- Cisco Community
- Technology and Support
- Networking
- Switching
- Access point fails to connect to WLC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Access point fails to connect to WLC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 05:06 AM - edited 03-08-2019 07:29 AM
I did a factory reset of a cisco AIR-LAP1131AG-N-K9. I is now failing to connect to our 2504 WLC. It had been connected in the past. The console is looping with the following:
*Sep 20 11:58:21.000: %CAPWAP-5-DTLSREQSEND: DTLS connection request sent peer_ip: 192.168.1.221 peer_port: 5246
*Sep 20 11:58:21.001: %CAPWAP-5-CHANGED: CAPWAP changed state to
*Sep 20 11:58:22.544: %DTLS-5-ALERT: Received FATAL : Certificate unknown alert from 192.168.1.221
*Sep 20 11:58:22.544: %CAPWAP-3-ERRORLOG: Bad certificate alert received from peer.
*Sep 20 11:58:22.545: %DTLS-5-PEER_DISCONNECT: Peer 192.168.1.221 has closed connection.
*Sep 20 11:58:22.545: %DTLS-5-SEND_ALERT: Send FATAL : Close notify Alert to 192.168.1.221:5246
*Sep 20 11:58:22.546: %CAPWAP-3-ERRORLOG: Invalid event 38 & state 3 combination.
I can ping the WLC from the AP. The traps log on the WLC shows no attempt to connect from AP.
Any suggestions?
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 05:15 AM
Tell the AP the controller to join-
AP#capwap ap controller ip address <WLC IP address>
then show the o/p
AP#sh capwap ip config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 05:19 AM
tried your suggestion and still receiving the same output
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 05:39 AM
checked the regulatory domains, enabled the accept self signed certificate in the AP policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2016 05:42 AM
see the link how t add self signed certificate
http://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wireless-lan-controllers/70341-manual-add-ssc.html
GUI Configuration
Complete these steps from the GUI:
-
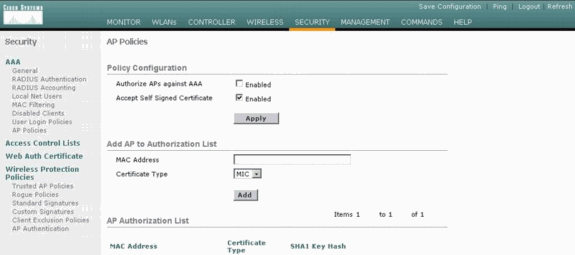
Choose Security > AP Policies and click Enabled beside Accept Self Signed Certificate.
-
Select SSC from the Certificate Type drop-down menu.
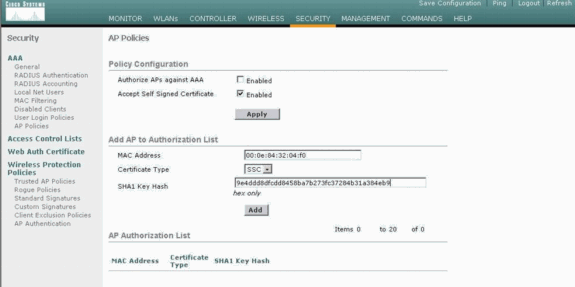
-
Enter the MAC address of the AP and the hash key, and click Add.
CLI Configuration
Complete these steps from the CLI:
-
Enable Accept Self Signed Certificate on the WLC.
The command is config auth-list ap-policy ssc enable.
(Cisco Controller) >config auth-list ap-policy ssc enable
-
Add the AP MAC address and hash key to the authorization list.
The command is config auth-list add ssc AP_MAC AP_key .
(Cisco Controller) >config auth-list add ssc 00:0e:84:32:04:f0 9e4ddd8dfcdd8458ba7b273fc37284b31a384eb9 !--- This command should be on one line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2016 08:34 AM
So the AP is AIR-AP1131AG-N-K9 and my controller was only set to use -A. I have followed the steps to add the -N regulatory domain. The AP still wouldn't connect. I then followed the SSC steps you have kindly included. To obtain the hash key I followed this:
https://supportforums.cisco.com/document/27971/how-recover-hash-key-access-point-and-import-it-controller
However I not able to obtain the hash key. I get this instead on the controller.
*spamApTask5: Sep 22 15:30:43.044: sshpmGetIssuerHandles: Current time outside AP cert validity interval: make sure the controller time is set.
on the AP:
AP0016.c7a0.b6de#sh clock
*15:32:04.858 UTC Thu Sep 22 2016
on the WLC:
(Cisco Controller) >show time
Time............................................. Thu Sep 22 15:32:48 2016
Timezone delta................................... 0:0
Timezone location................................
NTP Servers
NTP Polling Interval......................... 86400
Index NTP Key Index NTP Server NTP Msg Auth Status
------- ----------------------------------------------------------------------------------
1 0 192.168.1.201 AUTH DISABLED
The two devices seem to have the same time. I'm not sure why it would error out with a time issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2016 03:12 PM
What is the serial number of the AP and post the complete output to the WLC command of "sh sysinfo".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2017 02:25 PM
Hello Leo
AP0013.c3de.980a#show version
Cisco IOS Software, C1130 Software (C1130-K9W8-M), Experimental Version 12.4(20150326:115131) [wnbubld 104]
Copyright (c) 1986-2015 by Cisco Systems, Inc.
Compiled Thu 26-Mar-15 04:52 by wnbubld
ROM: Bootstrap program is C1130 boot loader
BOOTLDR: C1130 Boot Loader (C1130-BOOT-M) Version 12.3(2)JA3, RELEASE SOFTWARE (fc2)
AP0013.c3de.980a uptime is 38 minutes
System returned to ROM by power-on
System image file is "flash:/c1130-k9w8-mx.ap_o_v12t_esc.201503260444/c1130-k9w8-mx.a"
32K bytes of flash-simulated non-volatile configuration memory.
Base ethernet MAC Address: 00:13:C3:DE:98:0A
Part Number : 73-8962-07
PCA Assembly Number : 800-24818-06
PCA Revision Number : C0
PCB Serial Number : FOC091735HH
Top Assembly Part Number : 800-25544-01
Top Assembly Serial Number : FCZ0922Q0NV
Top Revision Number : A0
Product/Model Number : AIR-AP1131AG-E-K9
Configuration register is 0xF
(Cisco Controller) >show sysinfo
Manufacturer's Name.............................. Cisco Systems Inc.
Product Name..................................... Cisco Controller
Product Version.................................. 8.0.140.0
RTOS Version..................................... 8.0.140.0
Bootloader Version............................... 8.3.15.96
Emergency Image Version.......................... 8.0.140.0
Build Type....................................... DATA + WPS
System Name...................................... vWLC001
System Location..................................
System Contact...................................
System ObjectID.................................. 1.3.6.1.4.1.9.1.1631
IP Address....................................... 10.0.1.5
IPv6 Address..................................... ::
System Up Time................................... 0 days 0 hrs 57 mins 23 secs
System Timezone Location......................... (GMT +1:00) Amsterdam, Berlin, Rome, Vienna
System Stats Realtime Interval................... 5
System Stats Normal Interval..................... 180
Configured Country............................... BE - Belgium
--More-- or (q)uit
State of 802.11b Network......................... Enabled
State of 802.11a Network......................... Enabled
Number of WLANs.................................. 1
Number of Active Clients......................... 0
Burned-in MAC Address............................ 00:0C:29:40:14:07
Maximum number of APs supported.................. 200
System Nas-Id....................................
WLC MIC Certificate Types........................ SHA1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2016 03:49 PM
Try these:
- Delete the AP from the controller
- Delete the certificate on the flash of the AP if it exists
- Make sure the AP has a correct time.
Some links for you amusement:
https://learningnetwork.cisco.com/thread/80084
http://www.cisco.com/c/en/us/support/docs/wireless/5500-series-wireless-controllers/119286-lap-notjoin-wlc-tshoot.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 06:02 AM
After running into the same type of issue at a different location, I am now attempting to overcome the "LAP/WLC MIC or SSC lifetime expiration causes DTLS failure" CSCuq19142
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCuq19142/?referring_site=bugquickviewredir
At the other location I upgraded the product version to 8.0.140.0, set the date of the WLC to prior to the expired MIC of the downed AP's and all of the ap's updated their code as expected.
However, resetting the WLC to use the correct date and rebooting an AP causes the AP not to join again.
Following:
https://supportforums.cisco.com/document/12453081/lightweight-ap-fail-create-capwaplwapp-connection-due-certificate-expiration
I don't have the commands on my controller so I cannot enable/disable expired certificate checking.
***correction code version 8.0.140.0 does have the command built in and after running it, devices with expired MIC's do connect again.***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2016 06:08 AM
RESOLVED
The steps above resolved the issue which appears to have actually been expired certificates on the AP's.
Unfortunately the option to select "correct answer" is not available on my own comments.??
Thanks everyone that contributed.
Jeremy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 09:35 AM
Hi folks,
Understand this is quite old thread, however I just encountered same problem because of having to use some old spare APs. So just want to share my trick :-)
I was kind of lazy to fix MIC thing, so I temporarily changed the time of controller back to 2012, and immediately these old APs were associated to the controller. Once APs registered, I changed the time back, everything works like charm.
Roger
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide