- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Applications
- Re: MRA login over Expressway-E is failing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 03:17 AM
I setup a expressway C and E, I am trying to Login a MRA over expressway E and C but receiving this message from
Action plan
Create an SSL certificate with either the top level domain xxxxxx.co.uk or the subdomain collab-edge.xxxxxx.co.uk in the SAN field and upload it to the Expressway-E xx.xxx.xxx.xxx.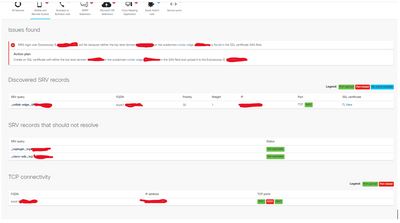
Solved! Go to Solution.
- Labels:
-
Jabber
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 07:52 AM
I believe this is the issue:
The tomcat(-ECDSA) certificate of the following CUCM / IM&P / Unity nodes is not trusted by the Expressway-C: imp.xxxxxx.co.uk, cucmsub01.xxxxxxx.co.uk, cucmpub.xxxxxx.co.uk. This leads to MRA login issues.
Expressway-C X14.2 and higher versions running MRA services are affected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 10:29 AM
If you read the documentation for this release, in the release notes if I’m not mistaken, there is a section on this topic. You can change the behaviour of this if you don’t want to use EC signed certificates.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 11:20 AM
The short term solution is to apply the workaround as documented to fallback to the previous behavior before X14.2.0. You can perform on this through the CLI on the Expressway-C server nodes with the newly introduced command:
xConfiguration EdgeConfigServer VerifyOriginServer: Off

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 11:53 AM - edited 05-11-2023 11:53 AM
There is a way to alter the ciphers that is used, so that RSA is preferred over EC. I remember reading it in the release notes, but for the love of me I cannot find it again. That’s a better solution than to use the xconfig command.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2023 02:58 AM
Found the cipher string we ended up using on our MRA C for them to favor the RSA signed CA certificates on CM/CUC. We don't use CUPS any longer, but if we did it would apply to that as well.
ECDHE-RSA-AES256-GCM-SHA384:EECDH:EDH:HIGH:-AES256+SHA:!MEDIUM:!LOW:!3DES:!MD5:!PSK:!eNULL:!aNULL:!aDH
I also found the part in the release notes that I couldn't locate yesterday, I blame the small screen as I was trying to find it using my mobile device.
Cipher Preferences - ECDSA Cipher Preference Over RSA
ECDSA certificates are preferred over RSA.

Important |
The following points lists the various upgrade path(s) that are mandatory for upgrading ciphers.
|
It's found in this document Cisco Expressway Release Note (X14.2.5)

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2023 01:49 AM
Certificate issue is resolved now, thanks for all your efforts
However, this is the latest error message:
Tested UDS servers
-
cucmpub.xxxxxx.co.uk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2023 02:00 AM - edited 05-12-2023 02:02 AM
You don't need a jabber-config file, for MRA to work.
And honestly, have you ever reviewed how MRA works and which steps do you need to configure it? You just tripping over "normal" failures, which wouldn't come up, if you know how to install MRA. Your "errors" are not real errors, they are configuration errors, because you don't know how MRA works and how to configure it, in my opinion. And I don't think, you shouldn't bother a help forum (where people spent their free time helping others), when you don't even know the basics. It's not a teaching platform.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2023 02:10 AM
@b.winter, you are probably right on that point. I have not configured MRA before, but I have read as much as I could on how to configure it. The Cisco MRA configuration guide doesn't give you a solution for the error you face when following the configuration steps.
If you know something that others may not, it's wrong to assume that everyone knows it. That's why this forum exists. However, I appreciate everyone's effort and help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2023 03:57 PM
Can you let us know the issues which you currently facing after clearing the certificate errors. As @b.winter mentioned, jabber-config file is not required.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2023 12:16 AM
Still facing same login issue, even tried to apply
xConfiguration EdgeConfigServer VerifyOriginServer: Off- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2023 06:38 AM
If you still have the issue why have you marked your post as solved?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2023 08:57 AM
I tried to disable TLS mode using xConfiguration EdgeConfigServer VerifyOriginServer: OFF, but after executing this command and restarting Expressway C, I am still getting the error message 'SSL Connection failed for publisher and subscriber.'"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2023 10:52 AM
Have you read the other suggestions made to your post. Also once again, if you still have issues it’s not good to mark the post as solved.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2023 10:16 PM
I assume you are using TLS between CUCM and Expressway, What certificate you use for CUCM ? self signed or CA signed. If CA signed, both expressway C and CUCM are signed by same CA. As a test, disable the TLS between CUCM and Expressway and use TCP.
Would you be able to share the domains which is configured for Expressway C and CUCM ? And a little more about your setup to help you.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2023 02:56 AM
I am using one domain on both external and internal. External DNS resolves _collab-edge._tls and _sip._tcp and internal DNS resolves cisco-uds._tcp and cuplogin_tcp
CUCM(cluster publisher, subscriber and IM&P)--->Exp C---->Exp E---MRA
I've created CUCM SIP Trunk pointing toward Exp C with TCP 5060, I've also created Neighbor Zone on Exp C pointing cucm publisher with TCP 5060. I disabled the TLS between CUCM and ExpresswayC using xConfiguration EdgeConfigServer VerifyOriginServer: OFF
I tried to use TLS but unfortunately as this is a lab setup, I could not change my CUCM cluster to mixed mode because my server was unable to verify smart license token. With a trail license can not change cluster mode
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide








