I am extremely proud that Cisco is leading the charge with a remarkable suite of open source AI projects. These initiatives aren’t just research experiments; they’re production-ready tools that addres...

Summary:Proxy ARP is enabled by default on all ASA/Firepower interfaces, but it generally comes into effect only when NAT is configured. Under normal circumstances, when traffic flows between a source...

Implementing IPsec over DMVPN Phase-3 Tunnels
Introduction
Lab Topology
IPsec Configuration
Verification
Conclusion
Introducti...

DMVPN Phase 3 Implementation
Introduction
Lab topology
Phase 3 Tunnel Configuration
Routing Protocol (Eigrp)...

Building AI is one thing; securing it is another. While constructing powerful AI systems, the real challenge lies in anticipating how they might be attacked or exploited. That’s where AI red teaming s...

DMVPN Phase-2 Implementation
Introduction
Overlay Configuration
Routing Protocol Configuraton
Verification
Conclusion
Int...

Site-to-Site IPSec VPN with Overlapping Subnets
Introduction
The Problem
The Solution
Lab Example
Introduction
To configure a si...

Understanding Internet Key Exchange (IKE) Protocol
IKE Operation
Main Mode Vs Aggressive Mode
IKE Phase-1
IKE Phase-2
Conclusion
IKE Opera...

We are all experiencing the rapid proliferation of autonomous AI agents and Multi-Agent Systems (MAS). These are no longer AI chatbots and assistants; they are increasingly self-directed entities capa...

The Model Context Protocol (MCP) is an open standard that provides a universal way to connect AI models and agentic applications to various data sources and tools. It's how AI applications and applica...

How do you extend the idling timeout screen?

Are you trashing/changing the default network discovery rule which is 0.0.0.0 for applications?

Cisco Duo SecurityDuo Security was a company acquired by Cisco that develops a very popular multifactor authentication solution that is used by ...

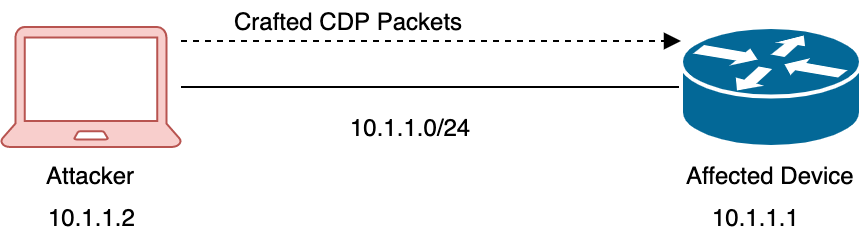
Many organizations fail to use one of the strongest tools that can help protect against today's security threats, the Network itself. For example, Cisco Catalyst switches, Data Center switches, ASR ro...

Does your organization use Splunk, Cisco Catalyst Center (formerly DNA Center) or Cisco Identity Services Engine (ISE) to manage your network?
Do you have security concerns about unmanaged endpoints o...