- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: 9800 and mDNS to Wired Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 04:16 PM - edited 07-05-2021 11:19 AM
Hi awesome community!
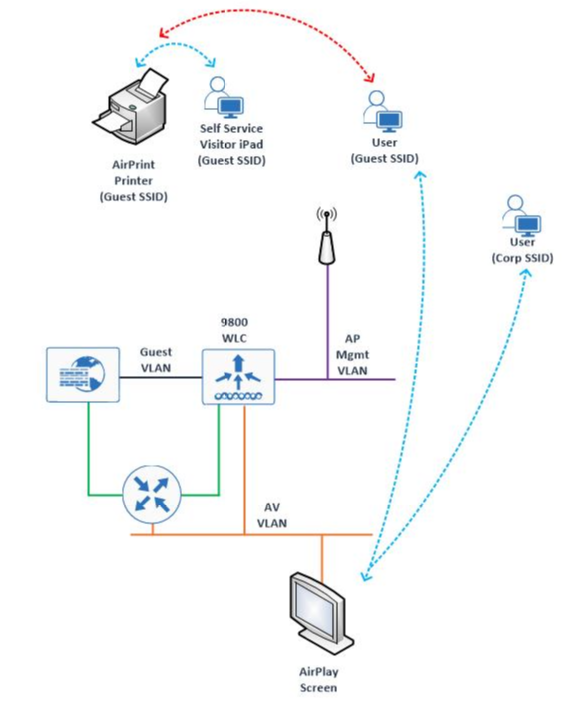
I'm really hoping that someone has a solution to this one - we're setting up a new 9800-40 controller for our corporate and guest wireless network. Once of the requirements is that we're able to AirPlay to devices that reside on our wired network, which is a different VLAN to both our Corporate wireless and Guest wireless network. With our older 55xx and 85xx controllers we're able to pick up the mDNS from the AP, which is fine and we can distribute this to our wireless network. With the 9800 this is co-located on the campus (as opposed to remotely with the legacy controllers) and while I've enabled mDNS, I can't see the mDNS services from the Corporate or Guest Wireless Network. If I look at the Cache on the 9800, I can see the mDNS entries from the wired network.
While the Guest Traffic would route via a Firewall, the Corporate Traffic should go via an internal L3 router, but again - I'm not picking up the mDNS cache from the 9800. The AV VLAN has a VLAN and an SVI on the 9800, the Corporate and Guest VLAN's exist on the controller, but with no SVIs.
The Second part of this is doing Air-Print over the Guest network for a specific device, I know with the older controllers I can contain the mDNS discovery and push profiles with ISE to permit this, but I can't seem to control it in the same way as the older controllers. For now however - the priority would be the AirPlay discovery.
I'll take any suggestion at the moment as I'm all out of ideas on how I can get AirPlay to show on the Wireless Network.
Thanks
Kev
Solved! Go to Solution.
- Labels:
-
Catalyst Wireless Controllers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 04:13 PM
Ok then - so a bit more testing and digging and here is the solution:
mDNS "Bridging" on the WLAN config enables Wireless Airplay to function *BUT* without any filtering, so anything on the WLAN will see mDNS, printers, iTunes etc are all exposed on the SSID - only on the SSID.
mDNS "Gateway" allows the control using the Service Lists and policies, however you need to implement extra steps to see the mDNS follows to control them.
You have to create SVI's in the wireless VLAN. In the above example, you have to create say interface vlan 10 for Corp and vlan 11 for Guest. Then, you have to give the SVI an IP address in that VLAN - just like you would with AireOS controller interfaces. Finally, you have to enable mdns-sd gateway under the SVI. You do not need to specify a service profile - unless you want to filter the results at this level. (Do via the CLI)
You have to globally enable MDNS on the controller (under mDNS) but you do not have to enable Wireless Multicast and Wireless mDNS bridging under the Multicast menu).
Finally, you can implement The service profiles - either on the WLAN directly or overriding it with ISE (or a RADIUS server of your choice) - we're using ISE here.
So in my example I have two requirements.
1. Corporate and Guest Devices should be able to see AirPlay services being advertised.
2. Certain Devices on the Guest Wireless will need to be able to see a AirPrint Printer - but importantly not all Guest Devices (or corporate connected devices).
If you run Bridging on the Guest SSID, all devices on that SSID can see the printer, so Gateway is the way to go, and then adding SVI's and mdns-sd gateway to them (do this via CLI)
Create the mDNS Profiles to suit your needs - I've used two - one for AirPlay and one for AirPrint.
Add them to your Applicable AuthZ Profile:
cisco-av-pair = mDNS-profile-name=Airplay
or
cisco-av-pair = mDNS-profile-name=AirPrint
Push the applicable profile - ISE will override the default, so you could default create a profile that blocks all mDNS or just have AirPlay as the default, then send AirPrint as the override.
At this time, I can't see the way of restricting services to an "AP Group" or site, but in my deployment the 9800 is in a single campus environment, rather than the AireOS controllers that service many Campus locations. That said - it would be better if I could restrict them a little by "floor" so people don't see a list of 150+ devices in the AirPlay list. If I come up with a solution for that - I'll update here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 12:17 PM
Ok, so have a solution for this (well I think I have!)
As soon as I’ve confirmed it then I’ll update with a solution for anyone that runs into this in the future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 04:13 PM
Ok then - so a bit more testing and digging and here is the solution:
mDNS "Bridging" on the WLAN config enables Wireless Airplay to function *BUT* without any filtering, so anything on the WLAN will see mDNS, printers, iTunes etc are all exposed on the SSID - only on the SSID.
mDNS "Gateway" allows the control using the Service Lists and policies, however you need to implement extra steps to see the mDNS follows to control them.
You have to create SVI's in the wireless VLAN. In the above example, you have to create say interface vlan 10 for Corp and vlan 11 for Guest. Then, you have to give the SVI an IP address in that VLAN - just like you would with AireOS controller interfaces. Finally, you have to enable mdns-sd gateway under the SVI. You do not need to specify a service profile - unless you want to filter the results at this level. (Do via the CLI)
You have to globally enable MDNS on the controller (under mDNS) but you do not have to enable Wireless Multicast and Wireless mDNS bridging under the Multicast menu).
Finally, you can implement The service profiles - either on the WLAN directly or overriding it with ISE (or a RADIUS server of your choice) - we're using ISE here.
So in my example I have two requirements.
1. Corporate and Guest Devices should be able to see AirPlay services being advertised.
2. Certain Devices on the Guest Wireless will need to be able to see a AirPrint Printer - but importantly not all Guest Devices (or corporate connected devices).
If you run Bridging on the Guest SSID, all devices on that SSID can see the printer, so Gateway is the way to go, and then adding SVI's and mdns-sd gateway to them (do this via CLI)
Create the mDNS Profiles to suit your needs - I've used two - one for AirPlay and one for AirPrint.
Add them to your Applicable AuthZ Profile:
cisco-av-pair = mDNS-profile-name=Airplay
or
cisco-av-pair = mDNS-profile-name=AirPrint
Push the applicable profile - ISE will override the default, so you could default create a profile that blocks all mDNS or just have AirPlay as the default, then send AirPrint as the override.
At this time, I can't see the way of restricting services to an "AP Group" or site, but in my deployment the 9800 is in a single campus environment, rather than the AireOS controllers that service many Campus locations. That said - it would be better if I could restrict them a little by "floor" so people don't see a list of 150+ devices in the AirPlay list. If I come up with a solution for that - I'll update here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2020 01:45 PM
Hey Kev, I know this post is a little dated but wanted to ask the question. Does the new wlc allow us to do the mdns ap that allows the ap to snoop the mdns traffic froma switch port. This was the solution in the old solution to learn about mdns services that separated by a layer 3 link.
Thanks,
Kanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2020 01:05 AM
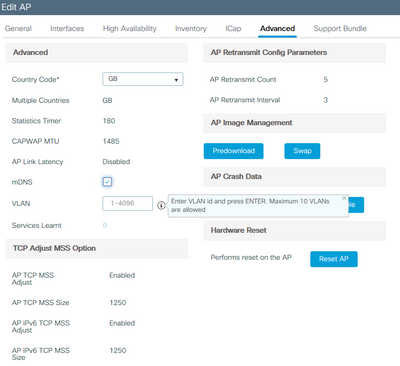
Hey Kanan! The option to configure mDNS under an AP and nominate the VLAN's is still there on the 9800:
I've not had a requirement to use this option just yet - I'm sure that will come as our 9800 estate expands.
Kev
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 06:42 AM
Thank you Kev. I'm currently at version 16.12 and do not see that option. What version is this screenshot from?
Kanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 07:01 AM
No problem! The screenshots are from 17.3.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 07:05 AM
Thanks what I was thinking. I see an upgrade int he near, near future.
Thank you !
'Kanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2021 05:55 PM
FYI - It also depends on the AP version. I'm running WLC 17.3 and see that option on 9100s but not on 4800 APs....
The 4800s are passing mDNS packets, so I don't understand what that switch does just yet on the 9100s...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2024 08:12 AM
For anybody using IOS-XE 17.6 and later please take note of https://bst.cisco.com/bugsearch/bug/CSCwd59093
17.9 || 9800 WLC does not learn mDNS service from wired
Workaround: Disable Multicast Link Local
conf t
no wireless multicast link-local
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2024 02:49 PM
Thanks for posting that. I was just knee-deep in mDNS troubleshooting and was struggling to figure out why it worked before being upgraded. Ran the command and all is well again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2024 02:10 PM
Just set up a local 9800 WLC with mDNS on 17.9.5. You need to have Multicast working and have a group specified for the AP's to join. You also need to have IGMP V2 snooping working on your switching infastructure.
The wireless management vlan has mdns-gateway defined
mdns-sd gateway
active-query timer 15
mdns-ap-service-policy xxxxxxxxx
source-interface Vlanxx
interface Vlan20
description Management
ip address x.xxx
mdns-sd gateway
service-policy XXXXXX
mdns-sd service-list xxxxxx-mdns-out OUT
match itune-wireless-devicesharing2
match apple-windows-fileshare
match apple-timecapsule-mgmt
match multifunction-printer
match apple-itunes-library
match phillips-hue-lights
match apple-remote-events
match google-expeditions
match apple-screen-share
match apple-remote-login
match apple-itunes-photo
match apple-itunes-music
match google-chromecast
match apple-timecapsule
match apple-file-share
match apple-continuity
match printer-socket
match apple-airprint
match amazon-fire-tv
match apple-keynote
match apple-homekit
match printer-ipps
match workstation
match printer-lpd
match printer-ipp
match homesharing
match web-server
match apple-rdp
match airserver
match apple-tv
match airtunes
match spotify
match scanner
match airplay
match roku
match fax
match spotify-connect
match device-info
!
mdns-sd service-list xxxxxx-mdns-in IN
match fax
match roku
match airplay
match scanner
match spotify
match airtunes
match apple-tv
match airserver
match apple-rdp
match web-server
match homesharing
match printer-ipp
match printer-lpd
match workstation
match printer-ipps
match apple-homekit
match apple-keynote
match amazon-fire-tv
match apple-airprint
match printer-socket
match apple-continuity
match apple-file-share
match apple-timecapsule
match google-chromecast
match apple-itunes-music
match apple-itunes-photo
match apple-remote-login
match apple-screen-share
match google-expeditions
match apple-remote-events
match phillips-hue-lights
match apple-itunes-library
match multifunction-printer
match apple-timecapsule-mgmt
match apple-windows-fileshare
match itune-wireless-devicesharing2
match spotify-connect
match device-info
!
mdns-sd service-policy xxxxxx-mdns-policy
service-list xxxxxx-mdns-in IN
service-list xxxxxx-mdns-out OUT
wireless multicast
wireless multicast non-ip
wireless multicast 239.1.1.1 ( Your choice all AP's will use this group )
wireless profile policy YYYYY
ipv4 arp-proxy
ipv4 dhcp required
mdns-sd service-policy XXXXX-policy
radius-profiling
session-timeout 43200
vlan YYYYY_SSID
no shutdown
One of the Key things is to see the AP's seeing multicast traffic. The command is
show ap multicast mom
AP Name MOM-IP TYPE MOM-STATUS
-----------------------------------------------------------------
APNAME IPv4 Up
when you do show mdns-sd cache you will see the management vlan in the cache
If you have bonjour traffic on a different vlan from the WLAN you will need that vlan in the IGMP v2 snooping
I don't have SVI for any of teh WLAn other than management.
I have Wireless Broadcast and Wireless Non-IP Multicast enabled on the WLAN's that i have WLAN SSID on and also MLD snooping
-link._tcp.local 4500 WIRED XX 001b.1700.1530
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide