Introduction
Cisco ASAs and FTDs can be configured with Certificate Authority to perform various jobs, like authenticating the users based on certificates before they connect to the VPN. However, the certificate trust points must also connect to the CA and download the CRLs. Using this blog, we're trying to explain how we can configure, test, and troubleshoot scenarios related to CRL checks.
Reference
https://www.cisco.com/c/en/us/support/docs/security/secure-client/221575-troubleshoot-crl-for-anyconnect-certific.html
Configuration
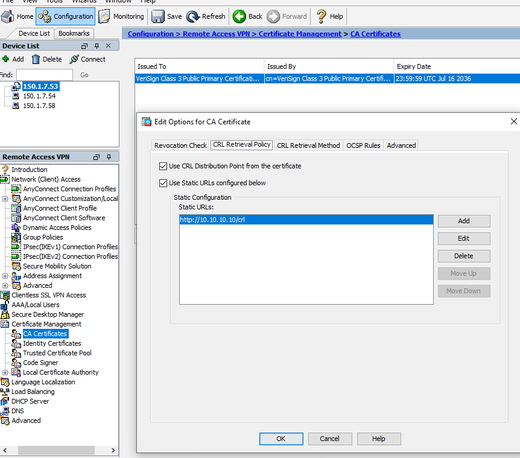
crypto ca trustpoint Cisco_CA
revocation-check crl
enrollment terminal
crl configure
policy static
url 1 http://10.10.1.22/%20CA3.crl
Troubleshoot
1. Manually force the ASA/FTDs to request the CRL
ASA(config)# crypto ca crl request Cisco_CA
CRYPTO_PKI: CRL is being polled from CDP http://10.10.1.22/%20CA3.crl
CRYPTO_PKI: transaction HTTPGetCRL completed, status (106)
CRYPTO_PKI: CRL is being polled from CDP http://10.10.1.22/%20CA3.crl.
Unable to retrieve or verify CRL
2. Run a packet capture on the ASA/FTD to see the response from the CA server, typically a TCP 3-way handshake first.
3. Check the network firewalls, if they are dropping the flow.
4. Debug
debug crypto ca transactions 10
