- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- ISE 2.1 802.1X and MAC filtering
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 02:18 AM - edited 07-05-2021 09:35 AM
Hi,
we have an SSID with more or less this configuration:
802.1X validated with an Identity Group user (Internal users)
We want to permit access only a devices that are included in a Identity group endpoint (a MAC address list).
How can add a policy to validate this point in my actual configuration?
Thanks in advance.
Samuel
Solved! Go to Solution.
- Labels:
-
ISE
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:32 AM
I found the solution:
In the controler SSID select MAC filtering.
authentication rules:
1- 802.1x and use:AD
2-MAB and use: indentity endpoint
in authorization:
1 rule: Identity: AD and 802.1x
2 rule: Identity: Identity group endpoint and condition MAB
result both the same.
the first process, as I select the MAC filtering in the controller, are the rules with MAB, and later use the 802.1x.
if one of them fails. can't access!! :)
thanks!! :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2018 08:53 PM
Interesting question
There is no easy way to do this as far as I know.
if you had the users in AD, then you could perhaps have an AD user object (e.g. macAddr) that contained the MAC address, and then in your Authorization Policy you could try an AND rule that looks something like:
MY_AD macAddr EQUALS Radius Calling-Station-Id
No idea if that will work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:32 AM
I found the solution:
In the controler SSID select MAC filtering.
authentication rules:
1- 802.1x and use:AD
2-MAB and use: indentity endpoint
in authorization:
1 rule: Identity: AD and 802.1x
2 rule: Identity: Identity group endpoint and condition MAB
result both the same.
the first process, as I select the MAC filtering in the controller, are the rules with MAB, and later use the 802.1x.
if one of them fails. can't access!! :)
thanks!! :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:48 AM
Did you set this up in your lab? How does the controller do MAB and 802.1X on the same wlan profile? I didn’t know it was possible to mix the two auth methods.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 03:17 AM
yes, not in lab, in production. is a new SSID.
the SSID is a WPA2 entreprise, so is 802.1x, but if you select MAC Filtering in the SSID (security) the controller first send the authentication/authorization for the MAC, and later the 802.1x.
Is working fine.
:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 04:14 PM
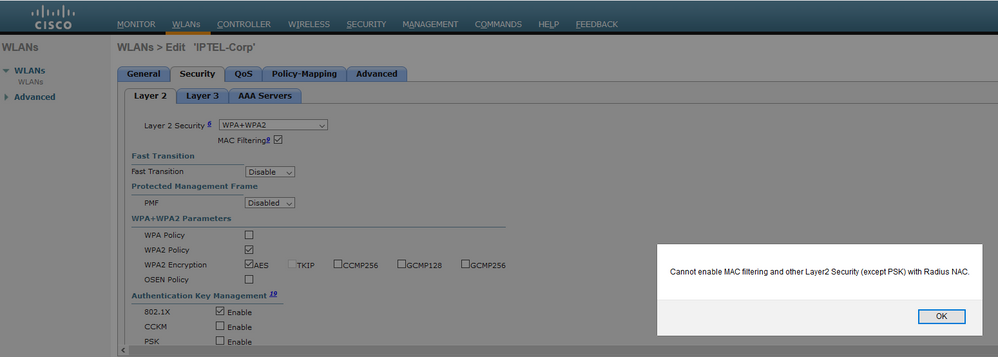
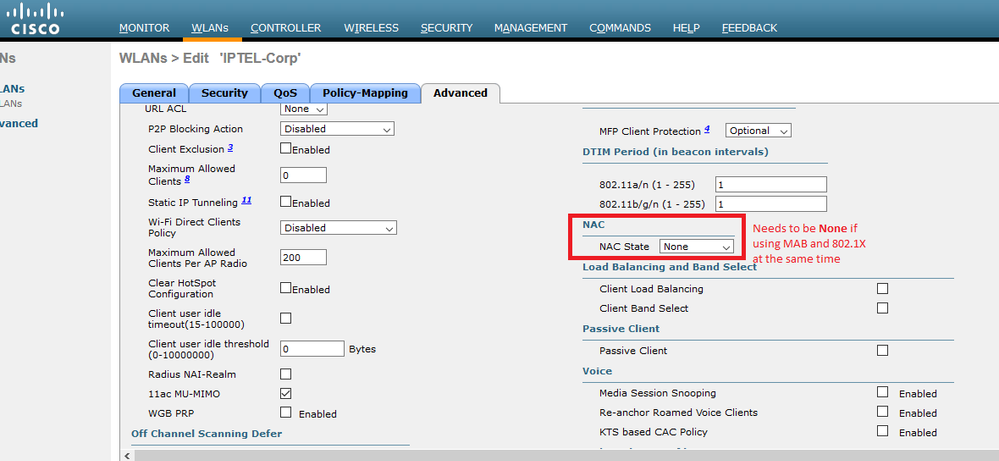
I just tried this on our Cisco virtual controller (8.5.131.0) and I had to turn off the Radius NAC in the WLAN in order for MAB to be enabled at the same time. And yes this is pretty amazing - thanks for pointing this out. I am wondering what this Radius NAC setting does ... ? Because we just blindly set this according to all the docs ... now 802.1X and MAB work just fine without it. I think I am about to learn something new ... do you have any clues what this is for?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2020 06:59 PM
eg user enter username/password on laptop.
un/pw info + wifi mac pass to WLC -> ISE
ISE authencticate first on authentication rule1? then rule2? then authoriation rule 1 rule2?
would you please explain on above?
thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide