan didn't reach asav-rome in the public network. now the VTI interfaces are up on both ASA firewalls!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2017 07:23 AM
Thank you for posting back to let us know that you have found the problem(s) and fixed them. (plus 5 for sharing the solution with the forum).
Thank you for the comment about the nat. I do see the point that the tunnel is a different interface and so the nat for the outside interface does not impact it. I am so used to thinking that a tunnel goes out a physical interface and so is impacted by nat on that interface, but with ASA it is a bit different.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2018 10:54 AM
Hi,
did you manage to establish IPsec btw ASA and Juniper by using VTI interface ?
BR
V
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide