- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Community Ask Me Anything- Configuration, Troubleshooting and Best Practices: Anyconnect Remote ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020
05:28 PM
- last edited on
04-27-2020
09:00 AM
by
Hilda Arteaga
![]()
| Español | Português | Français | Русский | 日本語 | 简体中文 |
This event continues the conversation of our recent Community Ask Me Anything event "Secure Remote Workers".
Here’s your chance to discuss more about the configuration, troubleshooting and best practices for AnyConnect secure mobility client on a Cisco Adaptive Security Appliances (ASA) and Firepower Threat Defense (FTD) and its integration with other Cisco security portfolio devices and technologies like ISE and Duo.
This session provides an opportunity to learn and ask questions about various aspects of AnyConnect implementation (using SSL and Ikev2) including (but not limited to) emergency licenses, configuration, deployment and troubleshooting AnyConnect that provides the security necessary to help ensure that your organization is safe and protected in such critical situation.
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Monday 6 to Friday, April 17, 2020
 Dinesh Moudgil is a High Touch Technical Support (HTTS) Engineer with the Security team at Cisco. He has been working on Cisco technologies for more than 6 years focusing on Cisco Next Generation Firewalls, Intrusion Prevention Systems, Identity Management and Access Control (AAA) and VPNs. He holds a CCNP, CCDP and CCIE #58881 certifications, and multiple vendors certifications such as ACE, PCNSE and VCP.
Dinesh Moudgil is a High Touch Technical Support (HTTS) Engineer with the Security team at Cisco. He has been working on Cisco technologies for more than 6 years focusing on Cisco Next Generation Firewalls, Intrusion Prevention Systems, Identity Management and Access Control (AAA) and VPNs. He holds a CCNP, CCDP and CCIE #58881 certifications, and multiple vendors certifications such as ACE, PCNSE and VCP. Pulkit Saxena works as High Touch Technical Support (HTTS) Engineer in Security Domain with Cisco bring nearly 7 years of experience in the industry to the team. He has hands on experience with multiple firewalls, different VPN solutions, AAA and Next Generation IPS along with delivering multiple trainings. Pulkit holds certifications from multiple vendors, namely Cisco and Juniper, (CCIE Security and JNCIA).
Pulkit Saxena works as High Touch Technical Support (HTTS) Engineer in Security Domain with Cisco bring nearly 7 years of experience in the industry to the team. He has hands on experience with multiple firewalls, different VPN solutions, AAA and Next Generation IPS along with delivering multiple trainings. Pulkit holds certifications from multiple vendors, namely Cisco and Juniper, (CCIE Security and JNCIA). Jason Grudier is the Technical leader on the VPN TAC team in Raleigh, NC. He has been working for Cisco on the VPN team for six years. Prior to joining the team, he was a network engineer at Labcorp. He works primarily with AnyConnect troubleshooting and configuration across all Cisco platforms as well as DMVPN, GETVPN, Radius, LDAP and Certificate authentications.
Jason Grudier is the Technical leader on the VPN TAC team in Raleigh, NC. He has been working for Cisco on the VPN team for six years. Prior to joining the team, he was a network engineer at Labcorp. He works primarily with AnyConnect troubleshooting and configuration across all Cisco platforms as well as DMVPN, GETVPN, Radius, LDAP and Certificate authentications. Gustavo Medina is a Systems Sales Engineer with the Enterprise Networking Sales team. He has more than 10 years of experience in security and enterprise networking. In his career he has focused on different tasks from technical escalations and partner adoption to the revision of Cisco Certification evaluations. Gustavo holds a CCNA, CCNP CCSI, and a CCIE in security (#51487).
Gustavo Medina is a Systems Sales Engineer with the Enterprise Networking Sales team. He has more than 10 years of experience in security and enterprise networking. In his career he has focused on different tasks from technical escalations and partner adoption to the revision of Cisco Certification evaluations. Gustavo holds a CCNA, CCNP CCSI, and a CCIE in security (#51487).By posting a question on this event you're giving permission to be translated in all languages we have in the community.
**Helpful votes Encourage Participation! **
Please be sure to rate the Answers to Questions
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Other VPN Topics
- Adaptive Security appliance
- AMA
- Annyconnect integration
- anyconnect
- Anyconnect Ikev2
- anyconnect posture
- anyconnect vpn
- asa
- ask me anything
- cisco
- Cisco Community
- cisco tac
- classic licensing
- coronavirus
- COVID 19
- Dinesh Moudgil
- Dynamic Access Policy
- emergency
- firepower
- firepower forum vent
- FirePOWER Threat Defense
- forum event
- FTD
- Gustavo Medina
- Host scan
- Jason Grudier
- license
- nam
- ogs
- Optimal Gateway Selection
- pandemic
- Pulkit Saxena
- remote access vpn
- secure remote worker
- security
- smart licensing
- ssl vpn
- tnd
- trusted network detection
- vpn
- wfo
- working from home
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 06:08 AM - edited 04-07-2020 06:10 AM
Hello jgrudier,
thanks for your answer.
I use LDAPs. If I'm not mistaken I can configure only FQDN with LDAPs.
Best regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 06:32 AM
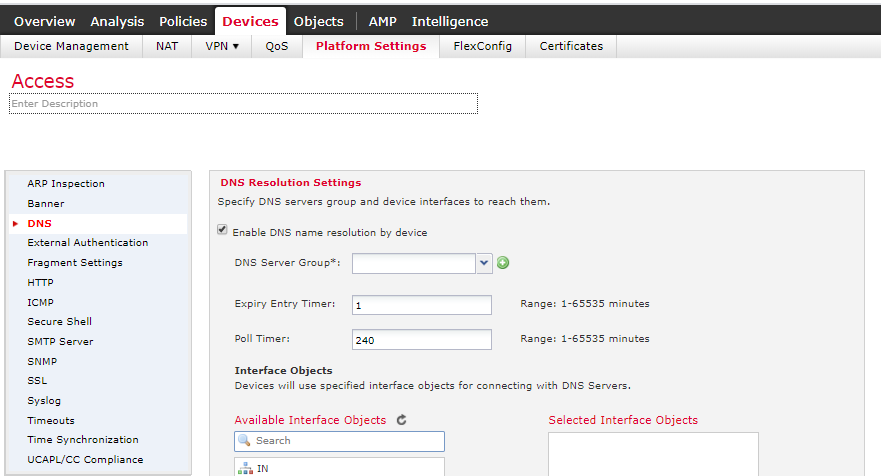
That is correct. I think there might be an issue with DNS not being set up properly on the FTD.
Have you set up DNS here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:02 AM
Thank, it was my mistake. But now I have new error:
[19] Session Start
[19] New request Session, context 0x00002b5de5d453b0, reqType = Authentication
[19] Fiber started
[19] Creating LDAP context with uri=ldaps://172.25.YY.XX:636
[19] Connect to LDAP server: ldaps://172.25.YY.XX:636, status = Failed
[19] Unable to read rootDSE. Can't contact LDAP server.
[19] Fiber exit Tx=0 bytes Rx=0 bytes, status=-2
[19] Session End
ldap_client_server_add: Add server:172.25.YY.XX, group=4
ldap_client_server_unlock: Free server:172.25.YY.XX, group=4
#telnet 172.25.YY.XX 636
Trying172.25.YY.XX...
Connected to172.25.YY.XX.
Escape character is '^]'.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:17 AM
Yes, I did it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:37 AM - edited 04-07-2020 07:41 AM
That is output of debug and ldaps config:
[27] Session Start
[27] New request Session, context 0x00002b5de5d453b0, reqType = Authentication
[27] Fiber started
[27] Creating LDAP context with uri=ldaps://172.25.XX.YY:636
[27] Connect to LDAP server: ldaps://172.25.XX.YY:636, status = Failed
[27] Unable to read rootDSE. Can't contact LDAP server.
[27] Fiber exit Tx=0 bytes Rx=0 bytes, status=-2
[27] Session End
ldap_client_server_add: Add server:172.25.XX.YY, group=4
ldap_client_server_unlock: Free server:172.25.XX.YY, group=4
telnet 172.25.XX.YY 636
Trying 172.25.XX.YY...
Connected to 172.25.XX.YY.
Escape character is '^]'.
^C
aaa-server srv protocol ldap
max-failed-attempts 4
realm-id 3
aaa-server srv-dc host srv-dc
server-port 636
ldap-base-dn DC=name,DC=local
ldap-group-base-dn DC=name,DC=local
ldap-scope subtree
ldap-naming-attribute samaccountname
ldap-login-password *****
ldap-login-dn user@name.local
ldap-over-ssl enable
server-type microsoft
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:41 AM
As a test, if you move back to LDAP, instead of LDAPs, does it succeed? Have you verified the certificate it a valid cert and the LDAP server has accepted it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:43 AM
I hadn't ever used ldap. Now migrate from ASA to FTP. And on the ASA ldaps works well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:47 AM
In System/Integration/Realms is the State i.O. and I can see the Usergroups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:11 AM
The FirePower Management Center has a Root CA Certificate. Should I install a certificate on the FTD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:29 AM
Does the FTD device have the root and sub CA certificates from the LDAP server as trusted CA's?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 09:16 AM
the FTD device have only Self Sign Certificate. The Root CA Certificate has only FirePower Management Center. I tried to add the Root CA in Devices/Certificate, but I don't see the certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 10:59 AM
I think it would be best for you to open a case, I would need to start looking at the certs and other specific configurations at this point and that is not a good thing to share here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 11:05 AM
Thanks for your answer. I did it yesterday (#SR 688828253), but so far I have no solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 11:21 AM
I will get with your engineer and take a look at the case.
Regarding the certificate install issue. Check out the video here starting at about 5 minutes. I go through the steps required for installing the cert on the FTD. I think the problem might be the CA you initially installed is no the CA that ultimately signed your identity certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 07:15 AM
Hello All,
Hoping someone might have some information to assist me.
I have a ASA 5585-SSP-10 pair running in context mode. It is version 9.8(2).
We have a customer who wants to configure dynamic split tunnels. However we cannot complete the configuration as it looks like under the section:
Remote Access VPN > Network (Client) Access > Group Policies > [policy name] > Advanced > AnyConnect Client
We need to assign the customer attributes to this group policy, however the custom attributes option is not avaliable on ASDM (7.8(2)).
I read the article below and it says you need AC 4.5 minimum and ASA 9.0 minimum, our AC is 4.7.
So not sure if there is something specific to us running a 5585 in context mode that is affecting this? Has anyone seen this before?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide