- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: SSH Connection Refused
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2020
01:05 PM
- last edited on
05-15-2023
09:48 PM
by
Translator
![]()
I have a dumb problem. We have several Cisco 881 routers deployed that are doing a simple site-to-site VPN back to us from users home offices. When I have them setup in my lab on our internet connection I can SSH to the LAN IP address (over the VPN) no problem. However when they are deployed to the field, I cannon SSH, putty gives me a "Network error: Connection refused" message. I believe it is in relation to my
access-list
but I'm not sure how. Below is the running config I have of one specific device.
They do have an ssh RSA key (4096) generated on them before shipping out. Let me know if more relevant config is needed. Unfortunately I can't get to any of the 18+ devices we have deployed, but I do have another on my bench with the same config that works.. My management PC is on the 172.17.14.0/24 subnet so that would fall within the 172.16.0.0 0.15.255.255 wildcard bit mask we have on the ACL as well. Running Version 15.7(3)M.
line con 0
logging synchronous
no modem enable
transport preferred none
stopbits 1
line aux 0
stopbits 1
line vty 0 4
access-class Management in
privilege level 15
logging synchronous
transport preferred none
transport input ssh
line vty 5 15
transport preferred none
transport input none
!
ip access-list standard Management
permit 172.16.0.0 0.15.255.255
!
interface FastEthernet4 (internet interface for home user)
ip address dhcp
ip virtual-reassembly in
duplex auto
speed auto
crypto map XXX
service-policy input pm-bandwidthlimit
service-policy output pm-bandwidthlimit
Solved! Go to Solution.
- Labels:
-
Other Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2020
07:35 AM
- last edited on
05-15-2023
09:58 PM
by
Translator
![]()
Well, when I do a
sh ip ssh
it states that ssh is disabled. So I then copy and pasted my standard line to generate a new rsa key at 4096 and it froze. I then restarted and generated one at 2048 and it generated and enabled SSH. Perhaps this device was not capable of generating a key with a length of 4096 and that was my problem. My standard config I use for our Cisco 4331 routers and 9300 switches generates a 4096 rsa key. Perhaps these smaller devices can only do 2048?
at-lte-agent-53#sh ip ssh
SSH Disabled - version 2.0
%Please create RSA keys to enable SSH (and of atleast 768 bits for SSH v2).
Authentication methods:publickey,keyboard-interactive,password
Authentication Publickey Algorithms:x509v3-ssh-rsa,ssh-rsa
Hostkey Algorithms:x509v3-ssh-rsa,ssh-rsa
Encryption Algorithms:aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc
MAC Algorithms:hmac-sha1,hmac-sha1-96
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 1024 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded): NONE
at-lte-agent-53#config t
Enter configuration commands, one per line. End with CNTL/Z.
at-lte-agent-53(config)#crypto key generate rsa modulus 4096
The name for the keys will be: at-lte-agent-53.xxxx.com
% The key modulus size is 4096 bits
% Generating 4096 bit RSA keys, keys will be non-exportable...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2020 07:49 AM - edited 12-17-2020 07:50 AM
Well I see from a Cisco page that with IOS 15.1 and up you CAN do 4096, and this particular device was running 15.4(3)M3 which shoudl allow for a key size of 4096. I'm cool with this being my solution though, and only generating a key size of 2048.
"Effective with Cisco IOS XE Release 2.4 and Cisco IOS Release 15.1(1)T, the maximum key size was expanded to 4096 bits for private key operations. The maximum for private key operations prior to these releases was 2048 bits."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2023 03:07 AM
No it didn't freeze - it just takes much longer. Generating the 4096 modulus key is CPU intensive so on those older routers can literally take a few minutes. You just need to be patient. Keep using 4096 on any IOS where it's supported to keep it future-proofed and as secure as possible.
Please click Helpful if this post helped you and Accept as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2023 05:19 PM
Hi Richard,
I was having same issue here. After we replace the UPS on one of our sites the devices are rebooted but prior on replacing the UPS the configs are saved. So after it turn back on I can access anything except this 9300 switch. What weird is I can ping the MGMT IP but when I tried to remote it says "The remote system refused the connection." I console on the switch and did confirmed nothing has been change. The MGMT IP is same the interface vlan is pointed to Tacacs and Radius servers, the Line VTY is there and the Crypto Key RSA is there too. I tried to do a debug but nothing shows. The configs are same with other switch and nothin has been change. I did check the SSH by doing shw IP SSH and it was disabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2023 05:18 PM
Hi Travis,
I was having same issue here. After we replace the UPS on one of our sites the devices are rebooted but prior on replacing the UPS the configs are saved. So after it turn back on I can access anything except this 9300 switch. What weird is I can ping the MGMT IP but when I tried to remote it says "The remote system refused the connection." I console on the switch and did confirmed nothing has been change. The MGMT IP is same the interface vlan is pointed to Tacacs and Radius servers, the Line VTY is there and the Crypto Key RSA is there too. I tried to do a debug but nothing shows. The configs are same with other switch and nothin has been change. I did check the SSH by doing shw IP SSH and it was disabled.
Any suggestion is greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2023 05:36 PM
> I did check the SSH by doing shw IP SSH and it was disabled.
You've answered your own question - SSH is disabled! So enable it:
ip ssh version 2
and then re-generate the key as per @Travis-Fleming example above!
Please click Helpful if this post helped you and Accept as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2023 05:45 PM
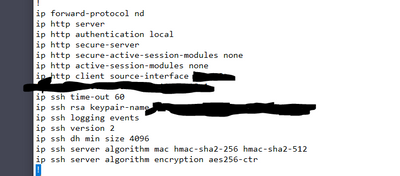
Hi Rich,
I have save the configs prior on replacing the UPS and yesterday I did check and verified SSH is enabled however it was pointed on our old vlan interface and ip route is pointed to an old ip. But weird is after replacing the UPS SSH suddenly don't work? in fact nothing has been change and the other switches that currently working after replacing UPS has the same configs. Please see screen shot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2023 07:43 PM
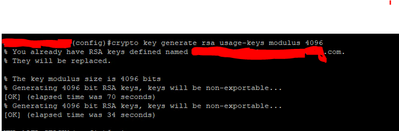
Hi Rich,
I just repasted the SSH command and i got a message generate a RSA KEY so I created a RSA key with 4096 bits and i got this message please see screen shot. The way i'm thinking right now is rebooting the switch after hours. what you think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2023 03:18 AM
Replying a bit late but those messages are normal when you re-generate the key.
If in doubt a reload is always worth a try but should not normally be needed.
Please click Helpful if this post helped you and Accept as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2020 03:29 PM
I think you need here ASA port forward for SSH.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2021 01:17 AM
Hi there,
Came across the same issue, the problem was with conflicting IP addresses. The LAN I was connecting from using AnyConnect and the remote network to which I was connecting were using the same IP subnet. I did not invest much time to find a work around because I have other ways to connect, but the source of the problem lies in routing and NAT.
Cheers,
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide