- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: ME: MAC address to VLAN mapping
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2018 03:19 PM - edited 07-05-2021 09:33 AM
I use a WPA2-PSK SSID for IoT devices which don't support 802.1X. Now some of those devices need to be moved to a separate VLAN. Can this be done with Mobility Express (8.8.100.0) without creating yet another SSID? I'm thinking about MAC-to-VLAN mapping.
Maurice
Solved! Go to Solution.
- Labels:
-
Aironet Access Points
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 12:15 PM
I have older code, with even fewer GUI options. But it's all there in the CLI. If you haven't already added a RADIUS server, you can use this CLI.
config radius auth add 1 [IP address] 1812 ascii [shared secret]
These commands will enable AAA override, MAC filtering, and call out your RADIUS server on the WLAN.
config wlan disable [wlan ID]
config wlan aaa-override enable [wlan ID]
config wlan mac-filtering enable [wlan ID]
config wlan radius_server auth add [wlan ID] 1
config wlan enable [wlan ID]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2018 02:18 AM
IPSK (Identity PSK) is the feature you need for it. Since 8.5.x onward WLC software versions support it. See if it works for ME as well
HTH
Rasika
*** Pls rate all useful responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2018 08:52 AM
Hey Rasika,
Thanks, that is an interesting feature indeed.
Unfortunately it's not mentioned in the ME documentation at all so it might not be supported. And the configuration required seems to be rather complex, especially since I don't have Cisco ISE. So I'd want to make sure there is a real chance of succeeding before going this way.
So, anyone out there who has IPSK working with Mobility Express?
Or is there a simpler (MAC-based) solution?
Maurice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:47 AM
There is an old-school method, but it comes with the burden of enabling MAC filtering on the WLAN and managing local MAC address entires on the WLC.
Set the security of the WLAN to be WPA2-PSK + MAC filtering. Also enable AAA override on the WLAN.
For the devices that need to be sent to different VLANs, create local MAC filtering entires for them on the WLC and map them to the appropriate interface in the MAC filtering entries. When they connect, a MAC filter check is done and the clients are overriden to the mapped interface.
Now for devices that don't need to be overriden, you have a couple of choices. You can manually create local MAC entries for all of them on the WLC and omit assigning them to an interface (or maybe you do need to still map them to their intended interface). Or, you can send all unknown MAC lookups to your RADIUS server and have your RADIUS server configured to send back a regular Permit for every MAC auth coming from the WLAN. The latter would be way less work as you then only need to manage the list of devices that need overrides rather than the list of every device on the WLAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 09:22 AM
Hi,
Thanks, this method seems to be what I'm looking for. But I can't figure out how to configure it.
MAC filtering and AAA override can be enabled for the WPA2-PSK SSID. Local MAC entries can be created, but I can't find an option to map them to specific VLANs. The only option is "blacklist" or "whitelist". Also, a RADIUS server can only be added to 802.1X SSIDs, not to PSK SSIDs.
Are you sure this is supported on Mobility Express?
Thanks,
Maurice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 10:16 AM
Good question... I tried to make that work, and was unable to do so in ME, even in the CLI. But then I realized that I should have just told you to enable MAC filtering and send ALL auths to RADIUS. Then the RADIUS server can do the VLAN overrides for you.
You can simply create as many endpoint groups as you need for the different VLANs to send endpoints to. Write up RADIUS rules to send MAC requests from group A to VLAN A, Group B to VLAN B, and so on. Anything not in groups should hit a rule that just sends back a permit.
I tested this with ME and ISE, and it worked just fine. You just need to be sure to pre-populate any needed VLANs in ME. I don't know if there's a way to do that in the GUI. But you can do it with the following CLI command.
config flexconnect group default-flexgroup vlan add [VLAN Number] acl none none
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 11:17 AM
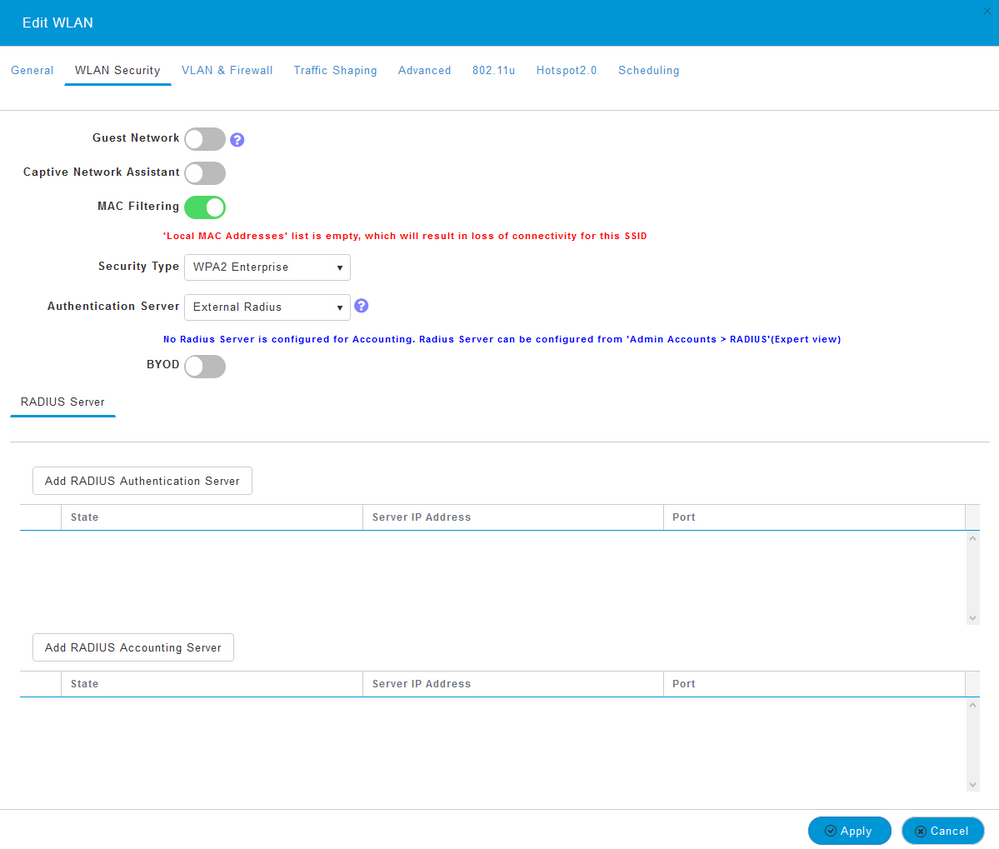
OK, so when enabling MAC filtering and allowing AAA override for a PSK SSID, all auth requests will be sent to one of the RADIUS servers configured in Management / Admin Accounts / RADIUS? Asking because it's not possible to add a RADIUS server to a PSK SSID:
And can the warning about the empty local MAC addresses list just be ignored?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 12:15 PM
I have older code, with even fewer GUI options. But it's all there in the CLI. If you haven't already added a RADIUS server, you can use this CLI.
config radius auth add 1 [IP address] 1812 ascii [shared secret]
These commands will enable AAA override, MAC filtering, and call out your RADIUS server on the WLAN.
config wlan disable [wlan ID]
config wlan aaa-override enable [wlan ID]
config wlan mac-filtering enable [wlan ID]
config wlan radius_server auth add [wlan ID] 1
config wlan enable [wlan ID]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 04:09 PM
Also, I kind of missed your last question. You can ignore any warnings about the local MAC filtering list being empty. The logic with MAC filtering is to look locally first. If the entry is not found locally, then it would look externally using RADIUS. With no local entries, it would then look externally every time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2019 10:19 AM
It's been a while, but I finally got it working! In ME 8.8.111.0, adding a RADIUS server to a PSK SSID is now possible in the GUI. You still have to send all requests to an external RADIUS because the local MAC filtering list is missing an "assign VLAN" option (blacklist / whitelist only).
My RADIUS server is Microsoft NPS and it took me a while to figure out how to configure it without having to add MAC addresses to Active Directory, but in the end it turned out to be easier than expected.
Thanks again for your help!
Maurice
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide